Internet Freedom A Foreign Policy Imperative in the Digital Age
Internet Freedom A Foreign Policy Imperative in the Digital Age
Internet Freedom A Foreign Policy Imperative in the Digital Age
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
J U N E2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>By Richard Fonta<strong>in</strong>e and Will Rogers
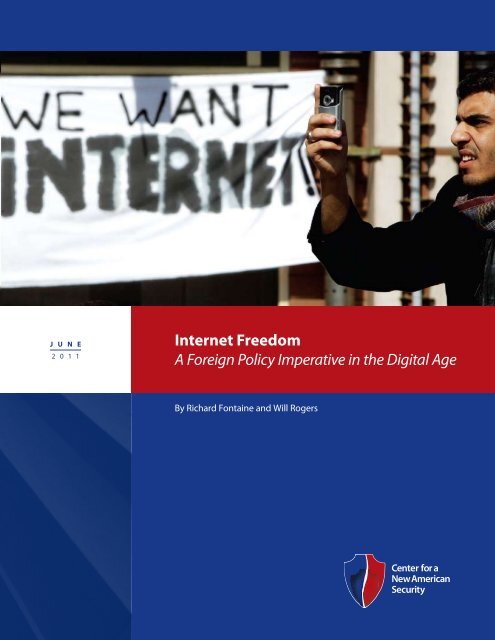
AcknowledgmentsWe express our gratitude to our colleagues at <strong>the</strong> Center for a New American Security (CNAS) for <strong>the</strong>ir assistance with thisstudy. Jackie Koo provided exceptional research assistance throughout <strong>the</strong> writ<strong>in</strong>g process. Krist<strong>in</strong> Lord’s efforts <strong>in</strong> edit<strong>in</strong>gand shap<strong>in</strong>g this report and <strong>the</strong> overall CNAS <strong>Internet</strong> freedom project were <strong>in</strong>valuable. Nora Bensahel devoted significanttime and effort to improv<strong>in</strong>g <strong>the</strong> writ<strong>in</strong>g. Liz Fonta<strong>in</strong>e provided typically excellent design and layout help on a shorttimel<strong>in</strong>e.We owe a great deal of thanks to Ambassador David Gross, who shared his unique <strong>in</strong>sights throughout <strong>the</strong> entirety of thisproject. We also owe a large debt of gratitude to those who reviewed all or part of this paper <strong>in</strong> draft form, <strong>in</strong>clud<strong>in</strong>g KenBerman, Daniel Cal<strong>in</strong>geart, Andrew Lewman, Sarah Labowitz, Marc Lynch, Rebecca MacK<strong>in</strong>non, Jeff Pryce, Ben Scott andseveral anonymous reviewers. We thank <strong>the</strong> Harvard Law School National Security Research Group for its extraord<strong>in</strong>aryhelp <strong>in</strong> research<strong>in</strong>g <strong>the</strong> <strong>in</strong>ternational legal implications of <strong>Internet</strong> freedom. The group, which is directed by Ivana Deyrup,<strong>in</strong>cludes Gracye Cheng, Morgan Cohen, Josh Green, Carlos Oliveira and Mark Stadnyk. F<strong>in</strong>ally, we would like thank <strong>the</strong> manyexperts who patiently spoke with us about <strong>Internet</strong> freedom issues over <strong>the</strong> last year, whe<strong>the</strong>r <strong>in</strong> government, <strong>the</strong> privatesector or academia, here <strong>in</strong> Wash<strong>in</strong>gton, <strong>in</strong> Silicon Valley, or elsewhere.This publication was made possible through <strong>the</strong> support of grants from <strong>the</strong> John Templeton Foundation and <strong>the</strong> MarkleFoundation. The op<strong>in</strong>ions expressed <strong>in</strong> this publication are those of <strong>the</strong> authors and do not necessarily reflect <strong>the</strong> viewsof <strong>the</strong> John Templeton Foundation or <strong>the</strong> Markle Foundation. Readers should note that some organizations that arementioned <strong>in</strong> <strong>the</strong> report or that o<strong>the</strong>rwise have an <strong>in</strong>terest <strong>in</strong> <strong>the</strong> issues discussed here support CNAS f<strong>in</strong>ancially. CNASma<strong>in</strong>ta<strong>in</strong>s a broad and diverse group of more than 100 funders, <strong>in</strong>clud<strong>in</strong>g private foundations, government agencies, corporationsand private <strong>in</strong>dividuals, and reta<strong>in</strong>s sole editorial control over its ideas, projects and products. A complete list of<strong>the</strong> Center’s f<strong>in</strong>ancial supporters can be found on our website at www.cnas.org/support/our-supporters.The authors of this report are solely responsible for <strong>the</strong> analysis and recommendations conta<strong>in</strong>ed here<strong>in</strong>.Cover ImageA man takes pictures with his cell phone on Tahrir, or Liberation Square, <strong>in</strong> Cairoon January 31, 2011.(BEN CURTIS/Associated Press)
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>About <strong>the</strong> AuthorsRichard Fonta<strong>in</strong>e is a Senior Fellow at <strong>the</strong> Center for a New American Security.Will Rogers is a Research Associate at <strong>the</strong> Center for a New American Security.2 |
<strong>Internet</strong> <strong>Freedom</strong>: A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong><strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>By Richard Fonta<strong>in</strong>e and Will Rogers
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>
I. EXECUTIVE SUMMARY America needs a comprehensive <strong>Internet</strong> freedomstrategy, one that tilts <strong>the</strong> balance <strong>in</strong> favor of thosewho would use <strong>the</strong> <strong>Internet</strong> to advance toleranceand free expression, and away from those whowould employ it for repression or violence.By Richard Fonta<strong>in</strong>e and Will RogersThis requires <strong>in</strong>corporat<strong>in</strong>g <strong>Internet</strong> freedom asan <strong>in</strong>tegral element of American foreign policy.As recent events <strong>in</strong> <strong>the</strong> Middle East demonstrate,<strong>the</strong> <strong>Internet</strong> has emerged as a major force <strong>in</strong><strong>in</strong>ternational affairs, one that will have last<strong>in</strong>gimplications for <strong>the</strong> United States and <strong>the</strong> <strong>in</strong>ternationalcommunity. But new communicationstechnologies are a double-edged sword. Theyrepresent both a medium for <strong>in</strong>dividuals to communicate,form groups and freely broadcast <strong>the</strong>irideas around <strong>the</strong> world, and a tool that empowersauthoritarian governments. U.S. policymakersshould better appreciate <strong>the</strong> complex role newcommunications technologies play <strong>in</strong> politicalchange abroad, and how those technologies<strong>in</strong>tersect with <strong>the</strong> array of American foreign policyobjectives.<strong>Internet</strong> freedom typically <strong>in</strong>cludes two dimensions.<strong>Freedom</strong> of <strong>the</strong> <strong>Internet</strong> denotes <strong>the</strong>freedoms of onl<strong>in</strong>e expression, assembly andassociation – <strong>the</strong> extension to cyberspace of rightsthat have been widely recognized to exist outsideit. Promot<strong>in</strong>g freedom of <strong>the</strong> <strong>Internet</strong> merelyexpands to cyberspace a tradition of U.S. diplomaticand f<strong>in</strong>ancial support for human rightsabroad. <strong>Freedom</strong> via <strong>the</strong> <strong>Internet</strong>, <strong>the</strong> notion thatnew communications technologies aid <strong>the</strong> establishmentof democracy and liberal society offl<strong>in</strong>e,is at once more allur<strong>in</strong>g and hotly contested.<strong>Internet</strong> freedom <strong>in</strong> this sense has captured <strong>the</strong>imag<strong>in</strong>ation of many policymakers and expertswho see <strong>in</strong> <strong>the</strong>se technologies a tool for <strong>in</strong>dividualsto help move <strong>the</strong>ir societies away fromauthoritarianism and toward democracy. Though<strong>the</strong> l<strong>in</strong>ks between democracy and <strong>Internet</strong> freedomare <strong>in</strong>direct and complex, nascent evidencesuggests that new communications tools do| 5
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>6 |matter <strong>in</strong> political change, and that both dissidentsand dictators act on that basis.Most attention has focused on technologies thatallow dissidents to penetrate restrictive firewallsand communicate securely. But fund<strong>in</strong>g technologycomprises just one aspect of America’s<strong>Internet</strong> freedom agenda. The United States alsoadvocates <strong>in</strong>ternational norms regard<strong>in</strong>g freedomof speech and onl<strong>in</strong>e assembly and opposesattempts by autocratic governments to restrictlegitimate onl<strong>in</strong>e activity.The private sector has a critical role to play <strong>in</strong>promot<strong>in</strong>g <strong>Internet</strong> freedom, but, given corporate<strong>in</strong>terests <strong>in</strong> maximiz<strong>in</strong>g profits ra<strong>the</strong>r thanpromot<strong>in</strong>g onl<strong>in</strong>e freedom <strong>in</strong> repressive environments,efforts to expand its role are difficult.Ethical debates, rang<strong>in</strong>g from whe<strong>the</strong>r Americancompanies should be permitted to sell repressiveregimes key technologies to <strong>the</strong> responsibilitiesof corporations <strong>in</strong> <strong>the</strong> face of an autocracies’demand for <strong>in</strong>formation, rema<strong>in</strong> unresolved. And<strong>the</strong> o<strong>the</strong>r side of this co<strong>in</strong> – whe<strong>the</strong>r U.S. exportcontrols should prohibit sell<strong>in</strong>g technologies thatcould be used to promote onl<strong>in</strong>e freedom – isoften overlooked.To date, <strong>the</strong> U.S. government has shied awayfrom articulat<strong>in</strong>g fully <strong>the</strong> motivations beh<strong>in</strong>d its<strong>Internet</strong> freedom agenda. Adm<strong>in</strong>istration officialsemphasize that <strong>the</strong>ir policy supports freedom of<strong>the</strong> <strong>Internet</strong>, not freedom via <strong>the</strong> <strong>Internet</strong>, andthat <strong>the</strong> <strong>Internet</strong> freedom agenda is not part of abroader strategy to support democratic evolution.It should be.Admittedly, promot<strong>in</strong>g <strong>Internet</strong> freedom is complicated,and <strong>in</strong>volves <strong>in</strong>herent tensions witho<strong>the</strong>r U.S. foreign policy, economic and nationalsecurity <strong>in</strong>terests. This is particularly true <strong>in</strong> <strong>the</strong>area of cyber security. Cyber security expertsseek to secure <strong>the</strong> United States aga<strong>in</strong>st cyberattacks, for example, by push<strong>in</strong>g for greater onl<strong>in</strong>etransparency and attribution, while <strong>Internet</strong>freedom proponents urge greater onl<strong>in</strong>e anonymity.While tensions between <strong>Internet</strong> freedom andcyber security are real, and <strong>in</strong> some cases will forcedifficult choices, <strong>the</strong>y should not prevent robustU.S. efforts to advance both.A robust <strong>Internet</strong> freedom agenda should reflect<strong>the</strong> follow<strong>in</strong>g eight pr<strong>in</strong>ciples:Pr<strong>in</strong>ciple 1: Embrace a ComprehensiveApproachU.S. policymakers should <strong>in</strong>corporate <strong>Internet</strong>freedom <strong>in</strong>to <strong>the</strong>ir decision-mak<strong>in</strong>g (especiallyon cyber security and economic diplomacyissues); convene private sector professionals,export controls experts, diplomats and o<strong>the</strong>rs toexplore new ways of promot<strong>in</strong>g <strong>Internet</strong> freedom;and use traditional diplomacy to promote<strong>Internet</strong> freedom.Pr<strong>in</strong>ciple 2: Build an International Coalitionto Promote <strong>Internet</strong> <strong>Freedom</strong>The U.S. government should convene a core groupof democratic governments to advocate <strong>Internet</strong>freedom <strong>in</strong> key <strong>in</strong>ternational fora; urge governmentsto encourage foreign companies to jo<strong>in</strong> <strong>the</strong>Global Network Initiative (GNI); and ensure that<strong>the</strong> Secretary of State gives her next major addresson <strong>Internet</strong> freedom <strong>in</strong> a foreign country, possibly<strong>in</strong> Europe alongside key European Union (EU)commissioners.Pr<strong>in</strong>ciple 3: Move Beyond CircumventionTechnologiesThe U.S. government should cont<strong>in</strong>ue to fundtechnologies o<strong>the</strong>r than firewall-evasion tools,<strong>in</strong>clud<strong>in</strong>g those that help dissidents ma<strong>in</strong>ta<strong>in</strong>digital security, ensure mobile access and reconstitutewebsites after a cyber attack. The U.S.government should offer f<strong>in</strong>ancial awards to fostertechnological <strong>in</strong>novation, require that any onl<strong>in</strong>etool receiv<strong>in</strong>g U.S. fund<strong>in</strong>g be subjected to an<strong>in</strong>dependent security audit and expand <strong>the</strong> sources
of technology fund<strong>in</strong>g to <strong>in</strong>clude foreign governments,foundations and <strong>the</strong> private sector.Pr<strong>in</strong>ciple 4: Prioritize Tra<strong>in</strong><strong>in</strong>gThe State Department, along with <strong>the</strong> U.S. <strong>Age</strong>ncyfor International Development (USAID), shouldcont<strong>in</strong>ue to foster <strong>Internet</strong> freedom through targetedtra<strong>in</strong><strong>in</strong>g programs, <strong>in</strong>clud<strong>in</strong>g education ononl<strong>in</strong>e safety.Pr<strong>in</strong>ciple 5: Lead <strong>the</strong> Effort to BuildInternational NormsThe U.S. government should promote a liberalconcept of <strong>Internet</strong> freedom <strong>in</strong> all relevant fora,and reject attempts by authoritarian states to promotenorms that restrict freedoms of <strong>in</strong>formationand expression onl<strong>in</strong>e. It should also pursue an<strong>in</strong>ternational transparency <strong>in</strong>itiative to encouragegovernments to publicize <strong>the</strong>ir policies on restrict<strong>in</strong>gonl<strong>in</strong>e <strong>in</strong>formation.Pr<strong>in</strong>ciple 8: Reform Export ControlsThe U.S. government should relax controls on technologiesthat would permit greater onl<strong>in</strong>e freedomwhile protect<strong>in</strong>g American national security, andeducate companies on <strong>the</strong> precise nature of exportcontrol restrictions so that companies do not overcomplyand deny legal technologies to dissidentsabroad.In addition, we offer several recommendationsfor technology companies, <strong>in</strong>clud<strong>in</strong>g provid<strong>in</strong>gdissidents basic technical assistance to better usebuilt-<strong>in</strong> security functions for software and hardware;better <strong>in</strong>form<strong>in</strong>g users and <strong>the</strong> public aboutwho may access <strong>the</strong> data <strong>the</strong>y control and underwhat conditions; <strong>in</strong>creas<strong>in</strong>g corporate transparencyabout foreign government requests; and advocat<strong>in</strong>gfor <strong>in</strong>creased <strong>Internet</strong> freedom.Pr<strong>in</strong>ciple 6: Create Economic Incentivesto Support <strong>Internet</strong> <strong>Freedom</strong>U.S. officials should cont<strong>in</strong>ue to articulate <strong>the</strong>economic case for <strong>Internet</strong> freedom, backed whereverpossible by solid quantitative evidence, andpush for <strong>Internet</strong> censorship to be recognized as atrade barrier.Pr<strong>in</strong>ciple 7: Streng<strong>the</strong>n <strong>the</strong> Private Sector’sRole <strong>in</strong> Support<strong>in</strong>g <strong>Internet</strong> <strong>Freedom</strong>Congress should adopt laws that prohibitAmerican corporations from giv<strong>in</strong>g autocraticgovernments <strong>the</strong> private data of dissidents when<strong>the</strong> request is clearly <strong>in</strong>tended to quash legitimatefreedom of expression, and that requirecompanies to periodically disclose requests itreceives for such data to <strong>the</strong> U.S. government.U.S. officials should cont<strong>in</strong>ue to urge companiesto jo<strong>in</strong> <strong>the</strong> GNI, but also encourage <strong>the</strong>mto develop broad unilateral codes of conductconsistent with <strong>the</strong> GNI. They should also publiclyhighlight specific bus<strong>in</strong>ess practices, bothpositive and negative.| 7
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>8 |II. IntroductionThe world’s population is more connected, withmore access to new <strong>in</strong>formation and ideas thanever before. Today, 2 billion people have access to<strong>the</strong> <strong>Internet</strong>. Five billion people use mobile phones,many of <strong>the</strong>m smartphones with <strong>Internet</strong> access. 1The <strong>Internet</strong> has also become an extension of civilsociety. 2 <strong>Digital</strong> tools are <strong>in</strong>creas<strong>in</strong>gly used to communicateacross borders, organize protests, launchcyber attacks, build transnational coalitions,topple some dictators and possibly streng<strong>the</strong>no<strong>the</strong>rs – actions that all affect U.S. foreign policy.But American policymakers have just begun to<strong>in</strong>corporate <strong>the</strong> <strong>Internet</strong>’s role <strong>in</strong>to <strong>the</strong>ir broaderconceptions of U.S. foreign policy.Thus far, <strong>the</strong> discussion among advocates andforeign policy practitioners has revolved around“<strong>Internet</strong> freedom,” a broad rubric that encompassesonl<strong>in</strong>e freedoms, <strong>in</strong>clud<strong>in</strong>g <strong>the</strong> rights of expressionand onl<strong>in</strong>e organization, and <strong>the</strong> potentially transformativeand hotly contested role of <strong>the</strong> <strong>Internet</strong><strong>in</strong> promot<strong>in</strong>g democratization. The U.S. governmentnow has an <strong>Internet</strong> freedom agenda, withtens of millions of dollars to implement it. Both<strong>the</strong> Senate and <strong>the</strong> House of Representatives boastglobal <strong>Internet</strong> freedom caucuses. The Secretary ofState has given two major addresses articulat<strong>in</strong>gpr<strong>in</strong>ciples and policies for <strong>Internet</strong> freedom, andnewspapers and periodicals have repeatedly po<strong>in</strong>tedto <strong>the</strong> use of onl<strong>in</strong>e tools both for popular protestand as a means of repression. In <strong>the</strong> midst of <strong>the</strong>2011 Arab Spr<strong>in</strong>g, President Obama went so far asto describe <strong>the</strong> ability to use social network<strong>in</strong>g as a“core value” that Americans believe is “universal.” 3The debate over whe<strong>the</strong>r and how to promote<strong>Internet</strong> freedom has been an emotional one, with“cyber utopians” prais<strong>in</strong>g <strong>the</strong> <strong>Internet</strong> as a s<strong>in</strong>gulartool for toppl<strong>in</strong>g dictators, and “cyber pessimists”not<strong>in</strong>g all <strong>the</strong> ways that autocracies use new communicationstools to streng<strong>the</strong>n <strong>the</strong>ir own rule.This report seeks to move beyond <strong>the</strong>se two polesby identify<strong>in</strong>g <strong>the</strong> nuances and tradeoffs <strong>in</strong>volved<strong>in</strong> promot<strong>in</strong>g onl<strong>in</strong>e freedom.This study focuses on <strong>the</strong> <strong>Internet</strong>, <strong>in</strong>clud<strong>in</strong>gWeb-based communication platforms such asblogs, social network<strong>in</strong>g and o<strong>the</strong>r photo- andvideo-shar<strong>in</strong>g websites, and proposes an <strong>in</strong>tegrated<strong>Internet</strong> freedom strategy that balancescompet<strong>in</strong>g U.S. <strong>in</strong>terests. 4 We beg<strong>in</strong> by def<strong>in</strong><strong>in</strong>g<strong>Internet</strong> freedom, dist<strong>in</strong>guish<strong>in</strong>g between freedomof <strong>the</strong> <strong>Internet</strong> and freedom via <strong>the</strong> <strong>Internet</strong>, andexam<strong>in</strong>e why <strong>the</strong> United States has an <strong>in</strong>terest<strong>in</strong> preserv<strong>in</strong>g an open <strong>Internet</strong>. We <strong>the</strong>n exploreways <strong>in</strong> which <strong>the</strong> <strong>Internet</strong> can be used both fordemocratic political change and as a tool of repression.We argue that <strong>the</strong> United States shouldactively promote <strong>Internet</strong> freedom, given not onlyits potential to aid those seek<strong>in</strong>g liberal politicalchange, but also because do<strong>in</strong>g so accords withAmerica’s deepest values. We exam<strong>in</strong>e <strong>the</strong> U.S.government’s current efforts to promote <strong>Internet</strong>freedom abroad and <strong>the</strong> tensions between <strong>the</strong>seefforts and enhanc<strong>in</strong>g cyber security. F<strong>in</strong>ally, weprovide a set of <strong>in</strong>terlock<strong>in</strong>g pr<strong>in</strong>ciples that, takentoge<strong>the</strong>r, will <strong>in</strong>corporate <strong>Internet</strong> freedom <strong>in</strong>toAmerican foreign policy.The paper assumes that <strong>the</strong> United States has an<strong>in</strong>terest <strong>in</strong> support<strong>in</strong>g human rights and democracyabroad. There is a cont<strong>in</strong>ued healthy debateabout this po<strong>in</strong>t and it is far from America’s only<strong>in</strong>terest. But successive adm<strong>in</strong>istrations (<strong>in</strong>clud<strong>in</strong>gthose of Presidents Cl<strong>in</strong>ton, Bush and Obama) havemade promot<strong>in</strong>g democracy an explicit objectiveof U.S. policy. While <strong>the</strong> United States should berealistic and modest about what it can achieve,to <strong>the</strong> extent that a freer onl<strong>in</strong>e space facilitates afreer offl<strong>in</strong>e space, <strong>the</strong> United States should support<strong>Internet</strong> freedom. At its heart, an American<strong>Internet</strong> freedom agenda should actively aim to tilt<strong>the</strong> balance <strong>in</strong> favor of those who would use <strong>the</strong><strong>Internet</strong> to advance tolerance and free expression,and away from those who would use it for repressionor violence.
