You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
It is worth noting that, of all of the attack types that Elknot Variant A supports, the random domain<br />
lookup flood attack is the only attack that does not utilize the IP over UDP encapsulation; rather, it<br />
sends the DNS request packet directly to the Internet. Despite only sending a DNS request datagram,<br />
the portion of CThreadAttack::PktAtk that handles the random domain lookup flood attack will<br />
generate a complete, legitimate UDP/IP packet for a DNS query, but will only send the payload<br />
section that contains the DNS request.<br />
2.4.1.5 CSubTask.taskType = 0x84: DNS AMPLIFICATION<br />
CSubTask.taskType = 0x84 attacks generate a UDP/IP packet consistent with the type of packet<br />
found in a DNS amplification attack. Unlike the CSubTask.taskType = 0x83 (Random Domain<br />
Lookup Attack), the packets that the DNS amplification attack generates are encapsulated within a<br />
UDP transport and not sent directly to the Internet for resolution.<br />
NOTE: While variant A’s CThreadAttack::PktAtk does have the functionality to construct the<br />
packets for this particular attack type, the ability for the Elknot C2 server to select this attack type<br />
has been restricted in the Variant A samples that Novetta captured and analyzed. Regardless, this<br />
section will define the packet structure as it would appear on the network if it were accessible.<br />
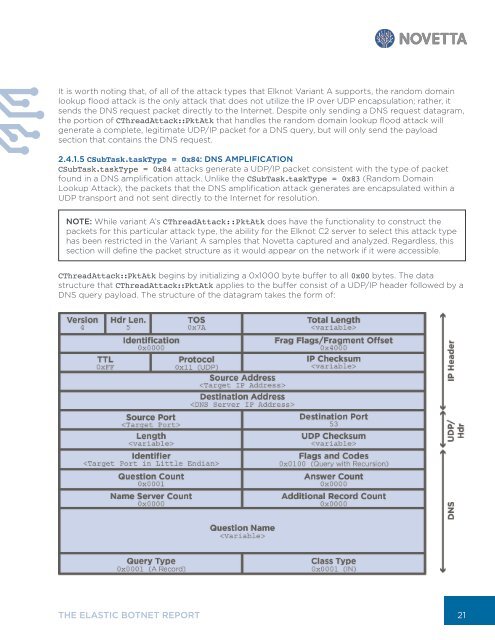
CThreadAttack::PktAtk begins by initializing a 0x1000 byte buffer to all 0x00 bytes. The data<br />
structure that CThreadAttack::PktAtk applies to the buffer consist of a UDP/IP header followed by a<br />
DNS query payload. The structure of the datagram takes the form of:<br />
THE ELASTIC BOTNET REPORT<br />
21