Communication Theory of Secrecy Systems - Network Research Lab
Communication Theory of Secrecy Systems - Network Research Lab
Communication Theory of Secrecy Systems - Network Research Lab
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
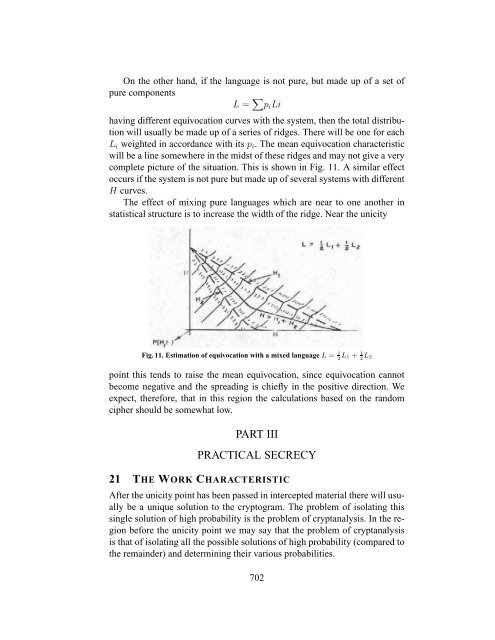
On the other hand, if the language is not pure, but made up <strong>of</strong> a set <strong>of</strong><br />
pure components<br />
L = piLi<br />
having different equivocation curves with the system, then the total distribution<br />
will usually be made up <strong>of</strong> a series <strong>of</strong> ridges. There will be one for each<br />
Li weighted in accordance with its pi. The mean equivocation characteristic<br />
will be a line somewhere in the midst <strong>of</strong> these ridges and may not give a very<br />
complete picture <strong>of</strong> the situation. This is shown in Fig. 11. A similar effect<br />
occurs if the system is not pure but made up <strong>of</strong> several systems with different<br />
H curves.<br />
The effect <strong>of</strong> mixing pure languages which are near to one another in<br />
statistical structure is to increase the width <strong>of</strong> the ridge. Near the unicity<br />
Fig. 11. Estimation <strong>of</strong> equivocation with a mixed language L = 1 1<br />
L1 + 2 2 L2<br />
point this tends to raise the mean equivocation, since equivocation cannot<br />
become negative and the spreading is chiefly in the positive direction. We<br />
expect, therefore, that in this region the calculations based on the random<br />
cipher should be somewhat low.<br />
PART III<br />
PRACTICAL SECRECY<br />
21 THE WORK CHARACTERISTIC<br />
After the unicity point has been passed in intercepted material there will usually<br />
be a unique solution to the cryptogram. The problem <strong>of</strong> isolating this<br />
single solution <strong>of</strong> high probability is the problem <strong>of</strong> cryptanalysis. In the region<br />
before the unicity point we may say that the problem <strong>of</strong> cryptanalysis<br />
is that <strong>of</strong> isolating all the possible solutions <strong>of</strong> high probability (compared to<br />
the remainder) and determining their various probabilities.<br />
702