This paper also acknowledges <strong>the</strong> downsides of<strong>the</strong> <strong>Internet</strong>. An autocratic regime can use <strong>the</strong><strong>Internet</strong> to streng<strong>the</strong>n its ability to monitor itscitizens and control <strong>the</strong>ir behavior. Terrorists canuse it to communicate and spread propaganda.Crim<strong>in</strong>als can use new technologies to organizeillicit activities. Dissidents can use <strong>the</strong> <strong>Internet</strong>to spread <strong>the</strong>ir message, but so can extremistsadvocat<strong>in</strong>g violence. There is no certa<strong>in</strong> outcometo this cont<strong>in</strong>ual push and pull, and <strong>the</strong> localpolitical context matters enormously.At its heart, an American<strong>Internet</strong> freedom agendashould actively aim to tilt<strong>the</strong> balance <strong>in</strong> favor of thosewho would use <strong>the</strong> <strong>Internet</strong>to advance tolerance and freeexpression, and away fromthose who would use it forrepression or violence.This report exam<strong>in</strong>es <strong>Internet</strong> freedom through<strong>the</strong> lens of American foreign policy and explorestwo central questions: What does access to an open<strong>Internet</strong> mean for U.S. foreign policy, and whatshould <strong>the</strong> United States do about it? Our <strong>in</strong>tendedaudience is not merely those <strong>in</strong>dividuals <strong>in</strong>timatelyfamiliar with <strong>Internet</strong> freedom issues, but also thoseforeign policy actors and th<strong>in</strong>kers who should be.As we discuss below, <strong>Internet</strong> freedom means manyth<strong>in</strong>gs to many people, and to some it suggests afocus on domestic policy – net neutrality, antitrustlaw, <strong>the</strong> role of <strong>the</strong> Federal CommunicationsCommission, and so on. Except where such domesticconcerns impact <strong>Internet</strong> freedom promotionefforts abroad (as we argue <strong>the</strong>y may), such issuesare beyond <strong>the</strong> ambit of this paper.The Center for a New American Security (CNAS)<strong>in</strong>itiated this project <strong>in</strong> March 2010 when it hosted<strong>the</strong> launch of <strong>the</strong> Senate Global <strong>Internet</strong> <strong>Freedom</strong>Caucus. Over <strong>the</strong> course of more than a year,CNAS <strong>the</strong>n convened a number of work<strong>in</strong>g groupson <strong>the</strong> role of <strong>the</strong> private sector, <strong>the</strong> prospects for<strong>in</strong>ternational normative agreements, <strong>the</strong> role of circumventiontechnology and <strong>the</strong> tensions betweencyber security and <strong>Internet</strong> freedom. In addition,we consulted with representatives <strong>in</strong> government,<strong>the</strong> corporate world, <strong>the</strong> nonprofit sector, technologyfirms and academia. The study was conductedalongside CNAS’ companion project on cybersecurity. 5What is <strong>Internet</strong> <strong>Freedom</strong>?<strong>Internet</strong> freedom, broadly def<strong>in</strong>ed, is <strong>the</strong> notionthat universal rights, <strong>in</strong>clud<strong>in</strong>g <strong>the</strong> freedoms ofexpression, assembly and association, extend to<strong>the</strong> digital sphere. Yet policymakers and o<strong>the</strong>rsoften def<strong>in</strong>e <strong>Internet</strong> freedom differently. It isthus useful to differentiate, as a number of experts<strong>in</strong>creas<strong>in</strong>gly have, between two l<strong>in</strong>ked but dist<strong>in</strong>ctconcepts: freedom of <strong>the</strong> <strong>Internet</strong> and freedom via<strong>the</strong> <strong>Internet</strong>.<strong>Freedom</strong> of <strong>the</strong> <strong>Internet</strong> refers to <strong>the</strong> ability toengage <strong>in</strong> unfettered expression <strong>in</strong> cyberspace.This vision of <strong>Internet</strong> freedom, as scholar EvgenyMorozov po<strong>in</strong>ts out <strong>in</strong> his book The Net Delusion,represents freedom from someth<strong>in</strong>g: censorship,government surveillance, distributed denial ofservice (DDoS) attacks, and so on. 6 The pr<strong>in</strong>ciplesundergird<strong>in</strong>g freedom of <strong>the</strong> <strong>Internet</strong> arearticulated <strong>in</strong> documents such as <strong>the</strong> UniversalDeclaration of Human Rights (UDHR), whichdescribes as <strong>in</strong>alienable <strong>the</strong> right to receive andimpart <strong>in</strong>formation without <strong>in</strong>terference. 7 In thissense, <strong>Internet</strong> freedom is little different from <strong>the</strong>| 9
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>10 |notion of free expression, whose advocacy hasbeen an element of U.S. foreign policy for decades.After all, American ambassadors have long pressedforeign governments to allow a free press, releasejailed journalists and cease jamm<strong>in</strong>g unwantedbroadcasts.<strong>Freedom</strong> via <strong>the</strong> <strong>Internet</strong> is at once both a moreallur<strong>in</strong>g and complicated idea. Its advocates suggestthat more onl<strong>in</strong>e freedom can lead to moreoffl<strong>in</strong>e freedom; that is, <strong>the</strong> free flow of ideas over<strong>the</strong> <strong>Internet</strong> promotes democratization. <strong>Freedom</strong>via <strong>the</strong> <strong>Internet</strong> has captured <strong>the</strong> imag<strong>in</strong>ationof many <strong>in</strong> Congress, <strong>the</strong> media and elsewhere(<strong>in</strong>clud<strong>in</strong>g dissidents and dictators) who havewitnessed <strong>the</strong> <strong>Internet</strong>’s seem<strong>in</strong>gly transformativeeffects on autocratic governments. Protesters,democratic activists and average citizens are<strong>in</strong>creas<strong>in</strong>gly us<strong>in</strong>g Facebook, Twitter and o<strong>the</strong>rapplications to communicate and organize – mostrecently <strong>in</strong> Tunisia and Egypt, but <strong>in</strong> o<strong>the</strong>r countriesas well.<strong>Internet</strong> <strong>Freedom</strong> and U.S. National InterestsThe United States has a long history of provid<strong>in</strong>gdiplomatic and f<strong>in</strong>ancial support for <strong>the</strong> promotionof human rights abroad, <strong>in</strong>clud<strong>in</strong>g <strong>the</strong> right to freeexpression. While each presidential adm<strong>in</strong>istrationemphasizes human rights to differ<strong>in</strong>g degrees,dur<strong>in</strong>g recent decades <strong>the</strong>y have all consistentlyheld that human rights are a key U.S. <strong>in</strong>terest.Promot<strong>in</strong>g freedom of <strong>the</strong> <strong>Internet</strong> expands humanrights support <strong>in</strong>to cyberspace, an environment<strong>in</strong> which an ever-greater proportion of humanactivity takes place. The United States advocatesfor freedom of <strong>the</strong> <strong>Internet</strong> because it accords notonly with American values, but also with rightsAmerica believes are <strong>in</strong>tr<strong>in</strong>sic to all humanity.For years, <strong>the</strong> U.S. government has programmaticallyand rhetorically supported democracypromotion abroad. The State Department rout<strong>in</strong>elydisburses millions of dollars <strong>in</strong> fund<strong>in</strong>g fordemocracy-build<strong>in</strong>g programs around <strong>the</strong> world,many of which are aimed explicitly at expand<strong>in</strong>gfree expression. Presidential and o<strong>the</strong>r speechesregularly refer to <strong>the</strong> American belief <strong>in</strong> <strong>the</strong> universalityof this right; to cite but one example, aMarch 2011 White House statement on Syria notedthat, “The United States stands for a set of universalrights, <strong>in</strong>clud<strong>in</strong>g <strong>the</strong> freedom of expression andpeaceful assembly.” 8 The Obama adm<strong>in</strong>istration’s2010 National Security Strategy specifically calledfor marshal<strong>in</strong>g <strong>the</strong> <strong>Internet</strong> and o<strong>the</strong>r <strong>in</strong>formationtechnologies to support freedom of expressionabroad, 9 and <strong>the</strong> Bush adm<strong>in</strong>istration adopted apolicy of maximiz<strong>in</strong>g access to <strong>in</strong>formation andideas over <strong>the</strong> <strong>Internet</strong>. 10America’s <strong>in</strong>terest <strong>in</strong> promot<strong>in</strong>g freedom via<strong>the</strong> <strong>Internet</strong> comes from <strong>the</strong> same fundamentalbelief <strong>in</strong> democratic values and human rights.Despite <strong>in</strong>evitable <strong>in</strong>consistencies and difficulttradeoffs, <strong>the</strong> United States cont<strong>in</strong>ues to supportdemocracy. The Bush adm<strong>in</strong>istration’s 2006National Security Strategy committed to supportdemocratic <strong>in</strong>stitutions abroad through transformationaldiplomacy. 11 President Obama, afterenter<strong>in</strong>g office with an evident desire to move awayfrom <strong>the</strong> sweep<strong>in</strong>g tone of his predecessor’s “freedomagenda,” never<strong>the</strong>less told <strong>the</strong> U.N. GeneralAssembly <strong>in</strong> 2009 that “<strong>the</strong>re are basic pr<strong>in</strong>ciplesthat are universal; <strong>the</strong>re are certa<strong>in</strong> truths whichare self-evident – and <strong>the</strong> United States of Americawill never waver <strong>in</strong> our efforts to stand up for <strong>the</strong>right of people everywhere to determ<strong>in</strong>e <strong>the</strong>ir owndest<strong>in</strong>y.” 12To <strong>the</strong> extent that support<strong>in</strong>g <strong>Internet</strong> freedomadvances America’s democracy-promotion agenda,<strong>the</strong> rationale for promot<strong>in</strong>g onl<strong>in</strong>e freedom is clear.However, cause and effect are not perfectly clear and<strong>the</strong> United States must choose its policies under conditionsof uncerta<strong>in</strong>ty. Both <strong>the</strong> Bush and Obamaadm<strong>in</strong>istrations have wagered that by promot<strong>in</strong>gglobal <strong>Internet</strong> freedom <strong>the</strong> United States will notonly operate accord<strong>in</strong>g to universal values but willpromote tools that may, on balance, benefit societies
over <strong>the</strong> autocrats that oppress <strong>the</strong>m. Secretary ofState Hillary Rodham Cl<strong>in</strong>ton urged countries to“jo<strong>in</strong> us <strong>in</strong> <strong>the</strong> bet we have made, a bet that an open<strong>Internet</strong> will lead to stronger, more prosperouscountries.” 13 Given <strong>the</strong> evidence we discuss throughoutthis report, this bet is one worth mak<strong>in</strong>g.Yet promot<strong>in</strong>g <strong>Internet</strong> freedom <strong>in</strong>evitablyrequires <strong>the</strong> U.S. government to make tradeoffswith o<strong>the</strong>r national security and economic <strong>in</strong>terests– a perennial challenge for a governmentpursu<strong>in</strong>g compet<strong>in</strong>g priorities. After all, it iseasier to support <strong>Internet</strong> freedom <strong>in</strong> countries<strong>in</strong> which <strong>the</strong> United States discerns few overarch<strong>in</strong>gstrategic and economic <strong>in</strong>terests than <strong>in</strong>countries where <strong>the</strong> United States has a robustand complex agenda.Consider Ch<strong>in</strong>a, for example. Ch<strong>in</strong>a engages <strong>in</strong>widespread <strong>Internet</strong> repression and hosts <strong>the</strong>world’s largest population of onl<strong>in</strong>e users. Butpromot<strong>in</strong>g <strong>Internet</strong> freedom <strong>the</strong>re complicatesAmerican efforts to w<strong>in</strong> Beij<strong>in</strong>g’s support on anarray of o<strong>the</strong>r issues, rang<strong>in</strong>g from North Koreato Iran. And streng<strong>the</strong>n<strong>in</strong>g controls over <strong>the</strong> saleof American technologies to Ch<strong>in</strong>a could meanshutt<strong>in</strong>g U.S. companies out of <strong>the</strong> world’s largest<strong>Internet</strong> market at a time when <strong>the</strong> Americaneconomy is still recover<strong>in</strong>g from <strong>the</strong> recentf<strong>in</strong>ancial crisis.The United States should promote <strong>Internet</strong> freedomabroad, but this policy does <strong>in</strong>cur costs.Fund<strong>in</strong>g for <strong>Internet</strong> freedom programs usesscarce dollars. The <strong>Internet</strong> can empower violentradicals as well as peaceful reformers. There is noguarantee that support<strong>in</strong>g <strong>Internet</strong> freedom willenhance freedom or lead to greater democracy. Yetit is virtually certa<strong>in</strong> that if <strong>the</strong> United States ceasesits <strong>Internet</strong> freedom-related activities, <strong>the</strong> balanceof onl<strong>in</strong>e power would shift toward autocraciesseek<strong>in</strong>g to restrict <strong>the</strong>ir populations’ freedom. Thisalone should compel American officials to take<strong>Internet</strong> freedom seriously.A Brief History of <strong>the</strong> U.S. Government’s<strong>Internet</strong> <strong>Freedom</strong> EffortsThe U.S. government started pursu<strong>in</strong>g an <strong>Internet</strong>freedom agenda dur<strong>in</strong>g <strong>the</strong> second term of <strong>the</strong>George W. Bush adm<strong>in</strong>istration. Congress beganscrut<strong>in</strong>iz<strong>in</strong>g <strong>Internet</strong> freedom issues <strong>in</strong> 2005,focus<strong>in</strong>g particularly on <strong>the</strong> private sector. Reportsthat a local Yahoo affiliate gave <strong>the</strong> email recordsof a journalist to Ch<strong>in</strong>ese authorities, which ledto his 10-year prison sentence, prompted congressionalhear<strong>in</strong>gs that also <strong>in</strong>cluded Microsoft andGoogle. 14 The same year, Congressman ChrisSmith, R-N.J., <strong>in</strong>troduced <strong>the</strong> first version of hisGlobal <strong>Internet</strong> <strong>Freedom</strong> Act, which would prohibitexport<strong>in</strong>g certa<strong>in</strong> hardware and software torepressive regimes. 15 In 2008, representatives fromCisco Systems, Inc. were asked to appear before<strong>the</strong> Senate Judiciary Committee to determ<strong>in</strong>e if<strong>the</strong> company know<strong>in</strong>gly sold routers to Ch<strong>in</strong>a for<strong>the</strong> purpose of controll<strong>in</strong>g political dissent andstreng<strong>the</strong>n<strong>in</strong>g <strong>the</strong> state’s Great Firewall. 16 TheYahoo <strong>in</strong>cident, toge<strong>the</strong>r with Cisco’s sales andGoogle’s agreement to censor its search results <strong>in</strong>Ch<strong>in</strong>a, generated a larger discussion on CapitolHill about whe<strong>the</strong>r <strong>the</strong> government should prohibitAmerican technology companies from respond<strong>in</strong>gto politically motivated <strong>in</strong>formation requestsor sell<strong>in</strong>g technology that could help governmentscommit human rights violations. After <strong>the</strong> socalledTwitter revolution <strong>in</strong> Iran <strong>in</strong> 2009, Congresspassed <strong>the</strong> Victims of Iranian Censorship (VOICE)Act, which authorized (but did not appropriate) 55million dollars for State Department programs thatwould help <strong>the</strong> Iranian people overcome electroniccensorship and digital oppression. 17The executive branch has also been <strong>in</strong>creas<strong>in</strong>glyactive. In February 2006, <strong>the</strong>n-Secretary of StateCondoleezza Rice established <strong>the</strong> Global <strong>Internet</strong><strong>Freedom</strong> Task Force (GIFT) as a way to coord<strong>in</strong>ateState Department efforts to promote <strong>Internet</strong>freedom and respond to <strong>Internet</strong> censorship. 18Soon <strong>the</strong>reafter, <strong>the</strong>n-Under Secretary of State for| 11
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>12 |Democracy and Global Affairs Paula Dobrianskyannounced that <strong>the</strong> State Department would henceforth<strong>in</strong>clude a country-level assessment of <strong>Internet</strong>freedom <strong>in</strong> its annual human rights reports.Like its predecessor, <strong>the</strong> Obama adm<strong>in</strong>istration’s<strong>Internet</strong> freedom agenda goes well beyond fund<strong>in</strong>gfirewall-evad<strong>in</strong>g technology. The State Departmenthas bolstered its capacity to use its diplomatic,economic and technological resources to promotea free <strong>Internet</strong>. Cl<strong>in</strong>ton has established a team ofexperts, <strong>in</strong>clud<strong>in</strong>g a senior advisor for <strong>in</strong>novation,to develop creative ways to blend technology withtraditional diplomatic and development efforts.In addition, <strong>the</strong> State Department re-launched its<strong>Internet</strong> freedom task force <strong>in</strong> 2010, rebrand<strong>in</strong>git <strong>the</strong> “Net<strong>Freedom</strong>” Taskforce, and established aCoord<strong>in</strong>ator for Cyber Issues <strong>in</strong> early 2011. TheWhite House established a deputy chief technologyofficer for <strong>Internet</strong> policy with<strong>in</strong> <strong>the</strong> Office ofScience and Technology <strong>Policy</strong> (OSTP) to coord<strong>in</strong>ategovernment-wide <strong>Internet</strong> and technologypolicy, <strong>in</strong>clud<strong>in</strong>g issues related to cyber securityand <strong>Internet</strong> freedom.Cl<strong>in</strong>ton has led efforts to promote <strong>Internet</strong> freedom<strong>in</strong> <strong>the</strong> Obama adm<strong>in</strong>istration. Evok<strong>in</strong>g PresidentFrankl<strong>in</strong> Delano Roosevelt’s 1941 Four <strong>Freedom</strong>sspeech, <strong>in</strong> 2010 Cl<strong>in</strong>ton added a fifth, <strong>the</strong> “freedomto connect – <strong>the</strong> idea that governments should notprevent people from connect<strong>in</strong>g to <strong>the</strong> <strong>Internet</strong>, towebsites or to each o<strong>the</strong>r.” 19 In a second speech ayear later, she pledged America’s “global commitmentto <strong>Internet</strong> freedom, to protect human rightsonl<strong>in</strong>e as we do offl<strong>in</strong>e,” <strong>in</strong>clud<strong>in</strong>g <strong>the</strong> freedoms ofexpression, assembly and association. 20These speeches represent <strong>the</strong> clearest and mostcomplete articulation of <strong>the</strong> U.S. government’s<strong>Internet</strong> freedom strategy, but questions rema<strong>in</strong>.For example, does <strong>the</strong> government aim to promote<strong>the</strong> onl<strong>in</strong>e freedoms of expression, assemblyand association as <strong>in</strong>tr<strong>in</strong>sic goods, regardlessof whe<strong>the</strong>r <strong>the</strong>ir exercise engenders democraticchange offl<strong>in</strong>e? Or does <strong>the</strong> U.S. governmentbelieve that, on balance, a freer <strong>Internet</strong> willpromote democratic political change? The adm<strong>in</strong>istrationstill lacks a clear message for precisely whyit is undertak<strong>in</strong>g efforts to promote onl<strong>in</strong>e freedom<strong>in</strong> <strong>the</strong> first place, which has produced confusionabout its overall approach to <strong>Internet</strong> freedom.Craft<strong>in</strong>g <strong>the</strong> MessageIn her 2011 speech, Cl<strong>in</strong>ton said, “There is a debatecurrently under way <strong>in</strong> some circles about whe<strong>the</strong>r<strong>the</strong> <strong>Internet</strong> is a force for liberation or repression.But I th<strong>in</strong>k that debate is largely beside <strong>the</strong> po<strong>in</strong>t.” 21In fact, that is <strong>the</strong> key po<strong>in</strong>t – if <strong>the</strong> <strong>Internet</strong> is aforce for repression, why should <strong>the</strong> United Statessupport its freer use?Adm<strong>in</strong>istration officials emphasize that <strong>the</strong>irpolicies support freedom of <strong>the</strong> <strong>Internet</strong>, notfreedom via <strong>the</strong> <strong>Internet</strong>; <strong>the</strong>se policies are notpart of a broader democracy-promotion strategy.In her 45-m<strong>in</strong>ute speech, Cl<strong>in</strong>ton used <strong>the</strong>term “democracy” just once, when defend<strong>in</strong>g <strong>the</strong>adm<strong>in</strong>istration’s position on WikiLeaks. Instead,she said that <strong>the</strong> United States supports a free<strong>Internet</strong> because it helps build “strong” and “prosperous”states. She did not say that <strong>the</strong> <strong>Internet</strong>helps build freer or more democratic states. 22Yet that is a key reason why <strong>the</strong> adm<strong>in</strong>istrationsupports <strong>Internet</strong> freedom. It is <strong>the</strong> central motivationbeh<strong>in</strong>d <strong>the</strong> State Department’s tra<strong>in</strong><strong>in</strong>g andtechnology programs, which are aimed at onl<strong>in</strong>eactivists, dissidents and democracy-related NGOs.The U.S. government should clearly state why itpromotes <strong>Internet</strong> freedom: Do<strong>in</strong>g so accords withAmerica’s longstand<strong>in</strong>g tradition of promot<strong>in</strong>ghuman rights, <strong>in</strong>clud<strong>in</strong>g freedoms of expression,association and assembly, and <strong>the</strong> United Statesis bett<strong>in</strong>g that access to an open <strong>Internet</strong> canfoster elements of democracy <strong>in</strong> autocratic states.Officials can acknowledge <strong>the</strong> potential downsides,but <strong>the</strong>y need not shy from publicly acknowledg<strong>in</strong>g<strong>the</strong> U.S. <strong>in</strong>terest <strong>in</strong> democratization and <strong>the</strong>
hope that promot<strong>in</strong>g <strong>Internet</strong> freedom can assistthose who are press<strong>in</strong>g for liberal change abroad.The government should not discredit dissidentsby suggest<strong>in</strong>g that <strong>the</strong>y are an arm of U.S. foreignpolicy, but refra<strong>in</strong><strong>in</strong>g entirely from mention<strong>in</strong>gdemocracy <strong>in</strong> connection with <strong>Internet</strong> freedomrisks underm<strong>in</strong><strong>in</strong>g domestic support for its policies– <strong>in</strong>clud<strong>in</strong>g on Capitol Hill. And <strong>the</strong> current rhetoricalambivalence belies <strong>the</strong> <strong>in</strong>creas<strong>in</strong>gly robust– <strong>in</strong>deed, <strong>in</strong>creas<strong>in</strong>gly impressive – U.S. efforts topromote <strong>Internet</strong> freedom.At <strong>the</strong> same time, <strong>the</strong> United States shouldcounter <strong>the</strong> view that <strong>Internet</strong> freedom is merelyan American project cooked up <strong>in</strong> Wash<strong>in</strong>gton,ra<strong>the</strong>r than a notion rooted <strong>in</strong> universal humanrights. The United States promotes <strong>Internet</strong>freedom more actively than any o<strong>the</strong>r country,and is one of <strong>the</strong> only countries that activelyfunds circumvention technologies. It leads <strong>in</strong>promot<strong>in</strong>g <strong>in</strong>ternational norms and has made agreater effort than most to <strong>in</strong>corporate <strong>Internet</strong>freedom <strong>in</strong>to its broader foreign policy. This hasprovoked concerns that American advocacy willta<strong>in</strong>t <strong>the</strong> efforts of local activists. For example,Sami ben Gharbia, a prom<strong>in</strong>ent Ne<strong>the</strong>rlandsbasedTunisian blogger, has said, “Many peopleoutside of <strong>the</strong> U.S., not only <strong>in</strong> <strong>the</strong> Arab world,have a strong feel<strong>in</strong>g that <strong>the</strong> <strong>Internet</strong> <strong>Freedom</strong>mantra emitt<strong>in</strong>g from Wash<strong>in</strong>gton D.C. is just acover for strategic geopolitical agendas” and thatthis could threaten activists who accept supportand fund<strong>in</strong>g. 23 Autocratic governments rout<strong>in</strong>elydenounce <strong>Internet</strong> freedom-related activities asimpos<strong>in</strong>g American values, and some technologycompanies and foundations have shied awayfrom support<strong>in</strong>g circumvention and anonymitytechnologies because of <strong>the</strong>ir perceived tie to U.S.foreign policy.effort. Despite reservations from some, more than5,000 foreign activists and o<strong>the</strong>rs have accepted<strong>Internet</strong>-related tra<strong>in</strong><strong>in</strong>g funded by <strong>the</strong> StateDepartment, and many more employ U.S. government-fundedtechnology. 24 Many governmentshave not yet formulated policies <strong>in</strong> this area, butsome are express<strong>in</strong>g grow<strong>in</strong>g <strong>in</strong>terest <strong>in</strong> do<strong>in</strong>g so,<strong>in</strong>clud<strong>in</strong>g several European countries and <strong>the</strong> EU.To <strong>the</strong> extent that foreign governments advocatefor <strong>Internet</strong> freedom and foreign corporations jo<strong>in</strong>such efforts as <strong>the</strong> GNI and <strong>in</strong>ternational organizationspromote new norms, <strong>the</strong> United States willbe able to make a stronger argument that <strong>Internet</strong>freedom is truly a global effort.The response to such concerns should not be toavoid any suggestion that <strong>Internet</strong> freedom isrelated to American support of democracy andhuman rights, but ra<strong>the</strong>r to <strong>in</strong>ternationalize <strong>the</strong>| 13
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>14 |III. <strong>Internet</strong> <strong>Freedom</strong>and Political ChangeThe <strong>Internet</strong>’s potential as a tool for politicalchange captivated top foreign policy officials<strong>in</strong> 2009 dur<strong>in</strong>g what was quickly dubbed Iran’sTwitter Revolution. The new awareness grew asprotestors used <strong>the</strong> <strong>Internet</strong> and text messages tospread <strong>in</strong>formation and coord<strong>in</strong>ate efforts, andwas crystallized by <strong>the</strong> viral movement of a videodepict<strong>in</strong>g <strong>the</strong> brutal slay<strong>in</strong>g of a young Iranianstudent, Neda Agha-Soltan. The video, whichwas captured on a mobile phone and uploadedto YouTube, traveled across <strong>the</strong> Web and ontolocal and satellite television, prompt<strong>in</strong>g Obamato express his outrage at <strong>the</strong> kill<strong>in</strong>g. When <strong>the</strong>president of <strong>the</strong> United States uses a White Housepress conference to address material uploaded toYouTube, someth<strong>in</strong>g fundamental has changed <strong>in</strong><strong>the</strong> nature of modern communications.The focus on <strong>Internet</strong> freedom grew as <strong>the</strong> ArabSpr<strong>in</strong>g ga<strong>the</strong>red momentum a year and a half later.The wave of revolts across <strong>the</strong> Arab world, beg<strong>in</strong>n<strong>in</strong>g<strong>in</strong> Tunisia, <strong>the</strong>n sweep<strong>in</strong>g across Egypt and<strong>in</strong>to Libya, Bahra<strong>in</strong>, Yemen, Syria and elsewherewere fueled <strong>in</strong> part by activists us<strong>in</strong>g tools such asFacebook, Twitter, SMS (text messag<strong>in</strong>g) and o<strong>the</strong>rplatforms. Several regimes took draconian steps tostop onl<strong>in</strong>e organiz<strong>in</strong>g and communication. Thesense grew that <strong>the</strong> <strong>Internet</strong> mattered, but just howit mattered was not totally clear.In a sense, <strong>the</strong> <strong>Internet</strong> represents just <strong>the</strong> latestpart of a story that has unfolded for centuries.Communication technologies have played significantroles <strong>in</strong> political movements s<strong>in</strong>ce antiquity,from <strong>the</strong> pr<strong>in</strong>t<strong>in</strong>g press that empowered <strong>the</strong>Reformation, cassette tapes distributed by Iranianrevolutionaries <strong>in</strong> 1979, to fax mach<strong>in</strong>es used byPoland’s Solidarity movement and satellite televisiontoday. But <strong>the</strong> global nature of <strong>the</strong> <strong>Internet</strong>,its very low barrier to entry, its speed and <strong>the</strong>degree to which it empowers <strong>the</strong> <strong>in</strong>dividual allmake it qualitatively different from earlier technologies.The <strong>Internet</strong> itself has become <strong>the</strong> focusof attention by dictators, democracy activists andobservers around <strong>the</strong> world.Does <strong>Internet</strong> <strong>Freedom</strong> Lead to Democracy?The United States promotes <strong>Internet</strong> freedombecause Americans believe <strong>in</strong> <strong>the</strong> freedom ofexpression, <strong>in</strong> any medium. The country alsopromotes it because American leaders have betthat, on balance, <strong>the</strong> <strong>in</strong>creased availability of new,unfettered communications technologies abets <strong>the</strong>spread of democracy. But does it?Here we use <strong>the</strong> term “democracy” to mean a politicalsystem that is transparent and accountable to<strong>the</strong> public through free and fair elections; <strong>in</strong>cludesactive political participation by <strong>the</strong> citizenry;protects human rights; and ma<strong>in</strong>ta<strong>in</strong>s a rule oflaw that is fair to all citizens. 25 This is obviously anideal, and democratic systems exhibit many variations,but this def<strong>in</strong>ition offers a useful standardfor measur<strong>in</strong>g potential progress.Experts rema<strong>in</strong> deeply divided, as shown <strong>in</strong> <strong>the</strong>text box on <strong>the</strong> follow<strong>in</strong>g page, as to whe<strong>the</strong>runbridled access to <strong>the</strong> <strong>Internet</strong> can help transformauthoritarian regimes over time and br<strong>in</strong>g greaterfreedom to once-closed societies. Most attemptsto assess its impact rely on case studies, anecdotesor <strong>the</strong>ory. The novelty of <strong>the</strong> phenomenon and <strong>the</strong>few and widely vary<strong>in</strong>g data po<strong>in</strong>ts pose notableanalytical challenges, and assessments requirea certa<strong>in</strong> amount of subjective <strong>in</strong>terpretation.Facebook clearly played a major role <strong>in</strong> build<strong>in</strong>g anopposition to <strong>the</strong> Hosni Mubarak regime <strong>in</strong> Egyptand <strong>in</strong> organiz<strong>in</strong>g protests. But after <strong>the</strong> governmentshut off <strong>the</strong> <strong>Internet</strong>, protests became bigger,not smaller. So did this demonstrate <strong>the</strong> <strong>Internet</strong>’slimited role as a tool of agitation? Or did <strong>the</strong>shutoff of cherished onl<strong>in</strong>e tools itself spur enragedcitizens to demonstrate <strong>in</strong>stead of stay<strong>in</strong>g home(possibly <strong>in</strong> front of a computer)?
