Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
3.2.1 BILLGATE’S “NORMAL” DOS ATTACK MODE<br />
The complement to the kernel level DoS attack generator occurs within<br />
CThreadAtkCtrl::DoNormalSubTask. When a task requests a standard (or “normal”) sub-task,<br />
CThreadAtkCtrl::ProcessMain calls CThreadAtkCtrl::DoNormalSubTask which in turn calls<br />
CThreadAtkCtrl::StartNormalSubTask. For each sub-task, a new CThreadNormalAtkExcutor is<br />
generated and executed resulting in CThreadNormalAtkExcutor::ProcessMain being called. Based<br />
on the CSubTask.taskType field, CThreadNormalAtkExecutor::ProcessMain will generate a specific<br />
type of attack object (all of whom are derived from the CPacketAttack base class):<br />
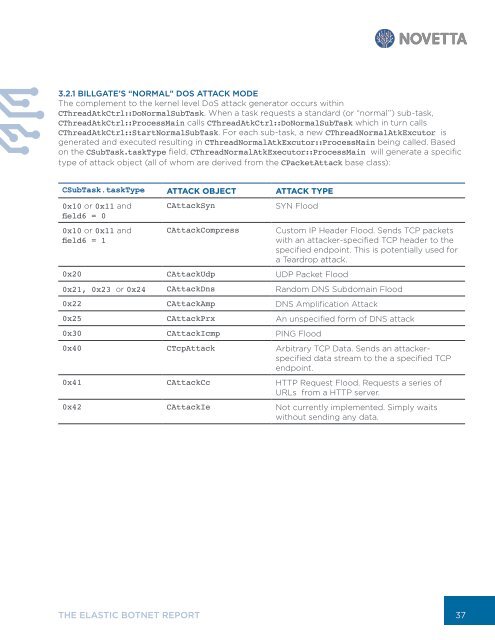
CSubTask.taskType ATTACK OBJECT ATTACK TYPE<br />
0x10 or 0x11 and<br />
field6 = 0<br />
0x10 or 0x11 and<br />
field6 = 1<br />
CAttackSyn<br />
CAttackCompress<br />
SYN Flood<br />
0x20 CAttackUdp UDP Packet Flood<br />
Custom IP Header Flood. Sends TCP packets<br />
with an attacker-specified TCP header to the<br />
specified endpoint. This is potentially used for<br />
a Teardrop attack.<br />
0x21, 0x23 or 0x24 CAttackDns Random DNS Subdomain Flood<br />
0x22 CAttackAmp DNS Amplification Attack<br />
0x25 CAttackPrx An unspecified form of DNS attack<br />
0x30 CAttackIcmp PING Flood<br />
0x40 CTcpAttack Arbitrary TCP Data. Sends an attackerspecified<br />
data stream to the a specified TCP<br />
endpoint.<br />
0x41 CAttackCc HTTP Request Flood. Requests a series of<br />
URLs from a HTTP server.<br />
0x42 CAttackIe Not currently implemented. Simply waits<br />
without sending any data.<br />
THE ELASTIC BOTNET REPORT<br />
37