Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
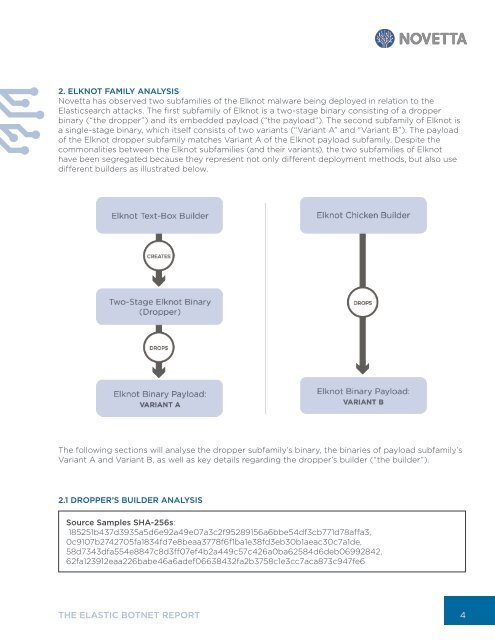
2. ELKNOT FAMILY ANALYSIS<br />
Novetta has observed two subfamilies of the Elknot malware being deployed in relation to the<br />
Elasticsearch attacks. The first subfamily of Elknot is a two-stage binary consisting of a dropper<br />
binary (“the dropper”) and its embedded payload (“the payload”). The second subfamily of Elknot is<br />
a single-stage binary, which itself consists of two variants (“Variant A” and “Variant B”). The payload<br />
of the Elknot dropper subfamily matches Variant A of the Elknot payload subfamily. Despite the<br />
commonalities between the Elknot subfamilies (and their variants), the two subfamilies of Elknot<br />
have been segregated because they represent not only different deployment methods, but also use<br />
different builders as illustrated below.<br />
The following sections will analyse the dropper subfamily’s binary, the binaries of payload subfamily’s<br />
Variant A and Variant B, as well as key details regarding the dropper’s builder (“the builder”).<br />
2.1 DROPPER’S BUILDER ANALYSIS<br />
Source Samples SHA-256s:<br />
185251b437d3935a5d6e92a49e07a3c2f95289156a6bbe54df3cb771d78affa3,<br />
0c9107b2742705fa1834fd7e8beaa3778f6f1ba1e38fd3eb30b1aeac30c7a1de,<br />
58d7343dfa554e8847c8d3ff07ef4b2a449c57c426a0ba62584d6deb06992842,<br />
62fa123912eaa226babe46a6adef06638432fa2b3758c1e3cc7aca873c947fe6<br />
THE ELASTIC BOTNET REPORT<br />
4