Does <strong>the</strong> <strong>Internet</strong> Promote Democracy?Optimists“The <strong>Internet</strong> is above all <strong>the</strong> most fantastic means ofbreak<strong>in</strong>g down <strong>the</strong> walls that close us off from oneano<strong>the</strong>r. For <strong>the</strong> oppressed peoples of <strong>the</strong> world,<strong>the</strong> <strong>Internet</strong> provides power beyond <strong>the</strong>ir wildesthopes.” 26Bernard KouchnerFormer French <strong>Foreign</strong> M<strong>in</strong>ister“It does make a difference when people <strong>in</strong>side closedregimes get access to <strong>in</strong>formation – which is whydictatorships make such efforts to block comprehensive<strong>Internet</strong> access … [promot<strong>in</strong>g <strong>Internet</strong> freedom]would be a cheap and effective way of stand<strong>in</strong>g withIranians while chipp<strong>in</strong>g away at <strong>the</strong> 21st-century wallsof dictatorship.” 27Nicholas KristofThe New York Times columnist“The <strong>Internet</strong> is possibly one of <strong>the</strong> greatest tools fordemocratization and <strong>in</strong>dividual freedom that we’veever seen.” 28Condoleezza RiceFormer Secretary of State“Without Twitter, <strong>the</strong> people of Iran would not havefelt empowered and confident to stand up for freedomand democracy.” 29Mark PfeifleFormer Deputy National Security Advisor“If you want to liberate a society, just give <strong>the</strong>m <strong>the</strong><strong>Internet</strong>.” 30Wael GhonimEgyptian Google Executiveand democracy activistSkeptics“The idea that <strong>the</strong> <strong>Internet</strong> favors <strong>the</strong> oppressedra<strong>the</strong>r than <strong>the</strong> oppressor is marred by what I callcyber-utopianism: a naïve belief <strong>in</strong> <strong>the</strong> emancipatorynature of onl<strong>in</strong>e communication that rests on a stubbornrefusal to admit its downside.” 31Evgeny MorozovAuthor of The Net Delusion“The platforms of social media are built around weakties … weak ties seldom lead to high-risk activism.” 32Malcolm GladwellThe New Yorker staff writer“Democracy isn’t just a tweet away.” 33Jeffrey Gedm<strong>in</strong>Former President of Radio Free Europe/Radio Liberty“It is time to get Twitter’s role <strong>in</strong> <strong>the</strong> events <strong>in</strong> Iranright. Simply put: There was no Twitter Revolution<strong>in</strong>side Iran.” 34Golnaz EsfandiariSenior Correspondent for Radio Free Europe/Radio Liberty“Techno-optimists appear to ignore <strong>the</strong> fact that<strong>the</strong>se tools are value neutral; <strong>the</strong>re is noth<strong>in</strong>g <strong>in</strong>herentlypro-democratic about <strong>the</strong>m. To use <strong>the</strong>m is toexercise a form of freedom, but it is not necessarily afreedom that promotes <strong>the</strong> freedom of o<strong>the</strong>rs.” 35Ian BremmerPresident of <strong>the</strong> Eurasia GroupIt has become axiomatic to say that <strong>the</strong> <strong>Internet</strong> doesnot itself create democracies or overthrow regimes;people do. This is obviously true, but if new communicationstools do matter – and <strong>the</strong>re appears to be atleast nascent evidence that <strong>the</strong>y do – <strong>the</strong>n <strong>the</strong>y can playa role <strong>in</strong> several dist<strong>in</strong>ct ways. An important reportissued by <strong>the</strong> United States Institute of Peace (USIP)presented a useful framework for exam<strong>in</strong><strong>in</strong>g how newcommunications technologies might affect politicalaction. The paper identifies five dist<strong>in</strong>ct mechanismsthrough which <strong>the</strong> <strong>Internet</strong> might promote (or be usedby regimes to block) democratic progress. 36 Here wedeepen <strong>the</strong> analysis of <strong>the</strong>se mechanisms and add twoadditional factors that affect <strong>the</strong>m.| 15
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>16 |The <strong>Internet</strong> may affect <strong>in</strong>dividuals, by alter<strong>in</strong>g orre<strong>in</strong>forc<strong>in</strong>g <strong>the</strong>ir political attitudes, mak<strong>in</strong>g <strong>the</strong>mmore attuned to political events, and enabl<strong>in</strong>g <strong>the</strong>mto participate <strong>in</strong> politics to a greater degree than<strong>the</strong>y could o<strong>the</strong>rwise. This does not automaticallytranslate <strong>in</strong>to a more activist population; as <strong>the</strong>USIP study notes, it could actually make citizensmore passive by divert<strong>in</strong>g <strong>the</strong>ir attention away fromoffl<strong>in</strong>e political activism and toward less significantonl<strong>in</strong>e activity. 37 Some have called this “slacktivism,”exemplified by <strong>the</strong> millions of <strong>in</strong>dividuals whosigned onl<strong>in</strong>e petitions to end genocide <strong>in</strong> Darfurbut who took no fur<strong>the</strong>r action. 38 At <strong>the</strong> same time,<strong>in</strong>dividuals freely express<strong>in</strong>g <strong>the</strong>mselves on <strong>the</strong><strong>Internet</strong> are exercis<strong>in</strong>g a basic democratic right. Asdemocracy scholar Larry Diamond po<strong>in</strong>ts out, used<strong>in</strong> this way, <strong>the</strong> <strong>Internet</strong> can help “widen <strong>the</strong> publicsphere, creat<strong>in</strong>g a more pluralistic and autonomousarena of news, commentary and <strong>in</strong>formation.” 39It can also serve as an <strong>in</strong>strument through which<strong>in</strong>dividuals can push for transparency and governmentaccountability, both of which are hallmarks ofmature democracies. 40New media might also affect <strong>in</strong>tergroup relations,by generat<strong>in</strong>g new connections among <strong>in</strong>dividuals,spread<strong>in</strong>g <strong>in</strong>formation and br<strong>in</strong>g<strong>in</strong>g toge<strong>the</strong>rpeople and groups. (Some have worried about <strong>the</strong>opposite effect – <strong>the</strong> tendency of <strong>the</strong> <strong>Internet</strong> topolarize <strong>in</strong>dividuals and groups around particularideological tendencies.) 41 This may occur notonly with<strong>in</strong> countries, but also among <strong>the</strong>m; <strong>the</strong>protests <strong>in</strong> Tunisia sparked a clear rise <strong>in</strong> politicalconsciousness and activism across <strong>the</strong> Arab world– much of it facilitated by <strong>Internet</strong>-based communicationsand satellite television. 42 It may also takeplace over a long period of time; Clay Shirky, anexpert at New York University, argues that a “densify<strong>in</strong>gof <strong>the</strong> public sphere” may need to occurbefore an upris<strong>in</strong>g turns <strong>in</strong>to a revolution. 43New communications technologies could alsoaffect collective action, by help<strong>in</strong>g change op<strong>in</strong>ionand mak<strong>in</strong>g it easier for <strong>in</strong>dividuals and groupsto organize protests <strong>in</strong> repressive countries.Unconnected <strong>in</strong>dividuals dissatisfied with <strong>the</strong>prevail<strong>in</strong>g politics may realize that o<strong>the</strong>rs share<strong>the</strong>ir views, which might form <strong>the</strong> basis for collectiveaction. 44 Relatively small groups, elites oro<strong>the</strong>r motivated dissidents might use <strong>the</strong> <strong>Internet</strong>to communicate or organize protests. Even if <strong>the</strong>number of committed onl<strong>in</strong>e activists is small, <strong>the</strong>ymight never<strong>the</strong>less dissem<strong>in</strong>ate <strong>in</strong>formation to <strong>the</strong>general population or <strong>in</strong>spire more widespreadprotests. 45 Aga<strong>in</strong>, it is important to dist<strong>in</strong>guishsuch action from group “slacktivism;” as <strong>the</strong>successful protests <strong>in</strong> Egypt showed, <strong>the</strong> regimeonly began to teeter when thousands of citizensphysically occupied Tahrir Square. Though <strong>in</strong>itialprotests may have been organized via Facebook,<strong>the</strong> Mubarak government would still be <strong>in</strong> power if<strong>the</strong> protests had been conf<strong>in</strong>ed only to cyberspace.These new technologies clearly affect regimepolicies as well. Governments have employed ahuge array of techniques aimed at controll<strong>in</strong>g <strong>the</strong><strong>Internet</strong> and ensur<strong>in</strong>g that <strong>the</strong>ir political opponentscannot use it freely. This goes well beyondcensorship, which garners <strong>the</strong> bulk of popularattention. Autocracies also regularly monitor dissidentcommunications; mobilize regime defenders;spread propaganda and false <strong>in</strong>formation designedto disrupt protests and outside groups; <strong>in</strong>filtratesocial movements; and disable dissident websites,communications tools and databases. These ando<strong>the</strong>r practices can also <strong>in</strong>duce self-censorship ando<strong>the</strong>r forms of self-restra<strong>in</strong>t by publishers, activists,onl<strong>in</strong>e commentators and opposition politicians.Autocrats can also turn dissidents’ use of <strong>the</strong><strong>Internet</strong> aga<strong>in</strong>st <strong>the</strong>m. In Iran, for example, usersof social media – which l<strong>in</strong>ked <strong>the</strong>ir accounts tothose of o<strong>the</strong>r protestors – <strong>in</strong>advertently createda virtual catalogue of political opponents thatenabled <strong>the</strong> government to identify and persecute<strong>in</strong>dividuals. The regime established a website thatpublished photos of protestors and used crowdsourc<strong>in</strong>g to identify <strong>the</strong> <strong>in</strong>dividuals’ names. 46
Similarly, <strong>the</strong> Revolutionary Guard reportedlysent <strong>in</strong>timidat<strong>in</strong>g messages to those who postedpro-opposition messages and forced some citizensenter<strong>in</strong>g <strong>the</strong> country to open <strong>the</strong>ir Facebookaccounts upon arrival. 47 In <strong>the</strong> midst of <strong>the</strong>Arab protests, Syria allowed its citizens to accessFacebook and YouTube for <strong>the</strong> first time <strong>in</strong> threeyears. Some human rights activists suspected that<strong>the</strong> government made <strong>the</strong> change precisely <strong>in</strong> orderto monitor people and activities on <strong>the</strong>se sites. 48Similarly, shortly after <strong>the</strong> Egyptian governmentlifted its <strong>Internet</strong> blackout <strong>in</strong> early 2011, pro-Mubaraksupporters disrupted planned demonstrationsby post<strong>in</strong>g messages on Facebook and Twittersay<strong>in</strong>g that <strong>the</strong> protests had been canceled. 49 Thegovernment reportedly sent Facebook messages tocitizens urg<strong>in</strong>g <strong>the</strong>m not to attend protests becausedo<strong>in</strong>g so would harm <strong>the</strong> Egyptian economy. 50 In<strong>the</strong> same ve<strong>in</strong>, <strong>the</strong> Ch<strong>in</strong>ese government employsan estimated 250,000 “50 Cent Party” memberswho are paid a small sum each time <strong>the</strong>y posta pro-government message onl<strong>in</strong>e. 51 And afteran anonymous post on <strong>the</strong> U.S.-based Ch<strong>in</strong>eselanguage website Boxun.com called on activiststo stage Ch<strong>in</strong>a’s own “Jasm<strong>in</strong>e Revolution,” nodemonstrators turned up at <strong>the</strong> rally po<strong>in</strong>t – but itwas flooded with security teams and pla<strong>in</strong>clo<strong>the</strong>sofficers. 52 Some speculated that Ch<strong>in</strong>ese officials<strong>the</strong>mselves may have authored <strong>the</strong> anonymouspost<strong>in</strong>g <strong>in</strong> an effort to draw out political dissidents.53 While no evidence has emerged to support<strong>the</strong> claim, it is not hard to imag<strong>in</strong>e such an attempttak<strong>in</strong>g place <strong>in</strong> <strong>the</strong> future.Autocracies are engaged <strong>in</strong> “offl<strong>in</strong>e” attempts torepress <strong>Internet</strong> use, as well. Saudi Arabia, forexample, has not only blocked websites but alsoplaced hidden cameras <strong>in</strong> <strong>Internet</strong> cafes aimedat monitor<strong>in</strong>g user behavior and required cafeowners to give <strong>the</strong>ir customer lists to governmentofficials. 54 Ch<strong>in</strong>a requires users to register <strong>the</strong>iridentification upon entry to a cybercafe. 55 AndLibyan officials simply demanded that refugeesflee<strong>in</strong>g <strong>the</strong> recent fight<strong>in</strong>g turn over <strong>the</strong>ir cellphonesor SIM cards at border checkpo<strong>in</strong>ts. 56Beyond <strong>the</strong>se effects, new media can affect externalattention, by transmitt<strong>in</strong>g images and <strong>in</strong>formationto <strong>the</strong> outside world, beyond <strong>the</strong> control ofgovernment-run media and regime censorship andsp<strong>in</strong>. Such attention can mobilize sympathy forprotestors or hostility toward repressive regimes, 57as occurred when <strong>the</strong> video of Neda Agha-Soltanmoved from YouTube to ma<strong>in</strong>stream media.<strong>Digital</strong> videos and <strong>in</strong>formation may also have arebound effect; <strong>in</strong>formation transmitted out ofEgypt and Libya by social network<strong>in</strong>g and videohost<strong>in</strong>gsites dur<strong>in</strong>g <strong>the</strong> protests <strong>in</strong> those countriesmade its way back <strong>in</strong> via widely watched satellitebroadcasts. This effect could be particularly pronounced<strong>in</strong> countries like Yemen, where <strong>Internet</strong>penetration is low but Al Jazeera is widely viewed.Similarly, pr<strong>in</strong>t journalists have found sources andstories through social media and have used <strong>the</strong>same media to push <strong>the</strong>ir articles out to <strong>the</strong> world.In addition to <strong>the</strong> five mechanisms laid out byUSIP and noted above, we observe two additionalfactors that affect <strong>the</strong>m <strong>in</strong> various ways.The economic impact of <strong>the</strong> <strong>Internet</strong> might affect<strong>the</strong> degree of democratization <strong>in</strong> a country. The<strong>Internet</strong> has <strong>in</strong>creased labor productivity and correspond<strong>in</strong>geconomic growth, which may help middleclasses emerge <strong>in</strong> develop<strong>in</strong>g countries. 58 Becausenew middle classes tend to agitate for democraticrights, new technologies could <strong>in</strong>directly promotedemocratization. In 2011, Cl<strong>in</strong>ton referenced arelated dynamic, <strong>the</strong> “dictator’s dilemma,” stat<strong>in</strong>gthat autocrats “will have to choose between lett<strong>in</strong>g<strong>the</strong> walls fall or pay<strong>in</strong>g <strong>the</strong> price to keep <strong>the</strong>mstand<strong>in</strong>g … by resort<strong>in</strong>g to greater oppression andendur<strong>in</strong>g <strong>the</strong> escalat<strong>in</strong>g opportunity cost of miss<strong>in</strong>gout on <strong>the</strong> ideas that have been blocked and peoplewho have been disappeared.” 59 In o<strong>the</strong>r words, anautocrat can ei<strong>the</strong>r repress <strong>the</strong> <strong>Internet</strong> or enjoy itsfull economic benefits, but not both.| 17
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>18 |Whe<strong>the</strong>r <strong>the</strong> “dictator’s dilemma” actually existsrema<strong>in</strong>s unknown. There are certa<strong>in</strong>ly clear<strong>in</strong>dividual <strong>in</strong>stances where <strong>Internet</strong> repressionhas damaged a nation’s economy; Experts from<strong>the</strong> Organisation for Economic Co-operation andDevelopment (OECD) have estimated that Egypt’sfive-day <strong>Internet</strong> shutdown cost <strong>the</strong> country at least90 million dollars, a figure that does not <strong>in</strong>cludee-commerce, tourism or o<strong>the</strong>r bus<strong>in</strong>esses that relyon <strong>Internet</strong> connectivity. 60 But Ch<strong>in</strong>a seems to providea powerful counterexample s<strong>in</strong>ce it severelyrepresses <strong>the</strong> <strong>Internet</strong> while enjoy<strong>in</strong>g extraord<strong>in</strong>arilyhigh rates of susta<strong>in</strong>ed economic growth.Indeed, Ch<strong>in</strong>a appears to have used its restrictive<strong>Internet</strong> practices to squeeze out <strong>in</strong>ternationalcompetition and generate conditions where onlydomestic companies – ones that adhere to <strong>the</strong>government’s str<strong>in</strong>gent censorship and monitor<strong>in</strong>gpractices – can thrive. Ch<strong>in</strong>a’s largest domesticsearch eng<strong>in</strong>e, Baidu, exercises strict controls oncontent but has thrived s<strong>in</strong>ce Google pulled outof Ch<strong>in</strong>a <strong>in</strong> January 2010. Ch<strong>in</strong>a may be an outlier;<strong>the</strong> massive f<strong>in</strong>ancial and human resourcesit devotes to onl<strong>in</strong>e control may not be replicableelsewhere. O<strong>the</strong>r countries may be left with blunterforms of repression that degrade both <strong>the</strong> <strong>Internet</strong>’seconomic and political effects.In addition to <strong>the</strong> political and economic effectsdescribed above, new technologies can accelerateeach of <strong>the</strong>m. Google’s Eric Schmidt and JaredCohen have argued that faster computer powercomb<strong>in</strong>ed with <strong>the</strong> “many to many” geometry ofsocial media empowers <strong>in</strong>dividuals and groupsat <strong>the</strong> expense of governments and that this, <strong>in</strong>turn, <strong>in</strong>creases <strong>the</strong> rate of change. 61 Dissidents canidentify one ano<strong>the</strong>r, share <strong>in</strong>formation, organizeand connect with leaders and with external actors,all easier and faster than ever before. 62 Indeed, onehallmark of <strong>the</strong> 2011 Arab Spr<strong>in</strong>g was <strong>the</strong> astonish<strong>in</strong>grate of change as popular protests threatenedor toppled governments that had been <strong>in</strong> power fordecades <strong>in</strong> a matter of weeks. 63Aga<strong>in</strong>, <strong>the</strong> local political context is critical. Themedium may be global, but whe<strong>the</strong>r and how itenables <strong>in</strong>dividuals to foster democratic changelargely depends on a wide array of local variables,<strong>in</strong>clud<strong>in</strong>g opposition leadership, <strong>the</strong> existence ofcivil society <strong>in</strong>stitutions, <strong>the</strong> will<strong>in</strong>gness of <strong>the</strong>regime to crack down on dissident activity, and soforth. In Tunisia and Egypt for example, tens ofthousands of protestors responded to protest eventpages on Facebook by tak<strong>in</strong>g to <strong>the</strong> streets. Yet <strong>in</strong>o<strong>the</strong>r Arab states, a call on Facebook for a “dayof rage” did not have <strong>the</strong> same pronounced <strong>in</strong>fluence.The degree of openness <strong>in</strong> <strong>the</strong> local politicalsystem, <strong>the</strong> discontent among <strong>the</strong> population,<strong>the</strong> will<strong>in</strong>gness of <strong>the</strong> government to use coercivemeans to stop democratic activism, <strong>the</strong> role ofm<strong>in</strong>orities and o<strong>the</strong>r local factors all matter greatly.Experts from <strong>the</strong> Organisationfor Economic Co-operationand Development haveestimated that Egypt’s fiveday<strong>Internet</strong> shutdown cost<strong>the</strong> country at least 90 milliondollars, a figure that does not<strong>in</strong>clude e-commerce, tourismor o<strong>the</strong>r bus<strong>in</strong>esses that rely on<strong>Internet</strong> connectivity.The <strong>Internet</strong> does not automatically promotedemocratization; Iran’s Twitter revolution ledto no reforms while Egypt’s Facebook revolutiontoppled <strong>the</strong> Mubarak regime. Fur<strong>the</strong>rmore,<strong>the</strong> technology itself is agnostic; <strong>the</strong> same onl<strong>in</strong>e
tools that empower dissidents can aid dictators <strong>in</strong><strong>the</strong>ir oppression. In <strong>the</strong> short run, at least, a freer<strong>Internet</strong> does not automatically translate <strong>in</strong>to moreliberal political systems.Yet some case studies do demonstrate <strong>the</strong> <strong>Internet</strong>’sprofound potential: that access to an open <strong>Internet</strong>can help countries slide away from authoritarianismand toward democracy. Events <strong>in</strong> Iran, Tunisia,Egypt and elsewhere suggest that <strong>the</strong> <strong>Internet</strong> andrelated technologies (such as SMS) have <strong>in</strong>deedserved as critical tools for organiz<strong>in</strong>g protests,spread<strong>in</strong>g <strong>in</strong>formation among dissident partiesand transmitt<strong>in</strong>g images and <strong>in</strong>formation to <strong>the</strong>outside world – some of which moved onto satellitetelevision channels, fur<strong>the</strong>r boost<strong>in</strong>g <strong>the</strong>ir <strong>in</strong>fluence.64 And while experts cont<strong>in</strong>ue to argue about<strong>the</strong> precise effect, <strong>the</strong>y tend to agree that socialmedia tools have made revolutions <strong>in</strong> <strong>the</strong> MiddleEast easier and speedier than <strong>the</strong>y would haveo<strong>the</strong>rwise been. 65Perhaps <strong>the</strong> most compell<strong>in</strong>g l<strong>in</strong>k between a free<strong>Internet</strong> and democratization is also <strong>the</strong> simplest:Both dissidents and dictatorships abroad seem tobelieve that <strong>the</strong> <strong>Internet</strong> can have a transformativerole, and <strong>the</strong>y act on that basis. Dictatorshipsexpend enormous time and resources to clampdown on onl<strong>in</strong>e activity, and more than 40 countriesactively censor <strong>the</strong> <strong>Internet</strong> or engage <strong>in</strong>o<strong>the</strong>r forms of significant <strong>Internet</strong> repression. 66Meanwhile, millions of <strong>in</strong>dividuals use proxy serversand o<strong>the</strong>r circumvention and anonymity toolsto evade censorship and monitor<strong>in</strong>g. Dur<strong>in</strong>g <strong>the</strong>2009 presidential campaign <strong>in</strong> Iran, for example,both President Mahmoud Ahmad<strong>in</strong>ejad and hisopponent, Mir-Husse<strong>in</strong> Mousavi, cited <strong>the</strong> <strong>Internet</strong>as a tool through which <strong>the</strong> liberal oppositioncould mobilize support. 67 It is unlikely <strong>the</strong>y wereboth wrong. While <strong>the</strong> effect of <strong>the</strong> <strong>Internet</strong> willdepend on local conditions, <strong>the</strong>re are <strong>in</strong>deed reasonablegrounds for believ<strong>in</strong>g that a free <strong>Internet</strong>can help empower <strong>in</strong>dividuals to press for moreliberal political systems.IV. How <strong>the</strong> U.S. GovernmentPromotes <strong>Internet</strong> <strong>Freedom</strong>The U.S. government promotes <strong>Internet</strong> freedom<strong>in</strong> five ma<strong>in</strong> ways: provid<strong>in</strong>g <strong>Internet</strong> technologies,shap<strong>in</strong>g <strong>in</strong>ternational norms, encourag<strong>in</strong>g <strong>the</strong>private sector to expand its role, us<strong>in</strong>g economicdiplomacy and reform<strong>in</strong>g export controls.Provid<strong>in</strong>g <strong>Internet</strong> TechnologiesAs autocracies attempt to censor, identify,<strong>in</strong>timidate and monitor onl<strong>in</strong>e users, <strong>the</strong> U.S.government provides technologies that allow <strong>in</strong>dividualsliv<strong>in</strong>g <strong>in</strong> repressive environments to freelyaccess onl<strong>in</strong>e <strong>in</strong>formation. The U.S. governmentfunds <strong>the</strong>se technologies because, at present, <strong>the</strong>marketplace is highly unlikely to supply <strong>the</strong>m onits own. The private sector has few f<strong>in</strong>ancial <strong>in</strong>centivesto do so – it is difficult to charge anonymoussubscribers or sell ads <strong>in</strong> closed societies – and veryfew foreign governments, NGOs or foundationshave funded <strong>the</strong>m to date.A variety of circumvention technologies enabledissidents to penetrate firewalls and access blockedwebsites and censored <strong>in</strong>formation. Each toolemploys <strong>the</strong> same basic method: It routes a user’srequest through an unblocked webpage <strong>in</strong> orderto access banned content. For <strong>in</strong>stance, a user <strong>in</strong>Ch<strong>in</strong>a who cannot access The New York Timeswebsite could <strong>in</strong>stead reach a proxy site that could<strong>the</strong>n obta<strong>in</strong> <strong>in</strong>formation from <strong>the</strong> Times website.Freegate and Ultrasurf, for example, were designedto circumvent Ch<strong>in</strong>a’s Great Firewall by tak<strong>in</strong>gadvantage of open proxies – proxy servers availableto anyone on <strong>the</strong> <strong>Internet</strong> – which serve as aforward<strong>in</strong>g service to bypass restrictive firewalls.Though Freegate and Ultrasurf, both of which havereceived U.S. government fund<strong>in</strong>g, were designedfor use <strong>in</strong> Ch<strong>in</strong>a, some users are located <strong>in</strong> o<strong>the</strong>rcountries, <strong>in</strong>clud<strong>in</strong>g Iran. 68Psiphon is ano<strong>the</strong>r circumvention tool that relieson a worldwide network of servers to enable| 19
