Raytheon Technology Today 2011 Issue 1
Raytheon Technology Today 2011 Issue 1
Raytheon Technology Today 2011 Issue 1
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Model – The assessment serves dual purposes.<br />
First, it drives the development of a<br />
comprehensive approach to improving the<br />
overall security posture of the environment<br />
by applying physical safeguards and process-based<br />
mitigation techniques. Second,<br />
it is used to drive a comprehensive model of<br />
the microgrid or the legacy energy system.<br />
The model generates three products:<br />
• The Baseline Report validates the actual<br />
person-based assessment performed<br />
upon the initial engagement of a customer<br />
and the threats against existing safeguards<br />
to establish a baseline residual risk.<br />
• The Mitigation Report allows customers<br />
to determine where to best apply resources<br />
and capital to achieve the highest<br />
return on investment when attempting to<br />
improve the security posture.<br />
• The What If Report allows the security<br />
analyst to evaluate various scenarios that<br />
are driven by possible new threats identified<br />
through open sources, or based on<br />
how a new safeguard may or may not<br />
help improve the overall residual risk of<br />
the environment.<br />
Protect – <strong>Raytheon</strong>’s protection capability<br />
relies upon the concepts inherent within<br />
traditional command and control systems.<br />
Every asset is monitored for changes from<br />
its established baseline. Any perturbation<br />
results in execution of predefined courses<br />
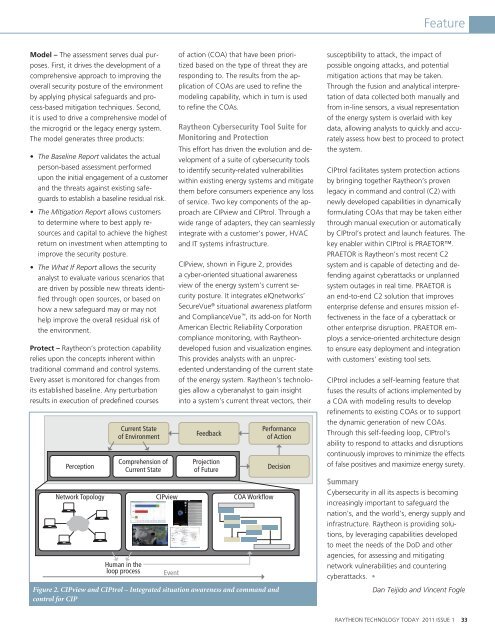
Perception<br />
Network Topology<br />
Current State<br />
of Environment<br />
Comprehension of<br />
Current State<br />
Human in the<br />
loop process Event<br />
of action (COA) that have been prioritized<br />
based on the type of threat they are<br />
responding to. The results from the application<br />
of COAs are used to refine the<br />
modeling capability, which in turn is used<br />
to refine the COAs.<br />
<strong>Raytheon</strong> Cybersecurity Tool Suite for<br />
Monitoring and Protection<br />
This effort has driven the evolution and development<br />
of a suite of cybersecurity tools<br />
to identify security-related vulnerabilities<br />
within existing energy systems and mitigate<br />
them before consumers experience any loss<br />
of service. Two key components of the approach<br />
are CIPview and CIPtrol. Through a<br />
wide range of adapters, they can seamlessly<br />
integrate with a customer’s power, HVAC<br />
and IT systems infrastructure.<br />
CIPview, shown in Figure 2, provides<br />
a cyber-oriented situational awareness<br />
view of the energy system’s current security<br />
posture. It integrates eIQnetworks’<br />
SecureVue ® situational awareness platform<br />
and ComplianceVue , its add-on for North<br />
American Electric Reliability Corporation<br />
compliance monitoring, with <strong>Raytheon</strong>developed<br />
fusion and visualization engines.<br />
This provides analysts with an unprecedented<br />
understanding of the current state<br />
of the energy system. <strong>Raytheon</strong>’s technologies<br />
allow a cyberanalyst to gain insight<br />
into a system’s current threat vectors, their<br />
Feedback<br />
Projection<br />
of Future<br />
CIPview COA Workflow<br />
Figure 2. CIPview and CIPtrol – Integrated situation awareness and command and<br />
control for CIP<br />
Performance<br />
of Action<br />
Decision<br />
Feature<br />
susceptibility to attack, the impact of<br />
possible ongoing attacks, and potential<br />
mitigation actions that may be taken.<br />
Through the fusion and analytical interpretation<br />
of data collected both manually and<br />
from in-line sensors, a visual representation<br />
of the energy system is overlaid with key<br />
data, allowing analysts to quickly and accurately<br />
assess how best to proceed to protect<br />
the system.<br />
CIPtrol facilitates system protection actions<br />
by bringing together <strong>Raytheon</strong>’s proven<br />
legacy in command and control (C2) with<br />
newly developed capabilities in dynamically<br />
formulating COAs that may be taken either<br />
through manual execution or automatically<br />
by CIPtrol’s protect and launch features. The<br />
key enabler within CIPtrol is PRAETOR.<br />
PRAETOR is <strong>Raytheon</strong>’s most recent C2<br />
system and is capable of detecting and defending<br />
against cyberattacks or unplanned<br />
system outages in real time. PRAETOR is<br />
an end-to-end C2 solution that improves<br />
enterprise defense and ensures mission effectiveness<br />
in the face of a cyberattack or<br />
other enterprise disruption. PRAETOR employs<br />
a service-oriented architecture design<br />
to ensure easy deployment and integration<br />
with customers’ existing tool sets.<br />
CIPtrol includes a self-learning feature that<br />
fuses the results of actions implemented by<br />
a COA with modeling results to develop<br />
refinements to existing COAs or to support<br />
the dynamic generation of new COAs.<br />
Through this self-feeding loop, CIPtrol’s<br />
ability to respond to attacks and disruptions<br />
continuously improves to minimize the effects<br />
of false positives and maximize energy surety.<br />
Summary<br />
Cybersecurity in all its aspects is becoming<br />
increasingly important to safeguard the<br />
nation's, and the world’s, energy supply and<br />
infrastructure. <strong>Raytheon</strong> is providing solutions,<br />
by leveraging capabilities developed<br />
to meet the needs of the DoD and other<br />
agencies, for assessing and mitigating<br />
network vulnerabilities and countering<br />
cyberattacks. •<br />
Dan Teijido and Vincent Fogle<br />
RAYTHEON TECHNOLOGY TODAY <strong>2011</strong> ISSUE 1 33