Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
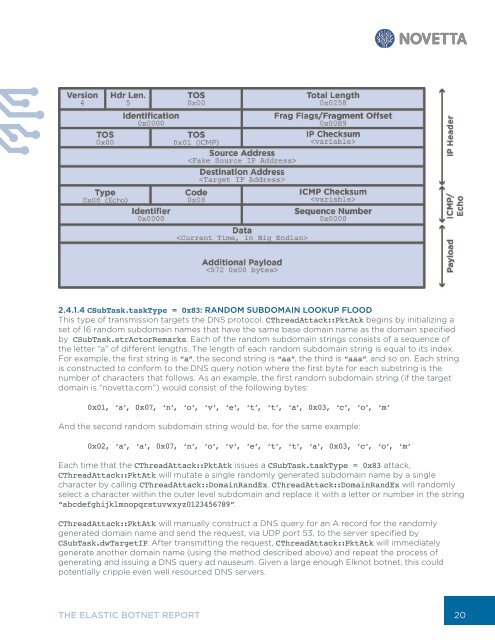
2.4.1.4 CSubTask.taskType = 0x83: RANDOM SUBDOMAIN LOOKUP FLOOD<br />
This type of transmission targets the DNS protocol. CThreadAttack::PktAtk begins by initializing a<br />
set of 16 random subdomain names that have the same base domain name as the domain specified<br />
by CSubTask.strActorRemarks. Each of the random subdomain strings consists of a sequence of<br />
the letter “a” of different lengths. The length of each random subdomain string is equal to its index.<br />
For example, the first string is “a”, the second string is “aa”, the third is “aaa”, and so on. Each string<br />
is constructed to conform to the DNS query notion where the first byte for each substring is the<br />
number of characters that follows. As an example, the first random subdomain string (if the target<br />
domain is “novetta.com”) would consist of the following bytes:<br />
0x01, ‘a’, 0x07, ‘n’, ‘o’, ‘v’, ‘e’, ‘t’, ‘t’, ‘a’, 0x03, ‘c’, ‘o’, ‘m’<br />
And the second random subdomain string would be, for the same example:<br />
0x02, ‘a’, ‘a’, 0x07, ‘n’, ‘o’, ‘v’, ‘e’, ‘t’, ‘t’, ‘a’, 0x03, ‘c’, ‘o’, ‘m’<br />
Each time that the CThreadAttack::PktAtk issues a CSubTask.taskType = 0x83 attack,<br />
CThreadAttack::PktAtk will mutate a single randomly generated subdomain name by a single<br />
character by calling CThreadAttack::DomainRandEx. CThreadAttack::DomainRandEx will randomly<br />
select a character within the outer level subdomain and replace it with a letter or number in the string<br />
“abcdefghijklmnopqrstuvwxyz0123456789”.<br />
CThreadAttack::PktAtk will manually construct a DNS query for an A record for the randomly<br />
generated domain name and send the request, via UDP port 53, to the server specified by<br />
CSubTask.dwTargetIP. After transmitting the request, CThreadAttack::PktAtk will immediately<br />
generate another domain name (using the method described above) and repeat the process of<br />
generating and issuing a DNS query ad nauseum. Given a large enough Elknot botnet, this could<br />
potentially cripple even well resourced DNS servers.<br />
THE ELASTIC BOTNET REPORT<br />
20