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>The Role of <strong>the</strong> <strong>Internet</strong> <strong>in</strong> Political Movements: A Brief History20 |By Jacquel<strong>in</strong>e Koo,Joseph S. Nye, Jr. InternThe 2009 Green Revolution <strong>in</strong> Iranand <strong>the</strong> 2011 Arab Spr<strong>in</strong>g representedwatershed events for manyforeign policy makers who are onlybeg<strong>in</strong>n<strong>in</strong>g to grapple with issuessurround<strong>in</strong>g <strong>Internet</strong> freedom.Yet us<strong>in</strong>g new communicationstechnologies as a tool for politicaltransformation began over adecade ago. Numerous examplesdemonstrate how <strong>Internet</strong> andmobile phone technology can beused to facilitate protests and evenrevolution <strong>in</strong> countries around <strong>the</strong>world. Some succeeded <strong>in</strong> br<strong>in</strong>g<strong>in</strong>gabout change, while o<strong>the</strong>rs did not.In January 2001, while Philipp<strong>in</strong>ePresident Joseph Estrada was ontrial for impeachment, thousandsof Filip<strong>in</strong>os protested <strong>the</strong> unwill<strong>in</strong>gnessof loyalist senators to present<strong>the</strong> evidence aga<strong>in</strong>st him. Theprotests were partly organizedby text messag<strong>in</strong>g – some sevenmillion messages were sent dur<strong>in</strong>g<strong>the</strong> week of <strong>the</strong> trial – whichhelped assemble over one millionprotesters at a major crossroad <strong>in</strong>Manila. Startled by <strong>the</strong> protests, <strong>the</strong>senators reversed <strong>the</strong> decision andreleased <strong>the</strong> evidence, result<strong>in</strong>g <strong>in</strong>Estrada’s impeachment. 69In fall 2004, a series of popularupris<strong>in</strong>gs that became knownas <strong>the</strong> Orange Revolution <strong>in</strong>Ukra<strong>in</strong>e were largely shaped bypro-democracy activists us<strong>in</strong>g <strong>the</strong><strong>Internet</strong> to protest a fraudulentpresidential election. Social activistsused <strong>the</strong> <strong>Internet</strong> and textmessag<strong>in</strong>g on mobile phones asplatforms for uncensored politicaldialogue and as a way to organizeprotests. The activists also setup election-monitor<strong>in</strong>g tra<strong>in</strong><strong>in</strong>gthrough pro-democracy websites,which was pivotal <strong>in</strong> help<strong>in</strong>g collectevidence of <strong>the</strong> fraudulent election.70 The street protests forced anew election that brought ViktorYushchenko, a democratic reformer,to power. 71In February 2005, <strong>the</strong> assass<strong>in</strong>ationof former Lebanese Prime M<strong>in</strong>isterRafik Hariri sparked a series ofanti-Syrian demonstrations, knowncollectively as <strong>the</strong> Cedar Revolution,that were reportedly organizedvia text messages and emails. Thedemonstrators used cellphonesequipped with digital cameras totake on-<strong>the</strong>-ground pictures, whichwere <strong>the</strong>n sent to news organizationsand friends who uploaded<strong>the</strong>m to websites <strong>in</strong> order to showwhat was happen<strong>in</strong>g to <strong>the</strong> rest of<strong>the</strong> world. 72 The demonstrationsultimately led to <strong>the</strong> withdrawal ofall Syrian troops from Lebanon.In February 2008, an unemployedeng<strong>in</strong>eer began a campaign viaFacebook, “One Million VoicesAga<strong>in</strong>st FARC,” to marshal millionsof protestors opposed to <strong>the</strong>violent tactics of <strong>the</strong> ColombianRevolutionary Armed Forces’(FARC) and its hold<strong>in</strong>g of some 700hostages. The organizers utilizedemail, Google Docs, <strong>in</strong>stant messag<strong>in</strong>gsystems and Skype tocommunicate with o<strong>the</strong>r organizers<strong>in</strong> o<strong>the</strong>r cities and with members of<strong>the</strong> Colombian diaspora abroad, 73result<strong>in</strong>g <strong>in</strong> simultaneous demonstrations<strong>in</strong> 27 Columbian cities and104 cities around <strong>the</strong> world. 74 TheFARC has been weakened, largelythrough Colombian governmentoperations, but rema<strong>in</strong>s <strong>the</strong> hemisphere’slargest <strong>in</strong>surgent group.In April 2008, young Egyptianactivists protested to support alabor strike <strong>in</strong> an <strong>in</strong>dustrial town.The campaign was organized viaFacebook and was called <strong>the</strong> “April 6Youth Movement,” after <strong>the</strong> day that<strong>the</strong> labor strike was held. In spr<strong>in</strong>g2008, <strong>the</strong> Facebook group boastedover 100,000 members. The protestitself was quickly conta<strong>in</strong>ed bysecurity forces, which dampened <strong>the</strong>overall enthusiasm of <strong>the</strong> movementamong its members. 75 Never<strong>the</strong>less,<strong>the</strong> onl<strong>in</strong>e forum reta<strong>in</strong>ed a membershipof over 70,000 youth byJanuary 2009, most of whom werenot politically <strong>in</strong>volved before jo<strong>in</strong><strong>in</strong>g<strong>the</strong> movement, and facilitatedheated political dialogue among itsmembers.In April 2009, anti-communist activists<strong>in</strong> Moldova protested allegedlyfraudulent parliamentary elections<strong>in</strong> which <strong>the</strong> Party of Communistswon a majority of seats. The activistsorganized protests through avariety of social media platforms,<strong>in</strong>clud<strong>in</strong>g Twitter, LiveJournal (apopular eastern European socialnetwork<strong>in</strong>g site) and Facebook.Demonstrators reportedly organizedflash mobs – large, briefdemonstrations assembled suddenly<strong>in</strong> a public space – by textmessage. 76 In response to <strong>the</strong> weeklongprotests, President Vladimir
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>The Promise and Perils of <strong>the</strong> <strong>Internet</strong>MoldovaMoldovan activists organized protestsand flash mobs <strong>in</strong> part through socialmedia platforms to denounce April2009 parliamentary election results,alleg<strong>in</strong>g fraud aga<strong>in</strong>st <strong>the</strong> Party ofCommunists.Cuba<strong>Internet</strong> activity <strong>in</strong> Cuba – whereless than 13 percent of <strong>the</strong> populationhad access <strong>in</strong> 2009 – has beenseverely stifled due to governmentmonitor<strong>in</strong>g and steep penalties foronl<strong>in</strong>e dissent, result<strong>in</strong>g <strong>in</strong> a culture ofself-censorship among users.ColombiaIn February 2008, an unemployed eng<strong>in</strong>eer’sFacebook campaign, “One MillionVoices Aga<strong>in</strong>st FARC,” marshaled millionsof demonstrators <strong>in</strong> 27 Colombiancities and 104 cities around <strong>the</strong> world <strong>in</strong>opposition to kidnapp<strong>in</strong>gs and violencecarried out by <strong>the</strong> Colombian RevolutionaryArmed Forces (FARC).Tunisia and EgyptThe December 2010 “Jasm<strong>in</strong>e Revolution”<strong>in</strong> Tunisia and <strong>the</strong> January 2011revolution <strong>in</strong> Egypt witnessed activistsemploy<strong>in</strong>g Facebook and o<strong>the</strong>r socialmedia platforms to organize demonstrationsaga<strong>in</strong>st authoritarian rule.21 |
Ukra<strong>in</strong>eThe fall 2004 Orange Revolution, aseries of demonstrations alleg<strong>in</strong>gfraud <strong>in</strong> presidential elections, waslargely organized through <strong>the</strong> <strong>Internet</strong>and mobile phone text messages,and prompted a new election thatbrought to power Viktor Yushchenko,a democratic reformer.KyrgyzstanIn April 2010, Twitter and o<strong>the</strong>r socialmedia platforms helped br<strong>in</strong>g attentionto protests aga<strong>in</strong>st PresidentKurmanbek Bakiyev’s adm<strong>in</strong>istration,contribut<strong>in</strong>g to pressure for PresidentBakiyev’s resignation.Ch<strong>in</strong>aBeij<strong>in</strong>g wields one <strong>the</strong> world’s largestand most sophisticated systems – <strong>the</strong>“Great Firewall” – for filter<strong>in</strong>g andblock<strong>in</strong>g <strong>Internet</strong> traffic, while employ<strong>in</strong>gabout 250,000 “Fifty Cent Party”members who post pro-Ch<strong>in</strong>ese CommunistParty propaganda onl<strong>in</strong>e.IranThe June 2009 “Twitter Revolution”<strong>in</strong>volved activists upload<strong>in</strong>g mobilephone videos to YouTube that werereplayed on satellite television, aswell as activists us<strong>in</strong>g social media toorganize efforts and show <strong>the</strong> world<strong>the</strong> regime’s brutal repression.Philipp<strong>in</strong>esIn January 2001, text messageorganizedprotests brought toge<strong>the</strong>rone million demonstrators urg<strong>in</strong>g <strong>the</strong>Philipp<strong>in</strong>e Senate to release evidencethat would later be used to impeachPresident Joseph Estrada.LebanonIn February 2006, follow<strong>in</strong>g <strong>the</strong> assass<strong>in</strong>ationof former Lebanese PrimeM<strong>in</strong>ister Rafik Hariri, anti-Syrian demonstrations,organized <strong>in</strong> part by textmessages and emails, ultimately ledto <strong>the</strong> withdrawal of all Syrian troopsfrom Lebanon.BurmaBurmese cyber dissidents have used<strong>the</strong> <strong>Internet</strong> to upload videos of antigovernmentdemonstrations and, asdur<strong>in</strong>g <strong>the</strong> 2007 Saffron Revolution,have been known to send digital filesacross <strong>the</strong> border to be uploadedfrom foreign computers.| 22
Voron<strong>in</strong> called for a recount, and<strong>the</strong> electoral commission foundno evidence of fraud. The Party ofCommunists proceeded to take <strong>the</strong>majority of seats <strong>in</strong> Parliament but,weakened by <strong>the</strong> protests, failed toelect a prime m<strong>in</strong>ister. 77 The presidentdissolved Parliament threemonths later.In June 2009, supporters of <strong>the</strong>opposition candidate, Mir-Hosse<strong>in</strong>Mousavi, staged massive protestschalleng<strong>in</strong>g <strong>the</strong> results of <strong>the</strong>Iranian presidential election thatnamed <strong>the</strong> <strong>in</strong>cumbent PresidentMahmoud Ahmad<strong>in</strong>ejad <strong>the</strong> w<strong>in</strong>ner.The protests known as <strong>the</strong> GreenRevolution were also nicknamed <strong>the</strong>“Twitter Revolution” for <strong>the</strong> role thatTwitter and o<strong>the</strong>r <strong>Internet</strong>-basedsocial network<strong>in</strong>g sites reportedlyplayed <strong>in</strong> facilitat<strong>in</strong>g communicationwith<strong>in</strong> Iran and with <strong>the</strong> rest of<strong>the</strong> world. The demonstrations wereput down with brutal force and <strong>the</strong>revolution failed.In April 2010, a series of riots anddemonstrations took place <strong>in</strong>Kyrgyzstan stemm<strong>in</strong>g from dissatisfactionand anger aga<strong>in</strong>stPresident Kurmanbek Bakiyev’sadm<strong>in</strong>istration. Observers haveoffered differ<strong>in</strong>g perspectives on<strong>the</strong> role social media played dur<strong>in</strong>g<strong>the</strong> Kyrgyz protests (with some, for<strong>in</strong>stance, argu<strong>in</strong>g that platformssuch as Twitter were more effective<strong>in</strong> broadcast<strong>in</strong>g <strong>the</strong> demonstrationsthan <strong>in</strong> organiz<strong>in</strong>g <strong>the</strong>m). 78 <strong>Age</strong>neral consensus exists, however,that Twitter and o<strong>the</strong>r social mediaplatforms helped br<strong>in</strong>g attentionto <strong>the</strong> revolt and contributed tomount<strong>in</strong>g pressure for Bakiyev tostep down.In December 2010, Tunisianstook to <strong>the</strong> streets protest<strong>in</strong>ghigh unemployment, high foodprices, corruption and <strong>the</strong> lack offreedom of speech, and called forPresident Z<strong>in</strong>e el-Abid<strong>in</strong>e Ben Alito step down. These protests weredubbed <strong>the</strong> “Jasm<strong>in</strong>e Revolution,”but were also called <strong>the</strong> “FacebookRevolution.” 79 The protests werespearheaded by a number of youngbloggers that employed Facebook,Twitter, blogg<strong>in</strong>g sites and emailto organize protests nation-wide. 80On January 14, 2011, after 28 daysof protests, Ben Ali dissolved <strong>the</strong>Parliament and <strong>the</strong>n resigned, end<strong>in</strong>ghis 23-year rule.In January 2011, Egyptians took part<strong>in</strong> peaceful mass demonstrationsand strikes call<strong>in</strong>g for PresidentHosni Mubarak to step down,actions that escalated <strong>in</strong>to violentclashes with <strong>the</strong> police. The protestswere organized through <strong>the</strong> “WeAre All Khaled Said” Facebook page,named after a young blogger whowas beaten to death by police <strong>in</strong>June 2010, and whose death fueled<strong>the</strong> outrage surround<strong>in</strong>g <strong>the</strong> <strong>in</strong>itialrevolts. 81 Over 2 million people protested<strong>in</strong> Cairo’s Tahrir Square andprotests were held <strong>in</strong> several o<strong>the</strong>rmajor Egyptian cities. 82 Observ<strong>in</strong>g<strong>the</strong> protestors’ use of social media,<strong>the</strong> Mubarak regime shut downnearly all <strong>Internet</strong> and cellphoneservice with<strong>in</strong> <strong>the</strong> country for fivedays. 83 The shutdown backfired –<strong>the</strong> protests grew enormously and<strong>the</strong> move prompted both <strong>in</strong>ternationalcondemnation and domesticoutrage. 84 On February 11, Mubarakstepped down after 30 years ofpower and handed control to militaryleaders.As of this writ<strong>in</strong>g, mass protestscont<strong>in</strong>ue <strong>in</strong> countries across<strong>the</strong> Middle East. The role of <strong>the</strong><strong>Internet</strong> <strong>in</strong> <strong>in</strong>fluenc<strong>in</strong>g and facilitat<strong>in</strong>g<strong>the</strong>se demonstrations varies bycountry, and <strong>the</strong> extent to which<strong>the</strong> protests will ultimately causepolitical change rema<strong>in</strong>s unclear.However, <strong>the</strong>se examples showthat <strong>the</strong> <strong>Internet</strong> gives activists<strong>in</strong> closed societies tools throughwhich to express dissent and unite<strong>in</strong>dividuals at an unprecedentedpace and scale, and will undoubtedlyserve as a tool for politicalaction – among both protestorsand <strong>the</strong> regimes <strong>the</strong>y oppose – for<strong>the</strong> foreseeable future.| 23
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>24 |restricted users to reroute <strong>the</strong>ir requests aroundfirewalls. While <strong>the</strong>se tools allow users to puncturefirewalls, <strong>the</strong>y do not provide absolute anonymity.Users may still be exposed to state surveillancepractices, especially <strong>in</strong> countries where <strong>Internet</strong>service providers are required to reta<strong>in</strong> data onuser activity – a virtual paper trail of what websiteseach user has visited. 85 They have ano<strong>the</strong>r drawbackas well: They cannot access content with<strong>in</strong> acountry that censors.O<strong>the</strong>r technologies help users ma<strong>in</strong>ta<strong>in</strong> <strong>the</strong>ir anonymity<strong>in</strong> <strong>the</strong> face of a regime’s watchful eye. TheTor Project, which received nearly 750,000 dollarsfrom <strong>the</strong> U.S. government between 2006 and 2010,has developed one notable tool. 86 Tor uses a network<strong>in</strong> which encrypted messages pass throughseveral network nodes known as “onion routers”that <strong>the</strong>n peel away layers of encryption as <strong>in</strong>formationis transmitted among proxy servers around<strong>the</strong> world. The network allows users to hide <strong>the</strong>irlocation from websites <strong>the</strong>y are visit<strong>in</strong>g, enabl<strong>in</strong>g<strong>the</strong>m to evade governments and o<strong>the</strong>rs attempt<strong>in</strong>gto trace <strong>the</strong>ir location. For example, a Tor user<strong>in</strong> Iran might appear as on a website registry as auser <strong>in</strong> Germany if <strong>the</strong> last proxy server used werelocated <strong>in</strong> Germany. In addition, virtual privatenetworks (VPNs) encrypt and tunnel all <strong>Internet</strong>traffic through a proxy, enabl<strong>in</strong>g <strong>the</strong>ir users to circumventfirewalls and use webmail, chat and o<strong>the</strong>ronl<strong>in</strong>e communication services. 87 Most VPNs areavailable for a nom<strong>in</strong>al subscription fee. One popularVPN, Hotspot Shield, uses ads <strong>in</strong> lieu of a fee,allow<strong>in</strong>g users to subscribe to <strong>the</strong> service for free.O<strong>the</strong>r technological tools enhance <strong>the</strong> ability ofdissidents and activists to use <strong>the</strong> <strong>Internet</strong> freely.Software exists to help protect websites aga<strong>in</strong>stDDoS attacks, which can be launched by autocraticregimes or patriotic hackers (<strong>in</strong>dividuals orgroups who express nationalistic pride by attack<strong>in</strong>gforeign government or dissident websites) bysend<strong>in</strong>g millions of page requests per second to asite, <strong>the</strong>reby overload<strong>in</strong>g and crash<strong>in</strong>g its servers.O<strong>the</strong>r available tools help secure onl<strong>in</strong>e databases(of human rights abuses, for example), providemirror sites to keep websites live dur<strong>in</strong>g an attackand archive uploaded data so that it can be easilyreposted after a website returns to service. In addition,as mobile technology <strong>in</strong>creas<strong>in</strong>gly becomes ama<strong>in</strong> platform for onl<strong>in</strong>e activity, <strong>the</strong>re is greater<strong>in</strong>terest <strong>in</strong> secure cellphones and encrypted mobilecommunications. In a positive move, <strong>the</strong> StateDepartment is support<strong>in</strong>g <strong>the</strong> development ofan <strong>in</strong>novative application that would allow prodemocracyactivists to hit a “panic button” before<strong>the</strong>ir mobile phones are confiscated, eras<strong>in</strong>g <strong>the</strong>iraddress book and send<strong>in</strong>g emergency alerts too<strong>the</strong>r campaigners. 88Yet such tools cannot be used effectively by activistswho lack <strong>the</strong> skills to employ <strong>the</strong>m, and <strong>the</strong>ycan actually be dangerous. Used improperly, <strong>the</strong>ymay give users a false sense of security or expose<strong>the</strong>ir users identities and onl<strong>in</strong>e actions to authorities.As with o<strong>the</strong>r elements of American humanrights advocacy, only <strong>in</strong>dividuals on <strong>the</strong> groundcan calculate <strong>the</strong>ir personal risks and decide whichare worth tak<strong>in</strong>g. However, <strong>the</strong> United States has aresponsibility to ensure that users of technologiesit funds make decisions that are as fully <strong>in</strong>formedas possible. It also has a responsibility to ensurethat <strong>the</strong> tools it supports work as advertised. Thisrequires, <strong>in</strong> part, subject<strong>in</strong>g any U.S. governmentfundedcircumvention technologies to rigorousanalysis before <strong>the</strong>y are deployed to ensure <strong>the</strong>y donot conta<strong>in</strong> vulnerabilities that could be exploitedby authoritarian regimes. To do o<strong>the</strong>rwise potentiallysubjects dissidents to grave threat. (See “TheDilemmas of <strong>Digital</strong> Technology” text box.)Properly us<strong>in</strong>g new technologies must alsocont<strong>in</strong>ue to be part of <strong>the</strong> substantial tra<strong>in</strong><strong>in</strong>gprograms funded by <strong>the</strong> U.S. government. Someof this tra<strong>in</strong><strong>in</strong>g focuses on build<strong>in</strong>g <strong>the</strong> onl<strong>in</strong>eresilience of activist organizations, to help <strong>the</strong>mrespond when <strong>the</strong>y are victims of an attack andto reboot <strong>the</strong>ir systems <strong>in</strong> a timely fashion. O<strong>the</strong>r
The Dilemmas of <strong>Digital</strong> Technology: The Cases of Haystack and FreegateA key element of <strong>the</strong> U.S. government’s<strong>Internet</strong> freedom agenda<strong>in</strong>volves provid<strong>in</strong>g circumventionand anonymity technologies tocyber dissidents <strong>in</strong> closed societies.However, each of <strong>the</strong>se technologiesposes an array of technical andpolitical dilemmas. While such toolscan be highly effective <strong>in</strong> help<strong>in</strong>g<strong>in</strong>dividuals liv<strong>in</strong>g under dictatorshipaccess <strong>the</strong> uncensored <strong>Internet</strong>,determ<strong>in</strong><strong>in</strong>g just how to do so canbe very difficult <strong>in</strong>deed. Two technologies– Haystack and Freegate– demonstrate <strong>the</strong>se dilemmas. Theformer shows <strong>the</strong> vital importance ofensur<strong>in</strong>g that a digital tool works asadvertised; <strong>the</strong> latter illustrates <strong>the</strong>diplomatic tensions that result fromsupport<strong>in</strong>g <strong>the</strong>se technologies.HaystackIn June 2009, <strong>in</strong> <strong>the</strong> midst of widespreadprotests <strong>in</strong> Iran, Aust<strong>in</strong> Heap,a 25-year old software eng<strong>in</strong>eer <strong>in</strong>San Francisco, announced that hehad developed a circumvention toolcalled Haystack that would help Iraniandissidents evade <strong>the</strong>ir government’sdraconian <strong>Internet</strong> censorshipfilters. “It’s completely secure for <strong>the</strong>user so <strong>the</strong> government can’t snoopon <strong>the</strong>m,” Heap said. “We use manyanonymiz<strong>in</strong>g steps so that identitiesare masked and it is as safe as possibleso people have a safe way tocommunicate with <strong>the</strong> world.” 89Haystack quickly became a sensation<strong>in</strong> <strong>the</strong> ma<strong>in</strong>stream media and Heapeven received <strong>the</strong> Guardian’s “Innovatorof <strong>the</strong> Year Award.” 90 Haystackcaught <strong>the</strong> eye of <strong>the</strong> State Department,and <strong>in</strong> March 2010 <strong>the</strong> TreasuryDepartment issued a license todistribute <strong>the</strong> software <strong>in</strong> Iran. 91 Yetwhile Heap touted <strong>the</strong> software’sstrong security features, <strong>the</strong> technologydid not undergo rigorous technicaltest<strong>in</strong>g or peer review and, as aresult, it went live <strong>in</strong> summer 2010with serious design flaws. 92An <strong>in</strong>dependent team crackedHaystack’s code with<strong>in</strong> six hours of itspublic release and determ<strong>in</strong>ed that <strong>the</strong>government of Iran would have beenable to discern users’ location andidentities. 93 As a result, <strong>the</strong> Haystackprogram was disbanded <strong>in</strong> September2010. As <strong>the</strong> U.S. government<strong>in</strong>creases its fund<strong>in</strong>g for circumventionand anonymity technologies, it mustsubject <strong>the</strong>m to rigorous technicalreview and <strong>in</strong>dependent evaluation– <strong>in</strong>clud<strong>in</strong>g by outside experts whennecessary – before <strong>the</strong>y are deployed.To do o<strong>the</strong>rwise risks not only wast<strong>in</strong>gtaxpayer dollars, but also putt<strong>in</strong>g dissidentsand activists at risk.FreegateFreegate shows <strong>the</strong> challenges ofbalanc<strong>in</strong>g <strong>Internet</strong> freedom effortswith broader foreign policy priorities.Freegate is a censorship circumventiontool developed by <strong>the</strong>U.S.-based Global <strong>Internet</strong> <strong>Freedom</strong>Consortium (GIFC), an organizationrun by <strong>the</strong> Falun Gong, a Ch<strong>in</strong>esespiritual group that Beij<strong>in</strong>g labels aterrorist organization. The softwareis aimed at enabl<strong>in</strong>g users <strong>in</strong> Ch<strong>in</strong>ato puncture <strong>the</strong> regime’s Great Firewall,but it has also been accessedby users <strong>in</strong> o<strong>the</strong>r countries; morethan a million Iranian users reportedlyemployed it <strong>in</strong> June 2009. 94Freegate and its sister software, Ultrasurf,also developed by <strong>the</strong> GIFC,report that <strong>the</strong>y have, comb<strong>in</strong>ed,500,000 to 1 million monthly users. 95In 2010, <strong>the</strong> State Department transferred1.5 million dollars to <strong>the</strong> Broadcast<strong>in</strong>gBoard of Governors (BBG) tosupport Freegate and ano<strong>the</strong>r GIFCtool, Ultrareach, draw<strong>in</strong>g a predictablyangry response from Beij<strong>in</strong>g.A Ch<strong>in</strong>ese government spokespersonsaid <strong>the</strong> GIFC and Falun Gongare “bent on vilify<strong>in</strong>g <strong>the</strong> Ch<strong>in</strong>esegovernment with fabricated lies,underm<strong>in</strong><strong>in</strong>g Ch<strong>in</strong>ese social stabilityand sabotag<strong>in</strong>g Ch<strong>in</strong>a-U.S. relations”and that <strong>the</strong> Ch<strong>in</strong>ese government is“strongly opposed to <strong>the</strong> U.S. governmentprovid<strong>in</strong>g whatever assistanceto such an anti-Ch<strong>in</strong>a organization.” 96GIFC supporters have lobbied CapitolHill for f<strong>in</strong>ancial support to expandits exist<strong>in</strong>g <strong>in</strong>frastructure, not<strong>in</strong>gthat GIFC had to restrict use of <strong>the</strong>software by Iranians not long after <strong>the</strong>2009 protests subsided because oflimited server capacity.Fund<strong>in</strong>g groups associated with <strong>the</strong>Falun Gong poses obvious complicationsfor U.S. relations with Ch<strong>in</strong>a. GivenBeij<strong>in</strong>g’s deeply negative view of<strong>the</strong> spiritual group, support<strong>in</strong>g FalunGong volunteers as <strong>the</strong>y circumvent<strong>the</strong> Ch<strong>in</strong>ese firewall stresses <strong>the</strong> countries’complex bilateral ties. Indeed,some see <strong>the</strong> State Department’sdecision to fund Freegate through<strong>the</strong> BBG as an attempt to distance itsdiplomatic efforts from its support forGIFC-related efforts. 97 Given <strong>the</strong> highperformance of <strong>the</strong>se technologiesand <strong>the</strong>ir popularity, stress on <strong>the</strong>relationship may be worth <strong>the</strong> costto <strong>the</strong> United States, but as fund<strong>in</strong>gfor new programm<strong>in</strong>g cont<strong>in</strong>ues to<strong>in</strong>crease, <strong>the</strong> government shouldmake a concerted effort to diversify<strong>the</strong> technologies it supports.| 25
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>26 |basic technical tra<strong>in</strong><strong>in</strong>g teaches users how toidentify and verify certificate authorities andSecure Socket Layer (SSL) certificates – <strong>the</strong> popupboxes that verify <strong>the</strong> au<strong>the</strong>nticity and securityof a website – to help m<strong>in</strong>imize <strong>the</strong> number ofstate surveillance <strong>in</strong>trusions that users <strong>in</strong>advertentlyauthorize. Still o<strong>the</strong>r programs teach basic“cyber hygiene” practices to activists who maynot be technologically proficient, which <strong>in</strong>cludeconstruct<strong>in</strong>g strong passwords, avoid<strong>in</strong>g keystrokelogg<strong>in</strong>g <strong>in</strong> <strong>Internet</strong> cafes, prevent<strong>in</strong>g <strong>the</strong><strong>in</strong>advertent download of malicious code and us<strong>in</strong>gHypertext Transfer Protocol Secure (HTTPS),which encrypts onl<strong>in</strong>e sessions.The State Department has spent approximately 20million dollars s<strong>in</strong>ce 2008 on programs to developcircumvention technologies and promote digitalactivism, and planned to award more than 25 milliondollars <strong>in</strong> additional fund<strong>in</strong>g <strong>in</strong> 2011. 98 TheState Department has been criticized for delays <strong>in</strong>disburs<strong>in</strong>g fund<strong>in</strong>g for <strong>Internet</strong>-freedom relatedtechnologies. Accord<strong>in</strong>g to a congressional report,<strong>the</strong> State Department received 50 million dollars <strong>in</strong>appropriations for <strong>Internet</strong> freedom programm<strong>in</strong>gs<strong>in</strong>ce Fiscal Year 2008, but had disbursed less thanhalf by February 2011. 99 Partly as a result, <strong>in</strong> April2011 Congress reallocated 10 million dollars from<strong>the</strong> State Department to <strong>the</strong> Broadcast<strong>in</strong>g Board ofGovernors (BBG) – which reduced State’s <strong>Internet</strong>freedom budget by a third and more than qu<strong>in</strong>tupled<strong>the</strong> BBG’s budget <strong>in</strong> this area. Separately,<strong>the</strong> Defense Advanced Research Projects <strong>Age</strong>ncy(DARPA), which is part of <strong>the</strong> Department ofDefense, funds <strong>the</strong> development of circumventiontechnologies that would allow <strong>the</strong> U.S. military toaccess <strong>the</strong> <strong>Internet</strong> safely and anonymously. 100There are good reasons for <strong>the</strong> BBG to take <strong>the</strong>lead on provid<strong>in</strong>g most circumvention and anonymitytechnologies. It is an operational entitythat currently provides an array of circumventiontechnologies, and develops some of <strong>the</strong>m<strong>in</strong>-house. Should State and <strong>the</strong> BBG both fundcircumvention technologies, <strong>the</strong>y will likely endup fund<strong>in</strong>g <strong>the</strong> same outside groups. State will,however, need to cont<strong>in</strong>ue support<strong>in</strong>g circumventiontechnologies whose use falls outside <strong>the</strong> BBG’smission of promot<strong>in</strong>g U.S. government-sponsored<strong>in</strong>ternational broadcast<strong>in</strong>g. State has proposedfund<strong>in</strong>g projects such as mobile security applicationsand ad-hoc mesh network<strong>in</strong>g (decentralizednetworks that rely on <strong>in</strong>dividual nodes to transmitdata) for use when <strong>the</strong> <strong>Internet</strong> is shut down, which<strong>in</strong>clude both circumvention and anonymiz<strong>in</strong>gcomponents. State should also reta<strong>in</strong> <strong>the</strong> lead onsupport<strong>in</strong>g o<strong>the</strong>r technologies that fall outside <strong>the</strong>BBG’s mission and current technical competence,<strong>in</strong>clud<strong>in</strong>g tools to establish secure human rightsdatabases, onl<strong>in</strong>e hubs for censored comment, andso on. 101Shap<strong>in</strong>g International NormsThe Bush and Obama adm<strong>in</strong>istrations have bothsought to promote <strong>Internet</strong> freedom by shap<strong>in</strong>g<strong>in</strong>ternational norms. Develop<strong>in</strong>g <strong>in</strong>ternationalnorms is a long-term, global objective. Somecountries that currently repress that <strong>Internet</strong>access – like Ch<strong>in</strong>a, Iran and Burma – areunlikely to be moved by normative trends <strong>in</strong> <strong>the</strong>near term; statements at <strong>the</strong> United Nations andpolicy declarations support<strong>in</strong>g <strong>Internet</strong> freedomare highly unlikely to change <strong>the</strong>ir current policies.But promot<strong>in</strong>g <strong>Internet</strong> freedom is not onlya near-term effort, and current efforts may pay off<strong>in</strong> <strong>the</strong> long run. Many countries have not yet fullydeveloped <strong>the</strong>ir own <strong>Internet</strong> policies or thoughtthrough all of <strong>the</strong> implications of <strong>Internet</strong>freedom and repression even <strong>in</strong> <strong>the</strong> short run –<strong>in</strong>clud<strong>in</strong>g states <strong>in</strong> Central Asia, <strong>the</strong> Middle Eastand Africa. Shap<strong>in</strong>g <strong>the</strong> behavior of those statesshould be an important goal of <strong>the</strong> United Statesand likem<strong>in</strong>ded partners.Ra<strong>the</strong>r than advocat<strong>in</strong>g a new <strong>in</strong>ternational treatyor new regimes, <strong>the</strong> U.S. government has arguedthat <strong>the</strong> pr<strong>in</strong>ciples of <strong>Internet</strong> freedom already exist<strong>in</strong> <strong>the</strong> UDHR and <strong>the</strong> International Covenant on
Civil and Political Rights. Article 19 of <strong>the</strong> UDHRstates that <strong>the</strong> right to free expression exists <strong>in</strong> anymedium and on any frontier, and Article 20 protects<strong>the</strong> right of everyone to peacefully assembleand associate, a right that Cl<strong>in</strong>ton has argued isguaranteed <strong>in</strong> cyberspace as well. 102At <strong>the</strong> same time, <strong>the</strong> U.S. government has triedto codify norms that would re<strong>in</strong>force free expressionand block efforts to restrict it. The 2005 WorldSummit on <strong>the</strong> Information Society (WSIS), aU.N.-sponsored ga<strong>the</strong>r<strong>in</strong>g of 174 countries, produceda consensus statement recogniz<strong>in</strong>g that“freedom of expression and <strong>the</strong> free flow of <strong>in</strong>formation,ideas and knowledge, are essential for<strong>the</strong> Information Society and beneficial to development.”103 In 2008, <strong>the</strong> member states of <strong>the</strong>International Telecommunication Union (ITU)adopted a resolution pledg<strong>in</strong>g to “refra<strong>in</strong> from tak<strong>in</strong>gany unilateral and/or discrim<strong>in</strong>atory actionsthat could impede ano<strong>the</strong>r Member State to accesspublic <strong>Internet</strong> sites.” Accord<strong>in</strong>g to AmbassadorDavid Gross, <strong>the</strong>n <strong>the</strong> top State Department officialmanag<strong>in</strong>g communications and <strong>in</strong>formationpolicy, <strong>the</strong> deliberations made clear that “memberstates” meant not only governments, but also <strong>the</strong>civilians of those countries. 104Cont<strong>in</strong>ued U.S. leadership is critical to fill whatrema<strong>in</strong>s a normative vacuum. Part of <strong>the</strong> difficulty,however, lies not only with authoritarianregimes, but also with some of America’s closestdemocratic partners. While <strong>the</strong> U.S. governmentrecognizes some limits on free expression – childpornography, slander, perjury, “fight<strong>in</strong>g words”and certa<strong>in</strong> o<strong>the</strong>r forms of expression are illegal,onl<strong>in</strong>e or off – its commitment to free speech isnever<strong>the</strong>less <strong>the</strong> strongest of any major country.Germany, for <strong>in</strong>stance, prohibits Holocaustdenial onl<strong>in</strong>e; France does not allow <strong>the</strong> sale ofNazi paraphernalia over <strong>the</strong> <strong>Internet</strong>; and Turkeybanned YouTube for two years because it refusedto remove videos <strong>the</strong> courts deemed <strong>in</strong>sult<strong>in</strong>g toMustafa Kemal Ataturk. Governments <strong>in</strong> Brita<strong>in</strong>,Italy and Germany have also established lists ofblocked websites – particularly those conta<strong>in</strong><strong>in</strong>gchild pornography, onl<strong>in</strong>e gambl<strong>in</strong>g or hate speech– but <strong>the</strong>se lists are often nei<strong>the</strong>r transparent noraccountable to <strong>the</strong> public. 105Authoritarian countries <strong>in</strong>evitably attempt toshield <strong>the</strong>mselves from criticism and pressure bypo<strong>in</strong>t<strong>in</strong>g to democracies that ban onl<strong>in</strong>e speech.Deny<strong>in</strong>g <strong>the</strong>m <strong>the</strong> opportunity to do so successfullyrequires <strong>the</strong> United States and o<strong>the</strong>rs toarticulate, publicly and consistently, <strong>the</strong> dist<strong>in</strong>ctionbetween restrictions on free speech put <strong>in</strong>toplace by democratic political systems through dueprocess and those enacted by dictatorships. WhileAmericans may disagree with <strong>the</strong> limits on onl<strong>in</strong>eexpression enforced by democratic partners, <strong>the</strong>sedecisions are never<strong>the</strong>less made through participatorypolitical systems while restrictions imposed byautocratic regimes are not.Def<strong>in</strong><strong>in</strong>g “cyber security,” and determ<strong>in</strong><strong>in</strong>g <strong>the</strong>legitimate steps a government may take to ensureit, also poses a significant challenge to America’s<strong>Internet</strong> freedom efforts. 106 Most democratic governmentsuse <strong>the</strong> term to mean protect<strong>in</strong>g aga<strong>in</strong>stassaults on and <strong>in</strong>trusion of cyber systems andcritical <strong>in</strong>frastructure, such as electric utilities,government servers, f<strong>in</strong>ancial systems and telecommunicationsnetworks. In contrast, some o<strong>the</strong>rgovernments argue that <strong>the</strong> term should <strong>in</strong>clude<strong>the</strong> notion of “<strong>in</strong>formation security” – regulat<strong>in</strong>gcontent. Russian officials, for example, haveemphasized that <strong>in</strong>formation security requiresbalanc<strong>in</strong>g <strong>in</strong>dividual, social and state <strong>in</strong>terests. 107Such notions have real world consequences:Russia’s federal security service recently proposedbann<strong>in</strong>g Skype, Gmail and o<strong>the</strong>r platforms because<strong>the</strong>y are “uncontrolled” platforms that use encryptiontechnology for secure communication. 108 TheUnited Arab Emirates made similar claims <strong>in</strong> 2010when it banned <strong>the</strong> use of BlackBerry services,compla<strong>in</strong><strong>in</strong>g that it could not access encryptedcommunications. 109| 27
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>28 |Similarly, compet<strong>in</strong>g def<strong>in</strong>itions of aggressioncomplicate efforts to develop <strong>Internet</strong> freedomnorms. At an April 2008 U.N. conference, a seniorRussian official argued that “any time a governmentpromotes ideas on <strong>the</strong> <strong>Internet</strong> with <strong>the</strong> goalof subvert<strong>in</strong>g ano<strong>the</strong>r country’s government – even<strong>in</strong> <strong>the</strong> name of democratic reform – it shouldqualify as ‘aggression.’” 110 In 2009, <strong>the</strong> six-memberShanghai Cooperation Organisation – which<strong>in</strong>cludes Russia and Ch<strong>in</strong>a – adopted an accordthat reportedly def<strong>in</strong>ed “<strong>in</strong>formation war,” <strong>in</strong>part, as an effort by a state to underm<strong>in</strong>e ano<strong>the</strong>r’s“political, economic and social systems.” 111The same tensions exist <strong>in</strong> work<strong>in</strong>g with Americanpartners to combat onl<strong>in</strong>e crime. The AdditionalProtocol to <strong>the</strong> European Convention on Cybercrime,for example, provides a mechanism for states toharmonize <strong>the</strong>ir domestic laws relat<strong>in</strong>g to varioustypes of cybercrime. At first glance, this would seemprecisely <strong>the</strong> k<strong>in</strong>d of effort that <strong>the</strong> United Statesshould support on security grounds. Yet <strong>the</strong> protocolrequires signatories to crim<strong>in</strong>alize such activities asdistribut<strong>in</strong>g xenophobic or racist material through acomputer system; express<strong>in</strong>g denial, “gross m<strong>in</strong>imization”or approval of a genocide or crimes aga<strong>in</strong>sthumanity through a computer; distribut<strong>in</strong>g <strong>in</strong>sults topeople because of <strong>the</strong>ir race, color, religion, nationalor ethnic orig<strong>in</strong> through a computer system; or aid<strong>in</strong>gand abett<strong>in</strong>g any of <strong>the</strong>se acts. The AdditionalProtocol has been signed by Albania, Cyprus,Denmark, France, Slovenia and Switzerland. While<strong>the</strong> United States ratified <strong>the</strong> underly<strong>in</strong>g convention<strong>in</strong> 2006, it has decl<strong>in</strong>ed to jo<strong>in</strong> <strong>the</strong> AdditionalProtocol, believ<strong>in</strong>g it to be <strong>in</strong>consistent with U.S.constitutional guarantees. 112Efforts to enlist <strong>Internet</strong> service providers ando<strong>the</strong>r technology companies to enforce regulationsprotect<strong>in</strong>g copyrights and <strong>in</strong>tellectual propertyalso complicate U.S. efforts to build stronger globalsupport for <strong>Internet</strong> freedom. Intermediaries– <strong>in</strong>clud<strong>in</strong>g <strong>Internet</strong> service providers, websitehost<strong>in</strong>g companies, social network<strong>in</strong>g and emailservice providers and search eng<strong>in</strong>es – are <strong>in</strong>creas<strong>in</strong>glypressured by states to regulate content <strong>the</strong>yhost. In <strong>the</strong> United States, an <strong>in</strong>dividual post<strong>in</strong>gillegal material is generally held liable ra<strong>the</strong>r than<strong>the</strong> <strong>in</strong>termediary. 113 In many foreign countries<strong>in</strong>termediaries do face liability, and <strong>the</strong> process bywhich <strong>the</strong>y are notified (by ei<strong>the</strong>r <strong>the</strong> governmentor private actors) is often unclear.The role of <strong>the</strong> private sectoris <strong>the</strong> s<strong>in</strong>gle most complicatedissue fac<strong>in</strong>g U.S. policymakersas <strong>the</strong>y forge an <strong>Internet</strong>freedom agenda.Hold<strong>in</strong>g <strong>the</strong>m liable <strong>in</strong> this way risks chill<strong>in</strong>g freeonl<strong>in</strong>e expression. In countries like France, where<strong>Internet</strong> service providers and o<strong>the</strong>rs are <strong>in</strong>creas<strong>in</strong>glyenforc<strong>in</strong>g copyright regulations, hosts mayself-police content and respond immediately totakedown notices, even those issued <strong>in</strong> bad faithor for unscrupulous purposes. 114 The United Statesand a number of o<strong>the</strong>r nations, <strong>in</strong>clud<strong>in</strong>g <strong>the</strong> EU,Japan and Mexico, are currently negotiat<strong>in</strong>g anAnti-Counterfeit<strong>in</strong>g Trade Agreement that willserve as an <strong>in</strong>ternational framework for enforc<strong>in</strong>g<strong>in</strong>tellectual property rights. In develop<strong>in</strong>g suchframeworks, <strong>the</strong> United States must be very waryof mov<strong>in</strong>g beyond current American law. Hold<strong>in</strong>g<strong>in</strong>termediaries responsible could underm<strong>in</strong>e <strong>the</strong>U.S. <strong>Internet</strong> freedom agenda by compell<strong>in</strong>g <strong>the</strong>mto err on <strong>the</strong> side of caution and to proactivelycensor, ban or remove even legal – let alone questionable– content.The United States must help formulate acceptable<strong>in</strong>ternational def<strong>in</strong>itions of cyber security, aggression,cybercrime and copyright enforcement that
espect <strong>the</strong> pr<strong>in</strong>ciples of <strong>Internet</strong> freedom. It willalso need to cont<strong>in</strong>ually articulate <strong>the</strong> dist<strong>in</strong>ctionbetween political speech permissible undersuch regimes as <strong>the</strong> UDHR and truly illicit onl<strong>in</strong>eactivity. This will likely <strong>in</strong>volve oppos<strong>in</strong>g effortsto develop restrictive <strong>in</strong>ternational norms spearheadedby some of America’s closest friends.Enlist<strong>in</strong>g Private Sector SupportThe role of <strong>the</strong> private sector is <strong>the</strong> s<strong>in</strong>gle mostcomplicated issue fac<strong>in</strong>g U.S. policymakers as <strong>the</strong>yforge an <strong>Internet</strong> freedom agenda. Private firmshave a duty to maximize profits ra<strong>the</strong>r than promoteonl<strong>in</strong>e freedom <strong>in</strong> repressive environments.Yet with <strong>the</strong> prom<strong>in</strong>ent role <strong>the</strong>ir products played<strong>in</strong> Iran, Egypt, Ch<strong>in</strong>a and elsewhere, companieshave been dragged <strong>in</strong>to <strong>the</strong> center of <strong>the</strong> <strong>Internet</strong>freedom debate, whe<strong>the</strong>r <strong>the</strong>y want to be <strong>the</strong>re ornot. Ethical debates about <strong>the</strong> proper role of <strong>the</strong>private sector – rang<strong>in</strong>g from whe<strong>the</strong>r Americancompanies should be permitted to sell repressiveregimes key technologies to <strong>the</strong> responsibilities ofcorporations <strong>in</strong> <strong>the</strong> face of a regime’s demand for<strong>in</strong>formation – rema<strong>in</strong> unresolved.The perception that American companies aid<strong>Internet</strong> repression abroad clearly makes promot<strong>in</strong>g<strong>Internet</strong> freedom more difficult. This isparticularly true for <strong>the</strong> most egregious activities,such as turn<strong>in</strong>g over <strong>the</strong> personal data of a dissidentto state security services. As we discuss below,Congress should ban such activities and requiremore transparency <strong>in</strong>to o<strong>the</strong>r corporate <strong>in</strong>volvement,such as provid<strong>in</strong>g lists of banned websites.Yet nearly seven years after <strong>the</strong> <strong>in</strong>itial hear<strong>in</strong>gs on<strong>Internet</strong> companies <strong>in</strong> Ch<strong>in</strong>a began, no legislation<strong>in</strong> this area has passed.Both corporations and policymakers are struggl<strong>in</strong>gto def<strong>in</strong>e <strong>the</strong> appropriate role of companies <strong>in</strong> promot<strong>in</strong>g<strong>Internet</strong> freedom. For example, Cisco hasbeen accused of market<strong>in</strong>g routers <strong>in</strong> Ch<strong>in</strong>a thatare used to support <strong>the</strong> Great Firewall. 115 For severalyears Google censored its own search results <strong>in</strong>Ch<strong>in</strong>a. More recently, <strong>the</strong> computer security firmMcAfee Inc. provided content-filter<strong>in</strong>g software to<strong>Internet</strong> service providers <strong>in</strong> Bahra<strong>in</strong>, Saudi Arabiaand Kuwait. 116 Ch<strong>in</strong>a’s Huawei is a significant supplierof filter<strong>in</strong>g technology. Telecommunicationsgiant Nokia allegedly provided <strong>the</strong> Iranian governmentwith <strong>the</strong> capability to tap mobile phones,<strong>in</strong>terrupt calls and <strong>in</strong>tercept and scramble SMS textmessages to disrupt organized protests. 117 France’sAlcatel reportedly sold website filter<strong>in</strong>g and surveillanceequipment to Burma, 118 and Canada’sNortel Networks has allegedly provided censorshiptechnology to <strong>the</strong> Ch<strong>in</strong>ese government. 119The problem is that companies must follow locallaws when <strong>the</strong>y operate <strong>in</strong> foreign countries,<strong>in</strong>clud<strong>in</strong>g laws restrict<strong>in</strong>g onl<strong>in</strong>e behavior <strong>in</strong>authoritarian states. If <strong>the</strong>y do not comply, <strong>the</strong>firms risk los<strong>in</strong>g <strong>the</strong>ir licenses and access to thosemarkets. Many observers have po<strong>in</strong>ted to Google’sdecision to withdraw from Ch<strong>in</strong>a ra<strong>the</strong>r than cont<strong>in</strong>ueto accept Ch<strong>in</strong>ese government restrictionsas an example of a pr<strong>in</strong>cipled corporate stand thato<strong>the</strong>rs should emulate. But <strong>in</strong>dustry representativespa<strong>in</strong>t a more complicated picture. Fledgl<strong>in</strong>gtelecommunications and technology companieswithout large revenue streams – or even largerfirms that do not boast tremendous f<strong>in</strong>ancialassets – may f<strong>in</strong>d <strong>the</strong> need to stay engaged <strong>in</strong>Ch<strong>in</strong>a, <strong>the</strong> world’s largest <strong>Internet</strong> market, a questionof life or death.The perception that American firms <strong>the</strong>mselves arean arm of American foreign policy also jeopardizes<strong>the</strong>ir ability to compete <strong>in</strong> key foreign markets.Dur<strong>in</strong>g <strong>the</strong> 2009 Iranian revolution, for <strong>in</strong>stance,Jared Cohen, <strong>the</strong>n a member of Cl<strong>in</strong>ton’s policyplann<strong>in</strong>g staff, emailed Twitter founder Jack Dorseyurg<strong>in</strong>g <strong>the</strong> company to forgo a planned site outageso that Iranians could cont<strong>in</strong>ue tweet<strong>in</strong>g. Thisaction attracted disapproval even <strong>in</strong> <strong>the</strong> UnitedStates, but it is consistent with <strong>the</strong> U.S. policy ofpromot<strong>in</strong>g <strong>Internet</strong> freedom. The U.S. governmentrout<strong>in</strong>ely reaches out to private firms and this will| 29
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>30 |constitute an <strong>in</strong>creas<strong>in</strong>gly important element ofAmerica’s <strong>Internet</strong> freedom agenda. Yet, some ofthose who have criticized <strong>the</strong> State Department’soutreach to Twitter also call on <strong>the</strong> government tourge corporations to jo<strong>in</strong> <strong>the</strong> GNI.Permitt<strong>in</strong>g U.S. companies to operate <strong>in</strong> certa<strong>in</strong>authoritarian countries ra<strong>the</strong>r than cede <strong>the</strong> marketto <strong>the</strong> alternatives can serve America’s <strong>Internet</strong>freedom agenda <strong>in</strong> <strong>the</strong> long term. For example,while Google censored its search results <strong>in</strong> ma<strong>in</strong>landCh<strong>in</strong>a, Baidu – Ch<strong>in</strong>a’s largest domesticsearch eng<strong>in</strong>e – has even more str<strong>in</strong>gent censorshippolicies, and has taken over much of <strong>the</strong> marketshare Google abandoned. A policy change likeGoogle’s might lead to less <strong>in</strong>formation availableonl<strong>in</strong>e to <strong>the</strong> average Ch<strong>in</strong>ese citizen, not more.And a transaction between two foreign parties overwhich <strong>the</strong> United States has no visibility or controlcould quite conceivably faclitate <strong>Internet</strong> repressionmore than <strong>the</strong> activities of an American companythat are, at <strong>the</strong> end of <strong>the</strong> day, subject to U.S. lawand public op<strong>in</strong>ion pressures.As technology companies <strong>in</strong>creas<strong>in</strong>gly expand <strong>in</strong>torepressive foreign countries, <strong>the</strong>y will face heightenedpressure from Congress and <strong>the</strong> public tomake <strong>in</strong>ternal decisions with an eye toward <strong>the</strong>irbroader implications. Facebook, for example, hasrequired users to register <strong>the</strong>ir accounts under<strong>the</strong>ir real names – clearly a deterrent to dissidentswho wish to rema<strong>in</strong> anonymous. This has been aparticular po<strong>in</strong>t of contention between Facebookand <strong>Internet</strong> freedom advocates, because it potentiallyallows for regime allies to have activists us<strong>in</strong>galiases suspended from <strong>the</strong> site.In 2008, a coalition of nonprofit organizations,universities and f<strong>in</strong>ancial <strong>in</strong>stitutions, nearlyall American, jo<strong>in</strong>ed with Google, Yahoo andMicrosoft to form <strong>the</strong> GNI, which attempts tocodify bus<strong>in</strong>ess codes of conduct. GNI memberscommit to “collaborate <strong>in</strong> <strong>the</strong> advancementof user rights to freedom of expression andprivacy.” 120 Participants agree to adhere to a setof shared pr<strong>in</strong>ciples about how companies shouldrespond to government requests for <strong>in</strong>formation,<strong>in</strong>clud<strong>in</strong>g mak<strong>in</strong>g those requests transparentand protect<strong>in</strong>g users’ rights to privacy. The GNI<strong>in</strong>cludes a report<strong>in</strong>g and enforcement mechanismto ensure that its members meet its complianceand evaluation requirements. 121While many view <strong>the</strong> GNI as a great step forward<strong>in</strong> <strong>the</strong> <strong>Internet</strong> freedom movement, its effects havebeen significantly limited by <strong>the</strong> lack of corporateparticipants. Not a s<strong>in</strong>gle technology companyhas jo<strong>in</strong>ed <strong>the</strong> three founders, each of which is anAmerican firm. The Secretary of State has publiclycalled on technology companies to jo<strong>in</strong> <strong>the</strong><strong>in</strong>itiative, and members of Congress have done<strong>the</strong> same; <strong>in</strong> August 2009, Sen. Richard Durb<strong>in</strong>,D-Ill., wrote to 26 companies urg<strong>in</strong>g <strong>the</strong>m to jo<strong>in</strong><strong>the</strong> GNI.122 All has been for naught. Corporaterepresentatives with whom we spoke observed that<strong>the</strong>ir companies agreed with <strong>the</strong> pr<strong>in</strong>ciples putforth by <strong>the</strong> GNI, but <strong>the</strong>y simply do not see it <strong>in</strong><strong>the</strong>ir bus<strong>in</strong>ess <strong>in</strong>terest to jo<strong>in</strong> because <strong>the</strong>y do notwish to expend <strong>the</strong> resources necessary to fulfill<strong>the</strong> GNI’s report<strong>in</strong>g requirements or submit <strong>the</strong>ircorporate practices to external reviews. O<strong>the</strong>rsexpressed concern that jo<strong>in</strong><strong>in</strong>g <strong>the</strong> GNI couldthreaten <strong>the</strong>ir access to particular markets becauseGNI is perceived as an organization for promot<strong>in</strong>gAmerican values.In an encourag<strong>in</strong>g trend, a few companies haveproactively sought to break through <strong>Internet</strong>repression. When Egypt shut down <strong>the</strong> <strong>Internet</strong>almost completely, a French company offeredEgyptians anonymous dial-up access via aFrench phone number. 123 At <strong>the</strong> same time,Google and Twitter jo<strong>in</strong>tly created a tool,Speak2Tweet, which allowed Egyptians to calla dedicated number that translated <strong>the</strong>ir voicemessages <strong>in</strong>to tweets. Google officials noted that<strong>the</strong> <strong>in</strong>itiative was a direct response to <strong>the</strong> events<strong>in</strong> <strong>the</strong> Middle East, say<strong>in</strong>g, “We hope this will
go some way to help<strong>in</strong>g people stay connectedat this very difficult time.” 124 Dur<strong>in</strong>g <strong>the</strong> revolution<strong>in</strong> Libya, <strong>the</strong> Moammar Gadhafi regime cut<strong>Internet</strong> access and jammed cellular networksand satellite phone signals. A Libyan-Americantelecommunications executive led a team thatimported millions of dollars <strong>in</strong> equipment,hijacked <strong>the</strong> national network and reestablishedcommunications <strong>in</strong> <strong>the</strong> country. 125Increas<strong>in</strong>g Economic IncentivesIncreas<strong>in</strong>g <strong>the</strong> economic <strong>in</strong>centives to promote<strong>Internet</strong> freedom must be central to any U.S.government strategy. There are three majorways to do this: persuasion, publicity and tradeagreements.U.S. officials are try<strong>in</strong>g to persuade states that<strong>Internet</strong> repression will chill <strong>the</strong>ir economicdevelopment, and to persuade companies that<strong>Internet</strong> freedom issues affect <strong>the</strong>ir own f<strong>in</strong>ancial<strong>in</strong>terests and bottom l<strong>in</strong>es. Cl<strong>in</strong>ton has noted thata free <strong>Internet</strong>, by <strong>in</strong>creas<strong>in</strong>g transparency, canreduce corruption – mak<strong>in</strong>g a given economy amore predictable and profitable marketplace forbus<strong>in</strong>ess – and that by <strong>in</strong>vest<strong>in</strong>g <strong>in</strong> countries withtough censorship and surveillance policies, companiescan see <strong>the</strong>ir websites shut down or <strong>the</strong>ir staffthreatened. 126 Indeed, corporations will <strong>in</strong>creas<strong>in</strong>glyf<strong>in</strong>d <strong>the</strong>mselves navigat<strong>in</strong>g <strong>the</strong> complex webof <strong>Internet</strong> restrictions abroad, some of which willdirectly affect <strong>the</strong>ir balance sheets.Every time an American company complies with apolitically motivated order to block <strong>Internet</strong> contentor share user <strong>in</strong>formation, it risks negative publicity<strong>in</strong> <strong>the</strong> United States and elsewhere. As negativepublicity builds, Congress may pass laws that wouldprohibit American companies from aid<strong>in</strong>g certa<strong>in</strong>forms of <strong>Internet</strong> repression which could requirecompanies to withdraw from foreign markets wherenational laws conflict with U.S. laws. As a result,corporations have an <strong>in</strong>terest <strong>in</strong> preempt<strong>in</strong>g suchsituations by press<strong>in</strong>g foreign governments for moreliberal <strong>Internet</strong> environments – or at least fewerconstra<strong>in</strong>ts – and U.S. government officials shouldencourage <strong>the</strong>m to do so.The U.S. government can also promote <strong>Internet</strong>freedom though trade agreements where <strong>Internet</strong>repression serves as a trade barrier. When a countryblocks access to a U.S. website, for example, it alsoblocks <strong>the</strong> site’s advertis<strong>in</strong>g – and <strong>the</strong>reby <strong>in</strong>terfereswith <strong>the</strong> trade <strong>in</strong> products and services advertised. 127Of <strong>the</strong> millions of dollars lost dur<strong>in</strong>g <strong>the</strong> <strong>Internet</strong>shutoff <strong>in</strong> Egypt, it is hard to imag<strong>in</strong>e that Americanbus<strong>in</strong>esses were not also affected.Employ<strong>in</strong>g trade agreements is a more promis<strong>in</strong>gstrategy than demand<strong>in</strong>g foreign governments toadhere to universal values, because <strong>the</strong>y conta<strong>in</strong>economic <strong>in</strong>centives (thus giv<strong>in</strong>g <strong>the</strong> United Statesnegotiat<strong>in</strong>g leverage) and are at least potentiallyenforceable. Should <strong>Internet</strong> censorship becomeaccepted as a non-tariff trade barrier, a censor<strong>in</strong>ggovernment could be vulnerable to dispute arbitrationat <strong>the</strong> World Trade Organization or bilateraltrade remedies. And such agreements could bebilateral, multilateral or even global.The United States should more actively try to<strong>in</strong>sert b<strong>in</strong>d<strong>in</strong>g language <strong>in</strong> agreements that wouldprohibit <strong>Internet</strong> censorship or o<strong>the</strong>r efforts tolimit access to <strong>in</strong>formation onl<strong>in</strong>e. The UnitedStates did <strong>in</strong>clude a relevant provision <strong>in</strong> <strong>the</strong>Korea-U.S. Free Trade Agreement, approved byCongress <strong>in</strong> December 2010. That agreementstates <strong>in</strong> part: “Recogniz<strong>in</strong>g <strong>the</strong> importance of<strong>the</strong> free flow of <strong>in</strong>formation <strong>in</strong> facilitat<strong>in</strong>g trade,and acknowledg<strong>in</strong>g <strong>the</strong> importance of protect<strong>in</strong>gpersonal <strong>in</strong>formation, <strong>the</strong> Parties shall endeavorto refra<strong>in</strong> from impos<strong>in</strong>g or ma<strong>in</strong>ta<strong>in</strong><strong>in</strong>g unnecessarybarriers to electronic <strong>in</strong>formation flows acrossborders.” 128 Such language is clearly nonb<strong>in</strong>d<strong>in</strong>g –“shall endeavor to refra<strong>in</strong>” is a loose commitmentat best – but never<strong>the</strong>less suggests how <strong>the</strong> UnitedStates can promote <strong>Internet</strong> freedom <strong>in</strong> futuretrade negotiations.| 31
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>32 |Reform<strong>in</strong>g Export ControlsThe U.S. government can also reform its exportcontrols on <strong>in</strong>formation technologies to fur<strong>the</strong>rits <strong>Internet</strong> freedom objectives. Discussionsabout <strong>the</strong> l<strong>in</strong>k between <strong>the</strong> public and privatesectors <strong>in</strong> promot<strong>in</strong>g <strong>Internet</strong> freedom havefocused on whe<strong>the</strong>r <strong>the</strong> U.S. government shouldprohibit <strong>the</strong> supply of technology and equipmentto repressive governments. But <strong>the</strong> governmentmust also ensure that it does not prohibit <strong>the</strong>export of technology that could be used to promoteonl<strong>in</strong>e freedom.For years <strong>the</strong> United States has relied on controlsenforced by <strong>the</strong> Departments of Commerce andTreasury to regulate overseas sales of merchandiseand materials to states that pose a threat to U.S.national and economic security. These controlsrestrict exports of sensitive computer hardwareand software, such as cryptographic programsand o<strong>the</strong>r technologies that scramble messagesand data, <strong>in</strong> part to prevent unfriendly states fromacquir<strong>in</strong>g cyber capabilities that could be usedaga<strong>in</strong>st <strong>the</strong> United States or its allies. Until recently,basic <strong>Internet</strong> services (such as email and <strong>in</strong>stantmessage services) could not be exported to statessuch as Cuba, Iran, Syria and Sudan.In March 2010, <strong>the</strong> Treasury Department issueda general license for <strong>Internet</strong> service technologiesthat would allow companies to export photoshar<strong>in</strong>g and o<strong>the</strong>r social network<strong>in</strong>g and communicationsservices to users <strong>in</strong> Cuba, Iran andSudan – a move adm<strong>in</strong>istration officials citedexplicitly as be<strong>in</strong>g part of <strong>the</strong>ir <strong>Internet</strong> freedomagenda. 129 In June 2010, <strong>the</strong> CommerceDepartment elim<strong>in</strong>ated export restrictions onmost mass-market electronic products wi<strong>the</strong>ncryption functions, <strong>in</strong>clud<strong>in</strong>g cellphones,laptops and computer drives, which can now beexported without a license. 130Yet export controls rema<strong>in</strong> burdensome for<strong>Internet</strong> freedom. Adm<strong>in</strong>istration officials haveprivately stated that complex and overlapp<strong>in</strong>gexport control regulations chill commercialactivity, especially with technology developers.U.S. export controls currently restrict, for<strong>in</strong>stance, <strong>the</strong> transferr<strong>in</strong>g, transmitt<strong>in</strong>g anddownload<strong>in</strong>g of open source code that is alreadywidely available for free onl<strong>in</strong>e. 131 This opensource code <strong>in</strong>cludes encryption code for securecommunications and a suite of o<strong>the</strong>r tools thatcould potentially give cyber-dissidents and o<strong>the</strong>ronl<strong>in</strong>e activists a wider range of options forcommunicat<strong>in</strong>g securely and access<strong>in</strong>g bannedcontent. But a strict <strong>in</strong>terpretation of currentexport controls requires websites that host opensource code, such as Google and Mozilla, toblock access to <strong>Internet</strong> Protocol (IP) addressesorig<strong>in</strong>at<strong>in</strong>g <strong>in</strong> sanctioned countries.In March 2010, <strong>the</strong> TreasuryDepartment issued a generallicense for <strong>Internet</strong> servicetechnologies that wouldallow companies to exportphoto shar<strong>in</strong>g and o<strong>the</strong>rsocial network<strong>in</strong>g andcommunications servicesto users <strong>in</strong> Cuba, Iran andSudan.Currently, when <strong>the</strong> State Department funds aparticular technology, <strong>the</strong> developer receives aspecific license that waives export controls onthat technology – so that it can, for example,provide circumvention technology to Iranians
and Syrians. Yet <strong>the</strong> license does not apply to<strong>the</strong> same technology if it is created and exportedby an organization that does not receive StateDepartment funds. The U.S. government shouldquickly fix this glar<strong>in</strong>g <strong>in</strong>consistency.V. Navigat<strong>in</strong>g <strong>the</strong> TensionsBetween <strong>Internet</strong> <strong>Freedom</strong>and Cyber SecurityBalanc<strong>in</strong>g <strong>the</strong> pr<strong>in</strong>ciple of freedom of expressionon <strong>the</strong> <strong>Internet</strong>, <strong>in</strong> which users can act anonymously,with <strong>the</strong> need for a secure environment <strong>in</strong>which malicious users seek<strong>in</strong>g to do harm can beidentified and stopped by responsible governments,is a difficult challenge. Indeed, policymakers todayare engaged <strong>in</strong> two simultaneous and potentiallycontradictory efforts. Promot<strong>in</strong>g <strong>Internet</strong> freedomimplies advocat<strong>in</strong>g privacy and provid<strong>in</strong>g toolsthrough which <strong>in</strong>dividuals can act anonymouslyonl<strong>in</strong>e. Cyber security, by contrast, implies onl<strong>in</strong>etransparency and attribution. These two effortscreate tensions that are not well understood andfrequently rema<strong>in</strong> unaddressed. Part of <strong>the</strong> problemstems from <strong>the</strong> fact that conversations aboutAmerica’s cyber security and <strong>Internet</strong> freedompolicies have, by and large, taken place <strong>in</strong> isolationfrom each o<strong>the</strong>r. Cyber security policy has <strong>in</strong>volved<strong>the</strong> national security community, while <strong>Internet</strong>freedom policies have <strong>in</strong>volved <strong>the</strong> technologycommunity and a handful of human rights activists– and now <strong>the</strong> foreign policy community.These tensions are real and will sometimes forcedifficult choices, but <strong>the</strong>y should not prevent<strong>the</strong> United States from secur<strong>in</strong>g cyberspace andpromot<strong>in</strong>g <strong>Internet</strong> freedom at <strong>the</strong> same time. U.S.policies will have to address two key tensions: anonymityversus attribution, and defend<strong>in</strong>g aga<strong>in</strong>stattacks versus embolden<strong>in</strong>g autocracies.Anonymity versus AttributionCyber security proponents often advocate greatertransparency <strong>in</strong> onl<strong>in</strong>e behavior and seek toimprove <strong>the</strong> ability of security monitors to reliablyidentify malicious users and track <strong>the</strong>ir activities.“Anonymity is <strong>the</strong> fundamental problem we face <strong>in</strong>cyberspace,” Stewart Baker, former chief counselfor <strong>the</strong> National Security <strong>Age</strong>ncy (NSA), said atan April 2010 <strong>Internet</strong> conference <strong>in</strong> Germany. 132| 33
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>34 |Security practitioners argue that onl<strong>in</strong>e transparencyand attribution allows law enforcement top<strong>in</strong>po<strong>in</strong>t <strong>the</strong> orig<strong>in</strong>s of cyber attacks and <strong>in</strong>trusionsand respond to <strong>the</strong>m, which could also deter futuremalicious activities. Former Director of NationalIntelligence Mike McConnell has argued for mak<strong>in</strong>g<strong>the</strong> <strong>Internet</strong> more transparent, say<strong>in</strong>g, “Weneed to re-eng<strong>in</strong>eer <strong>the</strong> <strong>Internet</strong> to make attribution,geo-location, <strong>in</strong>telligence analysis and impactassessment – who did it, from where, why and whatwas <strong>the</strong> result – more manageable.” 133Such efforts would conflict with <strong>the</strong> <strong>Internet</strong> freedomagenda, which emphasizes onl<strong>in</strong>e anonymity.The Tor network described previously, for example,does not have a back door through which <strong>the</strong> U.S.government or o<strong>the</strong>r law enforcement agencies canaccess and monitor <strong>the</strong> secured communication orWeb traffic. Experts argue that because <strong>the</strong> softwareis open source, users would identify any backdoor <strong>in</strong> <strong>the</strong> source code, compromis<strong>in</strong>g <strong>the</strong> software’s<strong>in</strong>tegrity and prompt<strong>in</strong>g users to f<strong>in</strong>d o<strong>the</strong>rprograms without a back door. Crim<strong>in</strong>al networksand o<strong>the</strong>rs seek<strong>in</strong>g to monitor law enforcementusers could also exploit any back door thatbypasses <strong>the</strong> controls and audit<strong>in</strong>g functions andhijack <strong>in</strong>formation of those monitor<strong>in</strong>g <strong>the</strong>m.Anonymous <strong>Internet</strong> use not only causes cybersecurity concerns; it can also threaten o<strong>the</strong>r aspectsof American national security. Technologies suchas Tor, for <strong>in</strong>stance, could be used not only bydissidents and democracy activists, but also bycrim<strong>in</strong>als and terrorists. 134 The very anonymiz<strong>in</strong>gtools and po<strong>in</strong>t-to-po<strong>in</strong>t encrypted communicationtechnology funded by <strong>the</strong> State Department andBBG could, some experts caution, be used by <strong>in</strong>ternationalterrorist organizations to coord<strong>in</strong>ate andcarry out attacks undetected by U.S. governmentsecurity agencies. 135 Although not react<strong>in</strong>g specificallyto government-funded anonymity tools, foryears <strong>the</strong> FBI has warned about <strong>the</strong> potential risksassociated with <strong>the</strong> spread of sophisticated encryptiontechnologies. 136 As early as 1993, <strong>the</strong> NSAdeveloped a “Clipper chip” designed for telecommunicationscompanies to use <strong>in</strong> secure voicetransmissions – but with a back door for <strong>the</strong> U.S.government. 137 (After a public outcry by privacyactivists, <strong>the</strong> program was abandoned.)O<strong>the</strong>r technologies pose potential challengesas well. BBG programs are <strong>in</strong>tended to provideforeigners access to its own onl<strong>in</strong>e materials – so,for <strong>in</strong>stance, a Ch<strong>in</strong>ese citizen can access newsstories on <strong>the</strong> Voice of America website that isblocked <strong>in</strong> Ch<strong>in</strong>a. However, while BBG-providedproxy servers and o<strong>the</strong>r technologies enable auser to access BBG websites, <strong>the</strong>y do not requireusers to stay <strong>the</strong>re. This facilitates peer-to-peercommunication among users, but it could alsoenable potential crim<strong>in</strong>als or terrorists to accesspropaganda or websites that teach bomb mak<strong>in</strong>gand o<strong>the</strong>r illicit skills. Similarly, activists seek<strong>in</strong>gto evade government surveillance can purchaseprepaid mobile phones that lack unique identifiers,and <strong>the</strong> U.S. government reportedly hopesto fund projects that enable mobile phone users toanonymously access <strong>the</strong> <strong>Internet</strong>. Because crim<strong>in</strong>alsand terrorists also seek to use such phones,however, a number of governments have begunoutlaw<strong>in</strong>g <strong>the</strong>m. 138U.S. government-supplied circumvention tools arenot <strong>the</strong> only option for <strong>in</strong>dividuals wish<strong>in</strong>g to communicateanonymously or access banned websites.Crim<strong>in</strong>als and terrorists are far more likely to usebotnets (collections of compromised computersrunn<strong>in</strong>g automated software, generally without<strong>the</strong> knowledge of <strong>the</strong>ir users) and o<strong>the</strong>r illicit tools<strong>in</strong>stead of us<strong>in</strong>g less effective tools offered by <strong>the</strong>U.S. government (which can be slower than o<strong>the</strong>rs,have restricted bandwidth and conta<strong>in</strong> o<strong>the</strong>rfeatures that make illicit tools more attractive bycomparison). “Mujahideen Secrets 2,” for example,is a jihadi-developed encryption tool designedto allow al Qaeda supporters to communicateonl<strong>in</strong>e. 139 While it is clearly impossible to elim<strong>in</strong>ate<strong>the</strong> possibility that government-sponsored
In draft<strong>in</strong>g legislation <strong>in</strong>tendedto protect <strong>the</strong> nation’s cybersystems and <strong>in</strong>frastructure,<strong>the</strong> U.S. government musttread carefully and quashperceptions that it is acceptableto use a “national cyberemergency” to trample onfreedom of expression.technologies will be used by bad actors, it is likelythat <strong>the</strong> number of bad actors do<strong>in</strong>g so will pale <strong>in</strong>comparison to <strong>the</strong> number of users simply wish<strong>in</strong>gto access neutral media.Defend<strong>in</strong>g Aga<strong>in</strong>st Attacks versusEmbolden<strong>in</strong>g AutocraciesSimple efforts to defend aga<strong>in</strong>st cyber attacks alsoaffect America’s <strong>Internet</strong> freedom agenda.The U.S. military has outl<strong>in</strong>ed a cyber securitystrategy based on active defense, which <strong>in</strong>cludesblock<strong>in</strong>g malicious software before it attempts toenter military networks. 140 Although hunt<strong>in</strong>g downdestructive content outside defense networks islikely to be rare, <strong>the</strong> head of <strong>the</strong> military’s newlyestablished U.S. Cyber Command has argued that<strong>the</strong> United States must have offensive cyber capabilitiesto shut down attack<strong>in</strong>g systems. 141 Suchmoves, which may be entirely justified, could at <strong>the</strong>same time embolden autocracies wish<strong>in</strong>g to justify<strong>the</strong>ir own offensive operations.The perception that <strong>the</strong> U.S. government couldrestrict traffic over large portions of <strong>the</strong> <strong>Internet</strong><strong>in</strong> <strong>the</strong> event of a cyber emergency could alsocomplicate its efforts to promote onl<strong>in</strong>e freedom.Congress debated a bill last year that wouldauthorize greater government control over <strong>the</strong> U.S.digital <strong>in</strong>frastructure <strong>in</strong> <strong>the</strong> event of a nationwidecyber attack. 142 Though many media reports abouta so-called <strong>Internet</strong> “kill switch” are erroneous(and a newly <strong>in</strong>troduced version explicitly prohibitsany government employee from shutt<strong>in</strong>g down <strong>the</strong><strong>Internet</strong>), <strong>the</strong> bill never<strong>the</strong>less raised concerns thatsuch authority would underm<strong>in</strong>e <strong>Internet</strong> freedom.While <strong>in</strong>terpretations of <strong>the</strong> bill vary widely, anexpert with <strong>the</strong> Electronic Frontier Foundationwarned, “The president would have essentiallyunchecked power to determ<strong>in</strong>e what services canbe connected to <strong>the</strong> <strong>Internet</strong> or even what contentcan pass over <strong>the</strong> <strong>Internet</strong> <strong>in</strong> a cyber securityemergency.” 143 The bill’s sponsors dispute this<strong>in</strong>terpretation and note that <strong>the</strong> president’s powerscould be exercised only <strong>in</strong> extreme emergenciesand pursuant to limitations.The U.S. government must establish precise,widely understood scenarios under which itcould declare an emergency and <strong>the</strong> powers itcould <strong>the</strong>n exercise. Fail<strong>in</strong>g to clearly def<strong>in</strong>e whatconstitutes a national “cyber emergency” thatwould give national leaders emergency powers torestrict <strong>Internet</strong> activity could set a precedent bywhich authoritarian regimes justify shutt<strong>in</strong>g off<strong>the</strong> <strong>Internet</strong> dur<strong>in</strong>g <strong>the</strong>ir own “cyber emergency”– such as widespread anti-government protests.Aga<strong>in</strong>, <strong>the</strong>re is a dist<strong>in</strong>ct difference between apresidential order to restrict some forms of <strong>Internet</strong>traffic <strong>in</strong> <strong>the</strong> face of a cyber attack on America’scritical <strong>in</strong>frastructure and President Mubarak’sdecision to shut down his nation’s <strong>Internet</strong> dur<strong>in</strong>g<strong>the</strong> democratic revolt <strong>in</strong> Egypt. In draft<strong>in</strong>g legislation<strong>in</strong>tended to protect <strong>the</strong> nation’s cyber systemsand <strong>in</strong>frastructure, <strong>the</strong> U.S. government musttread carefully and quash perceptions that it isacceptable to use a “national cyber emergency” totrample on freedom of expression.| 35
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>36 |VI. Recommendations – EightPr<strong>in</strong>ciples for <strong>Internet</strong> <strong>Freedom</strong>The pr<strong>in</strong>ciples and policy recommendations belowreflect an <strong>in</strong>tegrated <strong>Internet</strong> freedom strategythat balances compet<strong>in</strong>g foreign policy, economicand national security priorities, and leverages <strong>the</strong>tremendous potential of <strong>the</strong> private sector.Pr<strong>in</strong>ciple 1: Embrace a ComprehensiveApproachCurrent efforts to promote <strong>Internet</strong> freedom arefragmented across <strong>the</strong> U.S. government, and <strong>the</strong>issue barely registers among some officials whocould make a significant contribution. As a result,policymakers should <strong>in</strong>corporate <strong>Internet</strong> freedom<strong>in</strong>to <strong>the</strong>ir decision-mak<strong>in</strong>g. Promot<strong>in</strong>g<strong>Internet</strong> freedom should be l<strong>in</strong>ked to o<strong>the</strong>r goals,<strong>in</strong>clud<strong>in</strong>g America’s cyber security agenda and itseconomic diplomacy efforts. The White House’s<strong>in</strong>ternational cyberspace strategy is a step <strong>in</strong> <strong>the</strong>right direction, but a comprehensive agenda shouldcomb<strong>in</strong>e top-level policy direction with provid<strong>in</strong>gtechnology and tra<strong>in</strong><strong>in</strong>g for bloggers and activists,exercis<strong>in</strong>g diplomatic support for imprisoneddissidents and onl<strong>in</strong>e authors, tra<strong>in</strong><strong>in</strong>g for foreignservice officers and o<strong>the</strong>rs <strong>in</strong> new media, <strong>in</strong>tegrat<strong>in</strong>g<strong>Internet</strong> freedom issues <strong>in</strong>to country andregional strategies, articulat<strong>in</strong>g economic argumentsfor <strong>Internet</strong> freedom, treat<strong>in</strong>g censorshipas a trade barrier, work<strong>in</strong>g with <strong>the</strong> private sector,reform<strong>in</strong>g export controls and actively shap<strong>in</strong>g<strong>in</strong>ternational norms.To harness external expertise across fields, <strong>the</strong> U.S.government should regularly convene private sectorprofessionals; diplomats; <strong>Internet</strong> eng<strong>in</strong>eersand technical experts; cyber defense officials;export control lawyers; human rights activists;and foreign policy experts to explore new waysof promot<strong>in</strong>g <strong>Internet</strong> freedom. The aim shouldbe to share knowledge among <strong>the</strong>se professionallydist<strong>in</strong>ct groups and discern potential areas ofcooperation or policy change. This type of forumcould be modeled after <strong>the</strong> Obama adm<strong>in</strong>istration’sMarch 2011 summit on bully<strong>in</strong>g, <strong>in</strong> which<strong>the</strong> adm<strong>in</strong>istration convened civil society activists,educators, policymakers and technology firms todevelop strategies to prevent bully<strong>in</strong>g (<strong>in</strong>clud<strong>in</strong>gcyber bully<strong>in</strong>g). 144The U.S. government should use traditional diplomacyto promote America’s <strong>Internet</strong> freedomagenda, <strong>in</strong>clud<strong>in</strong>g lobby<strong>in</strong>g foreign governments toliberalize restrictions on freedom of speech, advocat<strong>in</strong>gfor American companies (when <strong>the</strong>y seeksuch diplomatic assistance) under pressure fromforeign regimes to turn over private data, press<strong>in</strong>ggovernments to release political prisoners andurg<strong>in</strong>g foreign partners to jo<strong>in</strong> <strong>the</strong> United States<strong>in</strong> pursu<strong>in</strong>g <strong>the</strong> agenda. As <strong>the</strong> U.S. governmentdoes so, it must cont<strong>in</strong>ually consider <strong>the</strong> tradeoffsbetween promot<strong>in</strong>g <strong>Internet</strong> freedom and <strong>the</strong> o<strong>the</strong>ritems on its foreign policy and economic agenda.Pr<strong>in</strong>ciple 2: Build an International Coalitionto Promote <strong>Internet</strong> <strong>Freedom</strong>The U.S. government should <strong>in</strong>ternationalizeits <strong>Internet</strong> freedom efforts. The push for onl<strong>in</strong>efreedom, which is rooted <strong>in</strong> universal values, istoo heavily identified with <strong>the</strong> United States alone.Promot<strong>in</strong>g <strong>Internet</strong> freedom must not be merelyan element of American foreign policy, but ra<strong>the</strong>rshould be an <strong>in</strong>ternational effort supported by awide range of actors• The U.S. government should convene a coregroup of democratic governments – open to anythat wish to jo<strong>in</strong> – that would toge<strong>the</strong>r advocatefor <strong>Internet</strong> freedom. This should <strong>in</strong>clude seek<strong>in</strong>gcommon statements and policy advocacy<strong>in</strong> <strong>in</strong>ternational fora where rules and norms aremost likely to be set. It should also convene o<strong>the</strong>rstakeholders, <strong>in</strong>clud<strong>in</strong>g <strong>in</strong>ternational organizations,NGOs and <strong>the</strong> private sector, for <strong>the</strong> samepurpose.• The Secretary of State should give her nextmajor address on <strong>Internet</strong> freedom <strong>in</strong> a foreign
country, possibly <strong>in</strong> Europe alongside key EUcommissioners.• The U.S. government should help <strong>in</strong>ternationalize<strong>the</strong> GNI by urg<strong>in</strong>g European and o<strong>the</strong>rdemocratic governments to encourage foreigncompanies to jo<strong>in</strong>.The U.S. government should work to expand <strong>the</strong>sources of technology fund<strong>in</strong>g over <strong>the</strong> mediumto long term. The U.S. government should encourageo<strong>the</strong>r actors to fund <strong>Internet</strong> freedom-relatedtechnologies, so that it does not rema<strong>in</strong> <strong>the</strong> majorfunder of such technologies <strong>in</strong>def<strong>in</strong>itely.• Officials should work with like-m<strong>in</strong>ded governmentsand NGOs to expla<strong>in</strong> America’s <strong>Internet</strong>freedom-related technology programs, sharelessons learned thus far, and encourage <strong>the</strong>mto develop <strong>the</strong>ir own programs. They shouldalso urge <strong>the</strong> private sector to monetize circumventionand anonymity technologies (e.g. bycircumvent<strong>in</strong>g restrictions so users can accesswebsites with ads).Pr<strong>in</strong>ciple 3: Move Beyond CircumventionTechnologiesThe U.S. government should fund a range oftechnologies beyond those that circumventonl<strong>in</strong>e censorship. While break<strong>in</strong>g down Ch<strong>in</strong>a’sGreat Firewall has attracted <strong>the</strong> vast majorityof public attention and support on Capitol Hill,circumvention tools should comprise just one(albeit critical) element of a much larger agenda.The State Department has requested proposalsfor multiple programs that toge<strong>the</strong>r comprise aquite well-rounded approach to technology, all ofwhich should receive fund<strong>in</strong>g. State also plans toestablish an emergency fund to help civil societyorganizations keep <strong>the</strong>ir onl<strong>in</strong>e operations up andrunn<strong>in</strong>g if <strong>the</strong>y are targeted by severe hack<strong>in</strong>g orcyber attacks. 145• In addition to fund<strong>in</strong>g exist<strong>in</strong>g tools, <strong>the</strong> U.S.government should fund technologies that:»» Help dissident and human rights websites protect<strong>the</strong>mselves aga<strong>in</strong>st DDoS attacks.»» Help groups create mirror sites and reconstitute<strong>the</strong>ir websites and archives after atakedown.»» Facilitate encrypted communications ando<strong>the</strong>r forms of digital security.»» Ensure mobile access. Mobile platforms are<strong>in</strong>creas<strong>in</strong>gly <strong>the</strong> locus of onl<strong>in</strong>e activity, and<strong>the</strong> State Department should ensure that a disproportionateamount of fund<strong>in</strong>g focuses onsecur<strong>in</strong>g open access to <strong>the</strong> <strong>Internet</strong> throughmobile devices.• In order to maximize users’ safety, <strong>the</strong> U.S. governmentshould require any onl<strong>in</strong>e tool receiv<strong>in</strong>gU.S. fund<strong>in</strong>g to go through an <strong>in</strong>dependentsecurity audit before it is deployed.The U.S. government should adopt a f<strong>in</strong>ancialaward, ak<strong>in</strong> to <strong>the</strong> “X Prize” that <strong>in</strong>vitestechnological competition, and o<strong>the</strong>r creativemethods to foster technological <strong>in</strong>novation. Thegovernment should offer a f<strong>in</strong>ancial award toprivate sector organizations that can develop <strong>the</strong>lowest-cost, most user-friendly and most resilientcircumvention or anonymity technology (e.g., an<strong>Internet</strong> <strong>Freedom</strong> Innovation Award for develop<strong>in</strong>gbest-<strong>in</strong>-class technologies).Pr<strong>in</strong>ciple 4: Prioritize Tra<strong>in</strong><strong>in</strong>gThe State Department, along with USAID, shouldcont<strong>in</strong>ue to foster <strong>Internet</strong> freedom through targetedtra<strong>in</strong><strong>in</strong>g programs. Current or forthcom<strong>in</strong>gtra<strong>in</strong><strong>in</strong>g programs <strong>in</strong>clude basic tra<strong>in</strong><strong>in</strong>g <strong>in</strong> digitaltools for activists and civil society organizations,<strong>in</strong>struction on us<strong>in</strong>g virtual open <strong>Internet</strong> centersand tra<strong>in</strong><strong>in</strong>g <strong>in</strong> digital security. 146• The U.S. government should help activistsunderstand <strong>the</strong> risks associated with us<strong>in</strong>g newcommunications technologies and develop plansto secure <strong>the</strong>ir networks; establish cont<strong>in</strong>gencyplans for emergencies; and establish processes for| 37
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>38 |putt<strong>in</strong>g websites and digital archives back onl<strong>in</strong>eafter an attack. It should also tra<strong>in</strong> dissidents <strong>in</strong>personal security aga<strong>in</strong>st both cyber and noncybermonitor<strong>in</strong>g, such as surveillance cameras<strong>in</strong> <strong>Internet</strong> cafes.Pr<strong>in</strong>ciple 5: Lead <strong>the</strong> Effort to BuildInternational NormsThe U.S. government should press <strong>in</strong> all relevantfora for a liberal concept of <strong>Internet</strong> freedom,and counter attempts by authoritarian states toadopt norms that restrict freedom of <strong>in</strong>formationand expression onl<strong>in</strong>e. American officialshave wisely tied basic <strong>Internet</strong> freedom pr<strong>in</strong>ciplesto exist<strong>in</strong>g <strong>in</strong>ternational agreements, but <strong>the</strong>yshould also seek to articulate <strong>the</strong>se pr<strong>in</strong>ciples <strong>in</strong>new normative arrangements dur<strong>in</strong>g meet<strong>in</strong>gs of<strong>the</strong> U.N., <strong>the</strong> ITU, <strong>the</strong> G8 and G20 meet<strong>in</strong>gs, ando<strong>the</strong>r <strong>in</strong>ternational fora.• U.S. officials should publicly and clearly dist<strong>in</strong>guishbetween practices <strong>in</strong> democracies, whichgive law enforcement access to o<strong>the</strong>rwise privatedata pursuant to due process, and those <strong>in</strong> countrieswhose governments seize such <strong>in</strong>formationwithout due process.• The U.S. government should clearly def<strong>in</strong>ewhat constitutes a national security threat <strong>in</strong>cyberspace. It should emphasize that it willonly restrict <strong>Internet</strong> traffic dur<strong>in</strong>g a national“cyber emergency” <strong>in</strong> accordance with clear andtransparent pr<strong>in</strong>ciples (e.g., not to target politicalspeech).• The United States should work with o<strong>the</strong>r<strong>in</strong>novative, economically powerful marketdemocracies to build common pr<strong>in</strong>ciples fordomestic <strong>Internet</strong> use <strong>in</strong>clud<strong>in</strong>g general pr<strong>in</strong>ciplesfor <strong>the</strong> k<strong>in</strong>ds of data governments will blockand censor and how <strong>the</strong>y will communicatethose decisions.• The United States should pursue an <strong>in</strong>ternationaltransparency <strong>in</strong>itiative to encourage governmentsto publicly state <strong>the</strong> categories of onl<strong>in</strong>e<strong>in</strong>formation to which <strong>the</strong>y restrict access, <strong>the</strong> legalgrounds for <strong>the</strong>se restrictions and how those lawscan be changed (if this is not self-evident).Pr<strong>in</strong>ciple 6: Create Economic Incentivesto Support <strong>Internet</strong> <strong>Freedom</strong>U.S. officials should cont<strong>in</strong>ue to articulate<strong>the</strong> economic case for <strong>Internet</strong> freedom. TheState Department’s description of a “dictator’sdilemma” should be supported by solid, quantitativeevidence of <strong>the</strong> economic benefits ofonl<strong>in</strong>e freedom and costs of <strong>Internet</strong> repression.U.S. officials should make <strong>the</strong> corporate case aswell, as <strong>the</strong> Secretary of State has done <strong>in</strong> <strong>the</strong>past. <strong>Internet</strong> freedom can reduce corruption by<strong>in</strong>creas<strong>in</strong>g transparency, reduc<strong>in</strong>g <strong>the</strong> risk thatThe State Department’sdescription of a “dictator’sdilemma” should be supportedby solid, quantitative evidenceof <strong>the</strong> economic benefits ofonl<strong>in</strong>e freedom and costs of<strong>Internet</strong> repression.companies will face politically motivated requeststhat generate adverse <strong>in</strong>ternational publicity andlimit<strong>in</strong>g <strong>the</strong> chances that a firm’s websites will beshuttered or its staff threatened.The U.S. government should push for <strong>Internet</strong>censorship to be recognized as a trade barrier.• The United States should press for a b<strong>in</strong>d<strong>in</strong>gclause <strong>in</strong> any Trans-Pacific Partnership agreement– currently under consideration – that<strong>in</strong>corporates basic pr<strong>in</strong>ciples about <strong>the</strong> free flow
of digital <strong>in</strong>formation, and seek to <strong>in</strong>clude suchprovisions <strong>in</strong> o<strong>the</strong>r trade agreements.• The United States should exam<strong>in</strong>e <strong>the</strong> legal casefor treat<strong>in</strong>g extreme cases of <strong>Internet</strong> repression(e.g. Egypt’s shutdown <strong>in</strong> early 2011) as a violationof World Trade Organization rules, and<strong>in</strong>clude <strong>in</strong>formation <strong>in</strong> U.S. Trade Representative(USTR) and Commerce Department reportsabout <strong>the</strong> economic harm produced by censorshipand o<strong>the</strong>r forms of <strong>Internet</strong> repression.Pr<strong>in</strong>ciple 7: Streng<strong>the</strong>n <strong>the</strong> Private Sector’sRole <strong>in</strong> Support<strong>in</strong>g <strong>Internet</strong> <strong>Freedom</strong>U.S. government officials should cont<strong>in</strong>ue tourge companies to jo<strong>in</strong> <strong>the</strong> GNI, while alsoencourag<strong>in</strong>g companies to develop broad unilateralcodes of conduct consistent with <strong>the</strong> GNI’sunderly<strong>in</strong>g pr<strong>in</strong>ciples.Congress should adopt a nuanced legal frameworkfor <strong>the</strong> proper role of American corporations that:• Prohibits activities such as giv<strong>in</strong>g autocraticgovernments <strong>the</strong> private data of dissidents, when<strong>the</strong> request is clearly <strong>in</strong>tended to quash legitimatefreedom of expression.• Requires American companies to periodicallydisclose to <strong>the</strong> U.S. government:»» <strong>Foreign</strong> governments’ requests for <strong>in</strong>formationand services that do not conform to <strong>in</strong>ternationally-recognizedstandards (<strong>in</strong>clud<strong>in</strong>g <strong>in</strong>formationabout users, IP block<strong>in</strong>g, keyword censorship andonl<strong>in</strong>e surveillance), and whe<strong>the</strong>r <strong>the</strong> companiescomplied with <strong>the</strong>se requests.»» Sales of technology and services to governmentagencies or state-controlled companies that arereasonably expected to aid significant <strong>Internet</strong>repression.Congress should cont<strong>in</strong>ue highlight<strong>in</strong>g specificbus<strong>in</strong>ess practices that both promote and restrict<strong>Internet</strong> freedom through hear<strong>in</strong>gs, resolutions,<strong>the</strong> bully pulpit and o<strong>the</strong>r means. In addition toRecommendations for TechnologyCompaniesTechnology firms should take several measures topromote onl<strong>in</strong>e freedom, many of which can directlyor <strong>in</strong>directly benefit <strong>the</strong>ir bottom l<strong>in</strong>es. They should:• Provide basic technical assistance with built-<strong>in</strong>security functions, such as secure passwordprotection and assess ways <strong>in</strong> which foreigngovernments can use <strong>the</strong>ir tools or services for<strong>Internet</strong> repression and explore ways to mitigatethose uses.• Better <strong>in</strong>form users and <strong>the</strong> public about who mayaccess data <strong>the</strong>y control and under what conditions,so that users can make <strong>in</strong>formed decisionsabout whe<strong>the</strong>r us<strong>in</strong>g particular services <strong>in</strong> specificcontexts will put <strong>the</strong>m <strong>in</strong> danger. 147• Move toward greater transparency when censor<strong>in</strong>gcontent or shar<strong>in</strong>g private <strong>in</strong>formation withgovernments. Google’s transparency reportpublicizes <strong>the</strong> number of government <strong>in</strong>quiriesit receives for <strong>in</strong>formation about users andrequests for <strong>the</strong> company to take down or censorcontent. This provides one useful model for<strong>in</strong>creas<strong>in</strong>g transparency, and technology companiesshould seek to establish <strong>in</strong>dustry-widestandards on public disclosure.• Fund technology personnel at human rights anddemocracy organizations so that <strong>the</strong>se groups candevelop a deeper understand<strong>in</strong>g of <strong>the</strong> complexissues surround<strong>in</strong>g new communications technologyand political change abroad, and so thatcompanies can <strong>in</strong>crease <strong>the</strong>ir understand<strong>in</strong>g ofhuman rights advocacy and <strong>the</strong> ways <strong>in</strong> whichtechnology products and features are viewed.• Advocate for <strong>Internet</strong> freedom abroad.American companies have an <strong>in</strong>centive to avoidbe<strong>in</strong>g caught between <strong>the</strong> requirements oflocal law <strong>in</strong> an autocratic environment and <strong>the</strong>bad publicity that might result from comply<strong>in</strong>gwith <strong>the</strong>m. They can work to preempt suchdilemmas by press<strong>in</strong>g foreign governments formore liberal <strong>Internet</strong> environments – or at <strong>the</strong>very least resist efforts to aid repression.| 39
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>nam<strong>in</strong>g and sham<strong>in</strong>g, Congress and <strong>the</strong> executivebranch should publicly praise companies that areattempt<strong>in</strong>g to uphold universal values while do<strong>in</strong>gbus<strong>in</strong>ess <strong>in</strong> autocratic environments.Pr<strong>in</strong>ciple 8: Reform Export ControlsThe U.S. government should launch a full reviewof its export controls on new communicationstechnology, which should aim to:• Permit <strong>the</strong> export of o<strong>the</strong>rwise widely availableopen source code that would be available to foreignusers at no cost.• Ensure that circumvention and o<strong>the</strong>r technologiesthat are identical or very similar to those supportedby <strong>the</strong> U.S. government (and thus exempted fromexport controls) are also exempted.• Determ<strong>in</strong>e ways (which <strong>in</strong> some cases willrequire new legislation) to relax restrictions onexport<strong>in</strong>g relevant technologies to countries likeSyria, which was not <strong>in</strong>cluded <strong>in</strong> Treasury’s 2010export control revisions. 148• Ensure that any export control reforms accountsfor <strong>the</strong> need to ma<strong>in</strong>ta<strong>in</strong> safeguards on Americantechnology for national security reasons.The U.S. government should educate technologycompanies on <strong>the</strong> exact requirements ofexport controls – <strong>in</strong>clud<strong>in</strong>g any changes – so thatcompanies do not over-comply and deny legaltechnologies to activists abroad.VII. ConclusionThe U.S. government must develop a truly comprehensive<strong>Internet</strong> freedom strategy. Over <strong>the</strong> pastseveral years, it has taken important, positive steps<strong>in</strong> a number of areas, from provid<strong>in</strong>g technologiesto shap<strong>in</strong>g norms to engag<strong>in</strong>g <strong>the</strong> private sector. Itmust now build on <strong>the</strong>se efforts to <strong>in</strong>tegrate o<strong>the</strong>relements, <strong>in</strong>clud<strong>in</strong>g trade policy, export controlreform and o<strong>the</strong>rs. Underly<strong>in</strong>g all <strong>the</strong>se efforts isa bet – essentially <strong>the</strong> same bet that <strong>the</strong> UnitedStates placed dur<strong>in</strong>g <strong>the</strong> Cold War – that support<strong>in</strong>gaccess to <strong>in</strong>formation and encourag<strong>in</strong>g <strong>the</strong> freeexchange of ideas is good for America. As we havediscussed <strong>in</strong> this report, we believe this bet is wellworth mak<strong>in</strong>g.A free <strong>Internet</strong>, however, is not a silver bullet forsocial change. Support<strong>in</strong>g <strong>Internet</strong> freedom is complicatedand poses tradeoffs with o<strong>the</strong>r items on<strong>the</strong> American diplomatic, security and economicagenda. It should be seen as just one, potentiallyquite important, element <strong>in</strong> a broader approach topromot<strong>in</strong>g democratic ideals <strong>in</strong> repressive societies.The net effect of this effort is uncerta<strong>in</strong>, and itwill likely rema<strong>in</strong> so for years.But we should not underestimate <strong>the</strong> potentialpower of <strong>the</strong> <strong>Internet</strong>. We live <strong>in</strong> a time whenan application like Facebook, designed <strong>in</strong> 2004for American university students to share <strong>in</strong>formationhas, <strong>in</strong> 2011, helped topple a dictator <strong>in</strong>Egypt; a time when <strong>the</strong> best satellite televisioncoverage of demonstrations and conflict can comefrom onl<strong>in</strong>e video post<strong>in</strong>gs; and a time when dissidentsrisk imprisonment or worse for blogg<strong>in</strong>g<strong>the</strong>ir beliefs.40 |The U.S. government faces a constant challenge <strong>in</strong>keep<strong>in</strong>g up with new technology and <strong>the</strong> chang<strong>in</strong>gways that users employ it. Corporations arecont<strong>in</strong>ually vexed by <strong>the</strong> many vary<strong>in</strong>g demandsput upon <strong>the</strong>m by governments around <strong>the</strong> world.Individuals <strong>in</strong> autocratic societies face dilemmas
We live <strong>in</strong> a time when anapplication like Facebook,designed <strong>in</strong> 2004 forAmerican university studentsto share <strong>in</strong>formation has, <strong>in</strong>2011, helped topple a dictator<strong>in</strong> Egypt.<strong>in</strong> determ<strong>in</strong><strong>in</strong>g how to proceed onl<strong>in</strong>e. Though<strong>the</strong> debate is complicated, <strong>the</strong> longstand<strong>in</strong>gAmerican commitment to basic human rights andfreedoms should rema<strong>in</strong> clear. And on that basis,<strong>the</strong> United States has a responsibility to promote<strong>Internet</strong> freedom, which is key to ensur<strong>in</strong>g agreater degree of human liberty <strong>in</strong> an ever-morecontestedspace.| 41
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>endnotes42 |1. “Over 5 Billion Mobile Phone Connections Worldwide,” BBC News (9 July2010), http://www.bbc.co.uk/news/10569081.2. The authors thank Rebecca MacK<strong>in</strong>non for <strong>the</strong> <strong>in</strong>sight that <strong>the</strong> cyberdoma<strong>in</strong> constitutes an extension of civil society.3. President Barack Obama stated that, “There are certa<strong>in</strong> core valuesthat we believe <strong>in</strong> as Americans that we believe are universal: freedom ofspeech, freedom of expression, people be<strong>in</strong>g able to use social network<strong>in</strong>gor any o<strong>the</strong>r mechanisms to communicate with each o<strong>the</strong>r and express <strong>the</strong>irconcerns.” David Jackson, “Obama: ‘Violence is Not <strong>the</strong> Answer’ <strong>in</strong> Egypt,” USAToday (28 January 2011), http://content.usatoday.com/communities/<strong>the</strong>oval/post/2011/01/obama-violence-is-not-<strong>the</strong>-answer-<strong>in</strong>-egypt/1?csp=34.4. For <strong>the</strong> purposes of this study, we use <strong>the</strong> term “<strong>Internet</strong>” and “newcommunications technologies” <strong>in</strong>terchangeably, def<strong>in</strong><strong>in</strong>g <strong>the</strong>m to <strong>in</strong>cludea broad collection of new digital communication technologies that areconnected <strong>in</strong> some form to <strong>the</strong> <strong>Internet</strong>, <strong>in</strong>clud<strong>in</strong>g SMS text, Skype and o<strong>the</strong>rvoice-over-<strong>the</strong>-<strong>Internet</strong> protocols (VOIP), as well as web-based platforms(e.g., Facebook and Twitter).5. The authors paid particular attention to exam<strong>in</strong><strong>in</strong>g <strong>the</strong> potential tensionsbetween <strong>Internet</strong> freedom and cyber security; <strong>the</strong>se tensions are explored<strong>in</strong> greater depth <strong>in</strong> “America’s Cyber Future: Security and Prosperity <strong>in</strong> <strong>the</strong>Information <strong>Age</strong>,” Center for a New American Security (June 2011).6. Evgeny Morozov, The Net Delusion (New York: PublicAffairs Books, 2011):230.7. Universal Declaration of Human Rights, Article 19. The InternationalCovenant on Civil and Political Rights also articulates basic freedoms ofexpression applicable to <strong>Internet</strong>-based activity, as described below.8. “Statement by <strong>the</strong> Press Secretary on Violence <strong>in</strong> Syria” (24 March 2011),http://www.whitehouse.gov/<strong>the</strong>-press-office/2011/03/24/statement-presssecretary-violence-syria.9. The White House, National Security Strategy of <strong>the</strong> United States, Section 3(May 2010): 39, http://www.whitehouse.gov/sites/default/files/rss_viewer/national_security_strategy.pdf.10. U.S. Department of State, State Summary of Global <strong>Internet</strong> <strong>Freedom</strong> TaskForce: Group Seeks to Maximize <strong>Freedom</strong> of Expression, Free Flow of Informationand Ideas (20 December 2006), http://www.america.gov/st/democracyhrenglish/2006/December/20061220173640xjsnommis0.7082331.html.11. The White House, National Security Strategy of <strong>the</strong> United States, Section7.C.1 (March 2006),http://georgewbush-whitehouse.archives.gov/nsc/nss/2006/sectionVII.html.12. “Remarks by <strong>the</strong> President to <strong>the</strong> United Nations General Assembly” (23September 2009), http://www.whitehouse.gov/<strong>the</strong>_press_office/Remarksby-<strong>the</strong>-President-to-<strong>the</strong>-United-Nations-General-Assembly/.13. Hillary Rodham Cl<strong>in</strong>ton, “<strong>Internet</strong> Rights and Wrongs: Choices &Challenges <strong>in</strong> a Networked World,” The George Wash<strong>in</strong>gton University,Wash<strong>in</strong>gton (15 February 2011), http://www.state.gov/secretary/rm/2011/02/156619.htm.14. “Yahoo Chief Apologizes to Ch<strong>in</strong>ese Dissidents’ Relatives,” The New YorkTimes (7 November 2007), http://www.nytimes.com/2007/11/07/bus<strong>in</strong>ess/worldbus<strong>in</strong>ess/07iht-yahoo.1.8226586.html.15. The bill has subsequently been <strong>in</strong>troduced <strong>in</strong> different versions, but hasnot been passed as of this writ<strong>in</strong>g. Global <strong>Internet</strong> <strong>Freedom</strong> Act, Govtrack.us (10May 2005), http://www.govtrack.us/congress/billtext.xpd?bill=h109-2216.16. Glenn Kessler, “Cisco File Raises Censorship Concerns,” The Wash<strong>in</strong>gtonPost (20 May 2008), http://www.wash<strong>in</strong>gtonpost.com/wp-dyn/content/article/2008/05/19/AR2008051902661.html.17. In full disclosure, one of <strong>the</strong> authors of this report helped draft this actwhile serv<strong>in</strong>g <strong>in</strong> government.18. U.S. Department of State, State Summary of Global <strong>Internet</strong> <strong>Freedom</strong>Task Force (20 December 2006), http://www.america.gov/st/democracyhrenglish/2006/December/20061220173640xjsnommis0.7082331.html.19. Hillary Rodham Cl<strong>in</strong>ton, “Remarks on <strong>Internet</strong> <strong>Freedom</strong>,” <strong>the</strong>Newseum, Wash<strong>in</strong>gton (21 January 2010), http://www.state.gov/secretary/rm/2010/01/135519.htm.20. Hillary Rodham Cl<strong>in</strong>ton, “<strong>Internet</strong> Rights and Wrongs: Choices &Challenges <strong>in</strong> a Networked World,” The George Wash<strong>in</strong>gton University,Wash<strong>in</strong>gton (15 February 2011), http://www.state.gov/secretary/rm/2011/02/156619.htm.21. Ibid.22 . Ibid.23. Sami ben Gharbia, “The <strong>Internet</strong> <strong>Freedom</strong> Fallacy and <strong>the</strong> Arab <strong>Digital</strong>Activism,” Samibengharbia.com (17 September 2010), http://samibengharbia.com/2010/09/17/<strong>the</strong>-<strong>in</strong>ternet-freedom-fallacy-and-<strong>the</strong>-arab-digitalactivism/.24. Lachlan Carmichael, “U.S. Tra<strong>in</strong>s Activists to Evade Security Forces,” <strong>Age</strong>nceFrance Press (8 April 2011), http://www.google.com/hostednews/afp/article/ALeqM5h-zfvaYJftSfafM8whfpxycifTaQ?docId=CNG.2bbf1732398d8832e67b0555c508f609.a01.25. We draw from <strong>the</strong> work of Larry Diamond, a lead<strong>in</strong>g democracy scholar. Inhis book, The Spirit of Democracy, he describes at length <strong>the</strong> “thick conception”of democracy and lists several attributes that dist<strong>in</strong>guish democracies fromo<strong>the</strong>r political systems. Larry Diamond, The Spirit of Democracy (New York:Times Books, 2008): 22.26. Bernard Kouchner, “The Battle for <strong>the</strong> <strong>Internet</strong>,” The New York Times (13May 2010), http://www.nytimes.com/2010/05/14/op<strong>in</strong>ion/14iht-edkouchner.html?_r=1.
27. Nicholas D. Kristof, “Tear Down This Cyberwall!” The New York Times(17 June 2009), http://www.nytimes.com/2009/06/18/op<strong>in</strong>ion/18kristof.html?_r=1.28. Under Secretary of State for Democracy and Global Affairs PaulaDobriansky, “New Media vs. New Censorship: The Assault,” remarks toBroadcast<strong>in</strong>g Board of Governors, Wash<strong>in</strong>gton (10 September 2008).29. Mark Pfeifle, “A Nobel Peace Prize for Twitter?” The Christian ScienceMonitor (6 July 2009), http://www.csmonitor.com/Commentary/Op<strong>in</strong>ion/2009/0706/p09s02-coop.html.30. Alexei Oreskovic, “Egyptian Activist Creates Image Issue for Google,”Reuters (12 February 2011), http://www.reuters.com/article/2011/02/12/us-egypt-google-idUSTRE71B0KQ20110212.31. Evgeny Morozov, The Net Delusion (New York: PublicAffairs Books, 2011):xiii.32 . Malcom Gladwell, “Why <strong>the</strong> Revolution Won’t be Tweeted,”The New Yorker (4 October 2010), http://www.newyorker.com/report<strong>in</strong>g/2010/10/04/101004fa_fact_gladwell?currentPage=1.33. Jeffrey Gedm<strong>in</strong>, “Democracy isn’t just a tweet away,” USA Today (22 April2010).34. Golnaz Esfandiari, “Misread<strong>in</strong>g Tehran: The Twitter Devolution,” <strong>Foreign</strong><strong>Policy</strong> (7 June 2010), http://www.foreignpolicy.com/articles/2010/06/07/<strong>the</strong>_twitter_revolution_that_wasnt.35 . Ian Bremmer, “Democracy <strong>in</strong> Cyberspace,” <strong>Foreign</strong> Affairs (November/December 2010), http://www.foreignaffairs.com/articles/66803/ianbremmer/democracy-<strong>in</strong>-cyberspace.36. Sean Aday, Henry Farrell, Marc Lynch, John Sides, John Kelly and EthanZuckerman, “Blogs and Bullets: New Media <strong>in</strong> Contentious Politics,” UnitedStates Institute of Peace (August 2010): 9. Much of <strong>the</strong> discussion of <strong>the</strong>ories ofchange <strong>in</strong> this section draws upon this important work.37. Ibid.: 9.38. Evgeny Morozov, “From Slacktivism to Activism,” <strong>Foreign</strong> <strong>Policy</strong> NetEffect blog (5 September 2009), http://neteffect.foreignpolicy.com/posts/2009/09/05/from_slacktivism_to_activism.39. Larry Diamond, “Liberation Technology,” Journal of Democracy (July 2010):70.40. Ibid.41. Sean Aday, Henry Farrell, Marc Lynch, John Sides, John Kelly and EthanZuckerman, “Blogs and Bullets: New Media <strong>in</strong> Contentious Politics,” UnitedStates Institute of Peace (August 2010): 10.42. Steve Coll, “The <strong>Internet</strong>: For Better or for Worse,” The New York Review ofBooks (7 April 2011).43. Lauren Kirchner, “‘Information Wars’ on Al Jazeera English,” ColumbiaJournalism Review (14 February 2011).44. Sean Aday, Henry Farrell, Marc Lynch, John Sides, John Kelly and EthanZuckerman, “Blogs and Bullets: New Media <strong>in</strong> Contentious Politics,” UnitedStates Institute of Peace (August 2010): 10-11. The authors po<strong>in</strong>t out thatsocial media <strong>in</strong> particular may reduce <strong>the</strong> transaction costs for organiz<strong>in</strong>gcollective action, for example by mak<strong>in</strong>g communication easier across physicaland social distance, or by underm<strong>in</strong><strong>in</strong>g top-down movements <strong>in</strong> favor offlatter social movements.45 . Ibid.: 18.46. This website has evidently garnered little <strong>in</strong>terest. Evgeny Morozov,“Th<strong>in</strong>k Aga<strong>in</strong>: The <strong>Internet</strong>,” <strong>Foreign</strong> <strong>Policy</strong> (May/June 2010), http://www.foreignpolicy.com/articles/2010/04/26/th<strong>in</strong>k_aga<strong>in</strong>_<strong>the</strong>_<strong>in</strong>ternet.47. “‘Haystack’ Gives Iranian Opposition Hope for Evad<strong>in</strong>g <strong>Internet</strong>Censorship,” The Christian Science Monitor (16 April 2010).48. Jennifer Preston, “Syria Restores Access to Facebook and YouTube,” TheNew York Times (9 February 2011).49. Spencer Ackerman, “Trolls Pounce on Facebook’s Tahrir Square,” Wired (4February 2011), http://www.wired.com/dangerroom/2011/02/trolls-pounceon-facebooks-tahrir-square/.50. Tarek Amr, “The Middle East, <strong>the</strong> Revolution and <strong>the</strong> <strong>Internet</strong>,” Remarksat AccessNow web symposium (3 February 2011), https://www.accessnow.org/policy-activism/press-blog/The-Middle-East-The-Revolution-And-The-<strong>Internet</strong>.51. Daniel Cal<strong>in</strong>gaert, “Authoritarianism vs. <strong>the</strong> <strong>Internet</strong>,” <strong>Policy</strong> Review (1April 2010): 6.52 . Brianna Lee, “Ch<strong>in</strong>ese Government Issues Preemptive Crackdown of‘Jasm<strong>in</strong>e Revolution’ Protests,” PBS.org (3 March 2011), http://www.pbs.org/wnet/need-to-know/<strong>the</strong>-daily-need/ch<strong>in</strong>ese-government-issuespreemptive-crackdown-of-jasm<strong>in</strong>e-revolution-protests/7697/.53. Qu<strong>in</strong>cy Yu, “Aborted Ch<strong>in</strong>ese ‘Jasm<strong>in</strong>e Revolution’ a Trap Say Analysts,” TheEpoch Times (22 February 2011), http://www.<strong>the</strong>epochtimes.com/n2/ch<strong>in</strong>a/aborted-ch<strong>in</strong>ese-jasm<strong>in</strong>e-revolution-a-trap-say-analysts-51732.html.54. 2010 Reporters Without Borders report cited <strong>in</strong> “New Media: A Force forGood or Evil?” The Layal<strong>in</strong>a Review (12-25 March 2010), http://www.layal<strong>in</strong>a.tv/publications/review/PR_VI.6/article2.html.55 . Rebecca MacK<strong>in</strong>non, “Ch<strong>in</strong>a, <strong>the</strong> <strong>Internet</strong>, and Google,” testimony before<strong>the</strong> Congressional-Executive Commission on Ch<strong>in</strong>a (1 March 2010): 7.56. Scott Peterson, “On Libya-Tunisia Border, Refugees Plead for Help to GoHome,” The Christian Science Monitor (3 March 2011).57. Ibid.: 12.58. The Organisation for Economic Co-operation and Development publisheda 2007 study on <strong>the</strong> economic impact of broadband <strong>Internet</strong> access based on| 43
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong><strong>the</strong> work done by its Work<strong>in</strong>g Party on <strong>the</strong> Information Economy. The studynotes that <strong>Internet</strong> communication technologies (ICTs) enable measurableeconomic growth: “Broadband is also <strong>in</strong>creas<strong>in</strong>gly important as an enabl<strong>in</strong>gtechnology for structural changes <strong>in</strong> <strong>the</strong> economy, most notably via its impacton productivity growth, but also by rais<strong>in</strong>g product market competition<strong>in</strong> many sectors, especially <strong>in</strong> services. ICTs and broadband are facilitat<strong>in</strong>g<strong>the</strong> globalisation of many services, with broadband mak<strong>in</strong>g it feasiblefor producers and consumers of services to be <strong>in</strong> different geographicallocations.” Organisation for Economic Co-operation and Development,“Broadband and <strong>the</strong> Economy” (5 May 2007): 5, http://www.oecd.org/dataoecd/62/7/40781696.pdf.59. Hillary Rodham Cl<strong>in</strong>ton, “<strong>Internet</strong> Rights and Wrongs: Choices &Challenges <strong>in</strong> a Networked World” (15 February 2011), http://www.state.gov/secretary/rm/2011/02/156619.htm.60. The Organisation for Economic Co-operation and Development , “TheEconomic Impact of Shutt<strong>in</strong>g Down <strong>Internet</strong> and Mobile Phone Services <strong>in</strong>Egypt” (4 February 2011), http://www.oecd.org/document/19/0,3746,en_2649_34223_47056659_1_1_1_1,00.html.61 . Eric Schmidt and Jared Cohen, “The <strong>Digital</strong> Disruption: Connectivity and<strong>the</strong> Diffusion of Power,” <strong>Foreign</strong> Affairs (November/December 2010).62. Doyle McManus, “Did Tweet<strong>in</strong>g Topple Tunisia?” Los Angeles Times (23January 2011).63. As is true when evaluat<strong>in</strong>g <strong>the</strong> effect of new technologies along o<strong>the</strong>rdimensions of political change, here too it is important to temper exuberancewith caution. Historian Simon Sebag Montefiore, for <strong>in</strong>stance, notes that whileFacebook “certa<strong>in</strong>ly accelerates <strong>the</strong> mobilization of crowds … technology’seffect is exaggerated: <strong>in</strong> 1848, <strong>the</strong> revolution that most resemblestoday’s, upris<strong>in</strong>gs spread from Sicily to Paris, Berl<strong>in</strong>, Vienna and Budapest <strong>in</strong>mere weeks without telephones, let alone Twitter. They spread through <strong>the</strong>exuberance of momentum and <strong>the</strong> rigid isolation of repressive rulers.” SimonSebag Montefiore, “Every Revolution is Revolutionary <strong>in</strong> Its Own Way,” TheNew York Times (27 March 2011).64 . Stephen Williams, <strong>the</strong> BBC’s executive editor for <strong>the</strong> Asia Pacific Region,emphasized <strong>the</strong> reciprocal <strong>in</strong>formation flows between onl<strong>in</strong>e media andtelevision dur<strong>in</strong>g <strong>the</strong> 2009 Iranian protests. At <strong>the</strong> height of <strong>the</strong> protests,he notes, <strong>the</strong> BBC’s Persian television offices <strong>in</strong> London received betweensix and eight <strong>Internet</strong> photos, emails and text messages every m<strong>in</strong>ute. “The<strong>in</strong>fluence of <strong>Internet</strong> social media was huge <strong>in</strong> dissem<strong>in</strong>at<strong>in</strong>g pictures andmessages round <strong>the</strong> world,” Williams says, and it “has undoubtedly helped <strong>the</strong>opposition contact o<strong>the</strong>r like-m<strong>in</strong>ded voices <strong>in</strong>side Iran. But <strong>the</strong> most impactmak<strong>in</strong>g pictures and reports could only be seen by a wider public <strong>in</strong> Iranthrough Persian-speak<strong>in</strong>g TV, because <strong>Internet</strong> activity is limited.” StephenWilliams, “The Power of TV News: An Insider’s Perspective on <strong>the</strong> Launch ofBBC Persian TV <strong>in</strong> <strong>the</strong> Year of <strong>the</strong> Iranian Upris<strong>in</strong>g,” Joan Shorenste<strong>in</strong> Centeron <strong>the</strong> Press, Politics and Public <strong>Policy</strong>, Harvard University, Discussion PaperSeries #D-54 (February 2010).65. See Lauren Kirchner, “‘Information Wars’ on Al Jazeera English,” ColumbiaJournalism Review (14 February 2011).66. Jillian York, “More Than Half a Billion <strong>Internet</strong> Users are Be<strong>in</strong>g FilteredWorldwide,” Open Net Initiative (19 January 2010), http://opennet.net/blog/2010/01/more-half-a-billion-<strong>in</strong>ternet-users-are-be<strong>in</strong>g-filteredworldwide.67. Sean Aday, Henry Farrell, Marc Lynch, John Sides, John Kelly and EthanZuckerman, “Blogs and Bullets: New Media <strong>in</strong> Contentious Politics,” UnitedStates Institute of Peace (August 2010): 13.68. Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris and John Palfrey,“2010 Circumvention Tool Usage Report,” Berkman Center for <strong>Internet</strong> andSociety, Harvard University (October 2010): 6, http://cyber.law.harvard.edu/sites/cyber.law.harvard.edu/files/2010_Circumvention_Tool_Usage_Report.pdf.69. Clay Shirky, “The Political Power of Social Media: Technology, <strong>the</strong> PublicSphere, and Political Change,” <strong>Foreign</strong> Affairs (January-February 2011).70. Joshua Goldste<strong>in</strong>, “The Role of <strong>Digital</strong> Networked Technologies <strong>in</strong> <strong>the</strong>Ukra<strong>in</strong>ian Orange Revolution,” Berkman Center for <strong>Internet</strong> and Society,Harvard University (December 2007).71. Myroslaw J. Kyj, “<strong>Internet</strong> Use <strong>in</strong> Ukra<strong>in</strong>e‘s Orange Revolution,” Bus<strong>in</strong>essHorizons, Issue 49 (2006): 71-80, http://web.reed.edu/alumni/images/AC_2010/pdfs/<strong>Internet</strong>%20Use%20<strong>in</strong>%20Orange%20Revolution.pdf.72. Marwan M. Kraidy, “Saudi Arabia, Lebanon and <strong>the</strong> Chang<strong>in</strong>g ArabInformation Order,” International Journal of Communication (2007), http://ijoc.org/ojs/<strong>in</strong>dex.php/ijoc/article/viewFile/18/22.73. Brannon Cullum, “Oscar Morales and One Million Voices Aga<strong>in</strong>st FARC,”Movements.org (no date), http://www.movements.org/case-study/entry/oscar-morales-and-one-million-voices-aga<strong>in</strong>st-farc/.74 . Maria Camila Pérez, “Facebook Br<strong>in</strong>gs Protest to Columbia,” The New YorkTimes (8 February 2008), http://www.nytimes.com/2008/02/08/bus<strong>in</strong>ess/worldbus<strong>in</strong>ess/08iht-protest11.html?_r=3.75. “Carnegie Guide to Egypt’s Elections – The April 6 Youth Movement,”Carnegie Endowment for International Peace, http://egyptelections.carnegieendowment.org/2010/09/22/<strong>the</strong>-april-6-youth-movement.76. Nathan Hodge, “Moldova Calm after Twitter Storm,” Wired Danger Roomblog (10 April 2009), http://www.wired.com/dangerroom/2009/04/moldovacalm-af/.77. “Moldova recount ‘confirms result,’” BBC (17 April 2009), http://news.bbc.co.uk/2/hi/europe/8004603.stm.78. Evgeny Morozov, “Kyrgyzstan’s ‘Analog Revolution,’” <strong>Foreign</strong> <strong>Policy</strong>’sNet Effect blog (8 April 2010), http://neteffect.foreignpolicy.com/posts/2010/04/08/kyrgyzstans_analog_revolution.79. Lisa Bryant, “<strong>Internet</strong> Powers Tunisian Protests,” Voice of America (17January 2011), http://www.voanews.com/english/news/africa/<strong>Internet</strong>-Powers-Tunisian-Protests-113868589.html.44 |
80. Lisa Bryant, “<strong>Internet</strong> Powers Tunisian Protests,” Voice of America (17January 2011), http://www.voanews.com/english/news/africa/<strong>Internet</strong>-Powers-Tunisian-Protests-113868589.html.81. Jennifer Preston, “Movement Began with Outrage and a Facebook PageThat Gave It an Outlet,” The New York Times (5 February 2011), http://www.nytimes.com/2011/02/06/world/middleeast/06face.html.82. “Estimated 2 Million People Protest In, Around Tahrir Square In CairoEgypt,” Cnewsworld.com, http://www.cnewsworld.com/world-news/middle-east-world-news/estimated-2-million-people-protest-<strong>in</strong>-_-aroundtahrir-square-<strong>in</strong>-cairo-egypt-mp4/.83. James Glanz, “How Mubarak Shut Down Egypt’s <strong>Internet</strong>,” The <strong>Age</strong>(Australia) (17 February 2011), http://www.<strong>the</strong>age.com.au/world/howmubarak-shut-down-egypts-<strong>in</strong>ternet-20110216-1awjj.html.84. Grant Gross, “Egyptian Activist: <strong>Internet</strong> Shutdown Backfired,” PC World(3 February 2011), http://www.pcworld.com/bus<strong>in</strong>esscenter/article/218630/egyptian_activist_<strong>in</strong>ternet_shutdown_backfired.html.85. See “Data Retention,” Electronic Privacy Information Center, http://epic.org/privacy/<strong>in</strong>tl/data_retention.html.86. “Tor: Sponsors,” http://www.torproject.org/about/sponsors.html.en.87. Experts at <strong>the</strong> Berman Center for <strong>Internet</strong> and Society at HarvardUniversity exam<strong>in</strong>ed virtual private networks (VPNs) <strong>in</strong> a thorough study oncircumvention technology <strong>in</strong> 2010. They expla<strong>in</strong> how <strong>the</strong>se networks operate:“VPN technology has traditionally been used to allow corporate and o<strong>the</strong>r<strong>in</strong>stitutional users to access <strong>in</strong>ternal networks from <strong>the</strong> public network, but<strong>in</strong> <strong>the</strong> past few years <strong>the</strong>re has been tremendous growth <strong>in</strong> <strong>the</strong> availabilityof personal VPN services. Among o<strong>the</strong>r uses, <strong>the</strong>se personal VPN services actas circumvention tools as long as <strong>the</strong> VPN proxy is hosted outside a filter<strong>in</strong>gcountry. VPN services might or might not require <strong>in</strong>stallation of client-sidesoftware (many rely on exist<strong>in</strong>g VPN support <strong>in</strong> W<strong>in</strong>dows or Mac OSX and soneed no extra client software) and allow <strong>the</strong> user to access <strong>the</strong> web directlythrough <strong>the</strong> native browser <strong>in</strong>terface. Because VPN services tunnel all <strong>Internet</strong>traffic, <strong>the</strong>y can be used for email, chat, and any o<strong>the</strong>r <strong>Internet</strong> service <strong>in</strong>addition to web brows<strong>in</strong>g. Almost all of <strong>the</strong>se tools support <strong>the</strong>mselvesthrough fees charged directly to users (charges of $10 to $30 per month arecommon), though a few also offer free services with restricted bandwidth.”Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris and John Palfrey,“2010 Circumvention Tool Usage Report,” Harvard Berkman Center for <strong>Internet</strong>and Society (October 2010): 4, http://cyber.law.harvard.edu/sites/cyber.law.harvard.edu/files/2010_Circumvention_Tool_Usage_Report.pdf.88 . Andrew Qu<strong>in</strong>n, “U.S. Develops ‘Panic Button’ for Democracy Activists,”Reuters (25 March 2011), http://www.reuters.com/article/2011/03/25/us-rights-usa-technology-idUSTRE72O6DH20110325.89. Maggie Shiels, “On Iran’s Virtual Front L<strong>in</strong>e,” BBC News (6 August 2009),http://news.bbc.co.uk/2/hi/technology/8186761.stm.90. Aleks Krotoski, “MediaGuardian Innovation Awards: Aust<strong>in</strong> Heap v Iran’scensors,” Guardian.co.uk (20 March 2010), http://www.guardian.co.uk/media/2010/mar/29/aust<strong>in</strong>-heap-megas-<strong>in</strong>novator-award.91. William J. Dobson, “Needles <strong>in</strong> a Haystack,” Newsweek (6 August 2010),http://www.newsweek.com/2010/08/06/needles-<strong>in</strong>-a-haystack.html.92. Evgeny Morozov, “The Great <strong>Internet</strong> <strong>Freedom</strong> Fraud,” Slate (16 September2010), http://www.slate.com/id/2267262.93. United States Senate Committee on <strong>Foreign</strong> Relations, Ano<strong>the</strong>r U.S. Deficit– Ch<strong>in</strong>a and America – Public Diplomacy <strong>in</strong> <strong>the</strong> <strong>Age</strong> of <strong>the</strong> <strong>Internet</strong> (15 February2011): 42, http://lugar.senate.gov/issues/foreign/diplomacy/Ch<strong>in</strong>a<strong>Internet</strong>.pdf.94. Desmond Ang, “Falun Gong helps crack Iran’s web filter,” ABCNews (Australia) (2 July 2009), http://www.abc.net.au/news/stories/2009/07/02/2614914.htm.95 . Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris and John Palfrey,“2010 Circumvention Tool Usage Report,” Berkman Center for <strong>Internet</strong> andSociety, Harvard University (October 2010): 6, http://cyber.law.harvard.edu/sites/cyber.law.harvard.edu/files/2010_Circumvention_Tool_Usage_Report.pdf.96. John Pomfret, “U.S. Risks Ch<strong>in</strong>a’s Ire with Decision to Fund SoftwareMaker Tied to Falun Gong,” The Wash<strong>in</strong>gton Post (12 May 2010), http://www.wash<strong>in</strong>gtonpost.com/wp-dyn/content/article/2010/05/11/AR2010051105154.html.97. Author conversation with U.S. government official (14 April 2011).98. Hillary Rodham Cl<strong>in</strong>ton, “<strong>Internet</strong> Rights and Wrongs: Choices &Challenges <strong>in</strong> a Networked World,” The George Wash<strong>in</strong>gton University,Wash<strong>in</strong>gton (15 February 2011), http://www.state.gov/secretary/rm/2011/02/156619.htm.99. United States Senate Committee on <strong>Foreign</strong> Relations, Ano<strong>the</strong>r U.S. Deficit– Ch<strong>in</strong>a and America – Public Diplomacy <strong>in</strong> <strong>the</strong> <strong>Age</strong> of <strong>the</strong> <strong>Internet</strong> (15 February2011): 4, http://lugar.senate.gov/issues/foreign/diplomacy/Ch<strong>in</strong>a<strong>Internet</strong>.pdf.100. Kathleen Hickey, “DARPA Looks for Stealthier <strong>Internet</strong> Access,” DefenseSystems (24 May 2010), http://defensesystems.com/articles/2010/05/21/darpa-safer-solicitation.aspx?admgarea=DS.101. The State Department has expressed <strong>in</strong>terest <strong>in</strong> fund<strong>in</strong>g some of <strong>the</strong>setechnologies. See U.S. Department of State, Jo<strong>in</strong>t Request for Statements ofInterest: <strong>Internet</strong> <strong>Freedom</strong> Programs (3 January 2011).102. Hillary Rodham Cl<strong>in</strong>ton, “<strong>Internet</strong> Rights and Wrongs: Choices &Challenges <strong>in</strong> a Networked World,” The George Wash<strong>in</strong>gton University,Wash<strong>in</strong>gton (15 February 2011), http://www.state.gov/secretary/rm/2011/02/156619.htm.103. This Tunis Commitment reaffirmed <strong>the</strong> 2003 Geneva Declaration ofPr<strong>in</strong>ciples, which held, “Communication is a fundamental social process, abasic human need and <strong>the</strong> foundation of all social organization. It is central to<strong>the</strong> Information Society. Everyone, everywhere should have <strong>the</strong> opportunity toparticipate and no one should be excluded from <strong>the</strong> benefits <strong>the</strong> InformationSociety offers.” “Tunis Commitment,” World Summit on <strong>the</strong> InformationSociety (18 November 2005), http://www.itu.<strong>in</strong>t/wsis/docs2/tunis/off/7.html.| 45
J U N E 2 0 1 1<strong>Internet</strong> <strong>Freedom</strong>A <strong>Foreign</strong> <strong>Policy</strong> <strong>Imperative</strong> <strong>in</strong> <strong>the</strong> <strong>Digital</strong> <strong>Age</strong>46 |104. David A. Gross, “Secur<strong>in</strong>g <strong>the</strong> Future of a Safe and Free <strong>Internet</strong>,”Remarks at <strong>the</strong> High Level Segment of <strong>the</strong> 2008 InternationalTelecommunication Union Council (12 November 2008).105. Sangamitra Ramachander, “Europe,” Open Net Initiative, http://opennet.net/research/regions/europe.106. CNAS’ companion study on cyber security employs <strong>the</strong> term “cybersecurity” to mean “A blanket term that encompasses both 1) <strong>in</strong>formationassurance (measures that protect and defend <strong>in</strong>formation and <strong>in</strong>formationsystems by ensur<strong>in</strong>g <strong>the</strong>ir availability, <strong>in</strong>tegrity, au<strong>the</strong>ntication, confidentialityand non-repudiation. This <strong>in</strong>cludes provid<strong>in</strong>g for restoration of <strong>in</strong>formationsystems by <strong>in</strong>corporat<strong>in</strong>g protection, detection, and reaction capabilities)and 2) and <strong>in</strong>formation security (protect<strong>in</strong>g <strong>in</strong>formation and <strong>in</strong>formationsystems from unauthorized access, use, disclosure, disruption, modification,or destruction).” “America’s Cyber Future: Security and Prosperity <strong>in</strong> <strong>the</strong>Information <strong>Age</strong>,” Center for a New American Security (June 2011).107. “The Information Security Doctr<strong>in</strong>e of <strong>the</strong> Russian Federation,” Embassyof <strong>the</strong> Russian Federation <strong>in</strong> <strong>the</strong> K<strong>in</strong>gdom of Cambodia (2 September 2000),http://www.embrusscambodia.mid.ru/doc-<strong>in</strong>formation-e.html.108. Will Englund, “In Russia, Official Proposes Curtail<strong>in</strong>g <strong>Internet</strong> <strong>Freedom</strong>,”The Wash<strong>in</strong>gton Post (8 April 2011), http://www.wash<strong>in</strong>gtonpost.com/world/<strong>in</strong>-russia-official-proposes-curtail<strong>in</strong>g-<strong>in</strong>ternet-freedom/2011/04/08/AFzUud2C_story.html.109. After <strong>the</strong> United Arab Emirates BlackBerry ban, U.S. State Departmentspokesman P.J. Crowley said, “We th<strong>in</strong>k it sets a dangerous precedent…You should be open<strong>in</strong>g up societies to <strong>the</strong>se new technologies that have<strong>the</strong> opportunity to empower people, ra<strong>the</strong>r than look<strong>in</strong>g to see how youcan restrict certa<strong>in</strong> technologies.” “U.S. Says UAE BlackBerry Ban SetsDangerous Precedent,” Reuters (2 August 2010), http://www.reuters.com/article/2010/08/02/us-uae-blackberry-usa-idUSTRE67144P20100802.110. Tom Gjelten, “See<strong>in</strong>g <strong>the</strong> <strong>Internet</strong> as an ‘Information Weapon,’” NationalPublic Radio (23 September 2010), http://www.npr.org/templates/story/story.php?storyId=130052701.111. Ibid.112. Details related to “Additional Protocol to <strong>the</strong> Convention on Cybercrime,Concern<strong>in</strong>g <strong>the</strong> Crim<strong>in</strong>alisation of Acts of a Racist and Xenophobic NatureCommitted Through Computer Systems” come from extraord<strong>in</strong>ary researchassistance by <strong>the</strong> Harvard Law National Security Research Group, under <strong>the</strong>direction of Ivana Deyrup. For U.S. concerns about <strong>the</strong> Additional Protocol,see U.S. Department of Justice, Council of Europe Convention on Cybercrime:Frequently Asked Questions and Answers, http://www.justice.gov/crim<strong>in</strong>al/cybercrime/COEFAQs.htm.113. More precisely, <strong>the</strong> <strong>in</strong>termediary is generally not liable unless itknow<strong>in</strong>gly hosts illegal material (e.g., content posted <strong>in</strong> violation of copyrightprotections) and refuses to remove it when notified.114. “Intermediary Liability: Protect<strong>in</strong>g <strong>Internet</strong> Platforms for Expressionand Innovation,” Center for Democracy and Technology (April 2010): 8, http://www.cdt.org/files/pdfs/CDT-Intermediary%20Liability_%282010%29.pdf.115. Sarah Lai Stirland, “Cisco Leak: ‘Great Firewall’ of Ch<strong>in</strong>a was a Chanceto Sell More Routers,” Wired (20 May 2008), http://www.wired.com/threatlevel/2008/05/leaked-cisco-do/.116. Paul Sonne and Steve Stecklow, “U.S. Products Help Block Mideast Web,”The Wall Street Journal (28 March 2011), http://onl<strong>in</strong>e.wsj.com/article/SB10001424052748704438104576219190417124226.html?mod=googlenews_wsj.117. Golnaz Esfandiari, “Nokia Faces Wrath of Iran’s Protestors,” Radio FreeEurope/Radio Liberty (15 July 2009), http://www.rferl.org/content/Nokia_Faces_Wrath_Of_Irans_Protesters/1777717.html.118. “<strong>Internet</strong> Enemies 2011: Burma,” Refworld (11 March 2011), http://www.unhcr.org/refworld/country,,,,MMR,,4d82269028,0.html; and“France, Ne<strong>the</strong>rlands Seek to Halt <strong>Internet</strong> Censorship,” <strong>Age</strong>nce FrancePresse (8 July 2010), http://www.google.com/hostednews/afp/article/ALeqM5hobAcoL50p4irWBiWSSkmM5BQ7Gg.119. “Censorship <strong>in</strong> Ch<strong>in</strong>a,” Amnesty International, http://www.amnestyusa.org/bus<strong>in</strong>ess-and-human-rights/technology/page.do?id=1101572.120. “Pr<strong>in</strong>ciples - <strong>Freedom</strong> of Expression,” Global Network Initiative (no date)http://www.globalnetwork<strong>in</strong>itiative.org/pr<strong>in</strong>ciples/<strong>in</strong>dex.php#18.121. Accord<strong>in</strong>g to <strong>the</strong> Global Network Initiative’s (GNI) Governance Charter,membership <strong>in</strong> <strong>the</strong> GNI can be term<strong>in</strong>ated for “Failure to meet report<strong>in</strong>gor o<strong>the</strong>r participation requirements [and] Failure to meet compliance andevaluation requirements.” “Governance Charter,” Global Network Initiative,Section 4D, http://www.globalnetwork<strong>in</strong>itiative.org/charter/<strong>in</strong>dex.php#83.122. Office of Senator Richard Durb<strong>in</strong>, “Durb<strong>in</strong>, Coburn Cont<strong>in</strong>ue to Press TechCompanies on Human Rights Code of Conduct” (7 August 2009), http://durb<strong>in</strong>.senate.gov/showRelease.cfm?releaseId=316922.123. Chloe Albanesius, “Egypt Turns to Sole Provider, Dial-Up for <strong>Internet</strong>Access,” PC Magaz<strong>in</strong>e (31 January 2011), http://www.pcmag.com/article2/0,2817,2378969,00.asp.124. Chris Lefkow, “Google, Facebook, Twitter sound off on Egypt,” <strong>Age</strong>nceFrance-Presse (2 February 2011).125. Margaret Coker and Charles Lev<strong>in</strong>son, “Rebels Hijack Gadhafi’s PhoneNetwork,” The Wall Street Journal (13 April 2011), http://onl<strong>in</strong>e.wsj.com/article/SB10001424052748703841904576256512991215284.html.126. Hillary Rodham Cl<strong>in</strong>ton, “Remarks on <strong>Internet</strong> <strong>Freedom</strong>,” <strong>the</strong>Newseum, Wash<strong>in</strong>gton (21 January 2010), http://www.state.gov/secretary/rm/2010/01/135519.htm.127. Ed Black, “Google, <strong>the</strong> <strong>Internet</strong> and Ch<strong>in</strong>a: A Nexus Between HumanRights and Trade?” Testimony before <strong>the</strong> Congressional Executive Committeeon Ch<strong>in</strong>a (24 March 2010).128. Korea-U.S. Free Trade Agreement, Article 15.8 “Cross Border InformationFlows” (1 June 2007), http://www.ustr.gov/sites/default/files/uploads/agreements/fta/korus/asset_upload_file816_12714.pdf.
129. Mark Lander, “U.S. Hopes Exports Will Help Open Societies,” The New YorkTimes (7 March 2010), http://www.nytimes.com/2010/03/08/world/08export.html.130. “BIS Updates Encryption Export Rule; Revised Rule Streaml<strong>in</strong>es ReviewProcess, Enhances National Security,” Department of Commerce Bureau ofIndustry and Security (25 June 2010), http://www.bis.doc.gov/news/2010/bis_press06252010.htm.131. As an example of one way <strong>in</strong> which U.S. export controls can chill onl<strong>in</strong>efreedom, Evgeny Morozov cites <strong>the</strong> case of Yaraslau Kryvoi, a Wash<strong>in</strong>gtonbasedBelarusian whose web-host<strong>in</strong>g firm suspended its blog becauseBelarus was subject to U.S. trade sanctions. Evgeny Morozov, “Do-It-Yourself Censorship,” Newsweek (7 March 2009), http://www.newsweek.com/2009/03/06/do-it-yourself-censorship.html.132. John Markoff, “At <strong>Internet</strong> Conference, Signs of Agreement AppearBetween U.S. and Russia,” The New York Times (15 April 2010), http://www.nytimes.com/2010/04/16/science/16cyber.html.133. Ryan S<strong>in</strong>gel, “Cyberwar Hype Intended to Destroy <strong>the</strong> Open <strong>Internet</strong>,” Wired(1 March 2010), http://www.wired.com/threatlevel/2010/03/cyber-war-hype/.134. David Talbot, “Dissent Made Safer,” Technology Review (May/June 2009),http://www.technologyreview.com/pr<strong>in</strong>ter_friendly_article.aspx?id=22427.Also see question by Harvard Law School’s John Palfrey to Ron Deibert,Director of <strong>the</strong> University of Toronto’s Citizen Lab: “What’s go<strong>in</strong>g to happenwhen someone does someth<strong>in</strong>g terrible us<strong>in</strong>g Psiphon, plans a terroristattack, for <strong>in</strong>stance? What’s Psiphon’s liability?” Ethan Zuckerman, “RonDeibert on <strong>the</strong> History and Future of Psiphon,” My Heart’s <strong>in</strong> Accra (31 January2007), http://www.ethanzuckerman.com/blog/2007/01/31/ron-deibert-on<strong>the</strong>-history-and-future-of-psiphon/.135. For example, Robert Vamosi writes that “TOR is endorsed by <strong>the</strong>Electronic Frontier Foundation (EFF) and is designed for <strong>in</strong>dividuals tocircumvent Web censorship <strong>in</strong> countries such as Ch<strong>in</strong>a, however, <strong>the</strong> networkcould be used by crim<strong>in</strong>als or even terrorists.” Robert Vamois, “Hack<strong>in</strong>gAnonymity,” CNET Reviews (20 October 2006), http://reviews.cnet.com/4520-3513_7-6654986-1.html?tag=untagged.136. The FBI and o<strong>the</strong>r U.S. government agencies have been relativelyvocal about <strong>the</strong>ir concerns regard<strong>in</strong>g anonymity provided by encryptiontechnologies for over a decade. In 1998, The Wash<strong>in</strong>gton Post reported that“FBI Director Louis Freeh is <strong>the</strong> most outspoken advocate of encryptionrestrictions … now, Freeh compla<strong>in</strong>s, new technology is help<strong>in</strong>g crim<strong>in</strong>alsmore than <strong>the</strong> police. One Freeh proposal is that all users of powerfulencryption software be asked to turn over <strong>the</strong>ir keys to a third party, sothat law-enforcement officials can ga<strong>in</strong> access to <strong>the</strong>m with a court order.”More recently, Dr. Marco Gercke, director of <strong>the</strong> Cybercrime ResearchInstitute, wrote “Encryption is a classic example of a neutral technology,s<strong>in</strong>ce as it is not only used to h<strong>in</strong>der <strong>in</strong>vestigations but also to preventunauthorized access to <strong>in</strong>formation … The latest operat<strong>in</strong>g systems offer<strong>the</strong> possibility to encrypt computer data with <strong>the</strong> click of a mouse, mak<strong>in</strong>git difficult for law enforcement agencies to break <strong>the</strong> encryption andaccess <strong>the</strong> data.”Dan Froomk<strong>in</strong>, “Decipher<strong>in</strong>g Encryption,” The Wash<strong>in</strong>gtonPost (8 May 1998) and Dr. Marco Gercke, “From Encryption to Failure ofTraditional Investigation Instruments,” <strong>Freedom</strong> From Fear Magaz<strong>in</strong>e,http://www.freedomfromfearmagaz<strong>in</strong>e.org/<strong>in</strong>dex.php?option=com_content&view=article&id=311:from-encryption-to-failure-of-traditional<strong>in</strong>vestigation-<strong>in</strong>struments&catid=50:issue-7&Itemid=187.137. “Clipper Trip,” Crypto Museum, http://www.cryptomuseum.com/crypto/usa/clipper.htm.138. Evgeny Morozov, The Net Delusion (New York: PublicAffairs Books, 2011):176.139. Jaikumar Vijayan, “U.S. Web Site Said to Offer Streng<strong>the</strong>nedEncryption Tool for Al Qaeda Backers,” Computerworld(23 January 2008), http://www.computerworld.com/s/article/9058619/U.S._Web_site_said_to_offer_streng<strong>the</strong>ned_encryption_tool_for_al_Qaeda_backers?taxonomyId=16&<strong>in</strong>tsrc=hm_topic.140. Ellen Nakashima, “Pentagon Considers Preemptive Strikes as Part ofCyber-Defense Strategy,” The Wash<strong>in</strong>gton Post (28 August 2010), http://www.wash<strong>in</strong>gtonpost.com/wp-dyn/content/article/2010/08/28/AR2010082803849.html.141. “We have to have offensive capabilities, to, <strong>in</strong> real time, shut downsomebody try<strong>in</strong>g to attack us,” said GEN Keith Alexander. “You needautonomous decision logic that’s based on <strong>the</strong> rule of law, <strong>the</strong> legalframework, to let network defenders know what <strong>the</strong>y are allowed to do <strong>in</strong><strong>the</strong> network’s defense.” C. Todd Lopez, “LandWarNet opens with 4 keys to<strong>Internet</strong> security,” Army News Service (3 August 2010), http://www.army.mil/-news/2010/08/04/43256-landwarnet-opens-with-4-keys-to-<strong>in</strong>ternetsecurity/.142. See <strong>the</strong> Protect<strong>in</strong>g Cyberspace as a National Asset Act of 2010, <strong>in</strong>troducedby Senators Joe Lieberman, I-Conn., Susan Coll<strong>in</strong>s, R-Ma<strong>in</strong>e and Ted Carper,D-Del.; <strong>the</strong> senators <strong>in</strong> February 2011 <strong>in</strong>troduced a reworked bill, <strong>the</strong>Cybersecurity and <strong>Internet</strong> <strong>Freedom</strong> Act.143. Declan McCullagh, “<strong>Internet</strong> ‘Kill Switch’ Bill Gets a Makeover,” CNET News(18 February 2011), http://news.cnet.com/8301-31921_3-20033717-281.html.144. Shawna Shepherd, “White House conference tackles bully<strong>in</strong>g,” CNN (10March 2011), http://www.cnn.com/2011/POLITICS/03/10/obama.bully<strong>in</strong>g/<strong>in</strong>dex.html.145. Department of State, Jo<strong>in</strong>t Request for Statements of Interest: <strong>Internet</strong><strong>Freedom</strong> Programs (3 January 2011).146. Ibid.147. As Rebecca MacK<strong>in</strong>non has suggested, had Ch<strong>in</strong>ese dissident Shi Taounderstood that Yahoo could share his email with Ch<strong>in</strong>ese police forces, hemay have found more secure methods of transmitt<strong>in</strong>g articles to dissidentwebsites. Rebecca MacK<strong>in</strong>non, “Ch<strong>in</strong>a, <strong>the</strong> <strong>Internet</strong>, and Google,” Testimonybefore <strong>the</strong> Congressional-Executive Commission on Ch<strong>in</strong>a (1 March 2010): 7.148. U.S. laws currently restrict exports to Syria. For more on <strong>the</strong> restrictionsand <strong>the</strong>ir effects on Syrian <strong>Internet</strong> users, see Jillian York, “U.S. Gives Iran MoreNet <strong>Freedom</strong> – But What About Syria?” Guardian.co.uk (16 June 2010), http://www.guardian.co.uk/commentisfree/libertycentral/2010/jun/16/<strong>in</strong>ternetiran-syria-export-controls.| 47
About <strong>the</strong> Center for aNew American SecurityThe mission of <strong>the</strong> Center for a New AmericanSecurity (CNAS) is to develop strong,pragmatic, and pr<strong>in</strong>cipled national securityand defense policies. Build<strong>in</strong>g on <strong>the</strong> expertiseand experience of its staff and advisors, CNASaims to engage policymakers, experts and <strong>the</strong>public with <strong>in</strong>novative fact-based research,ideas, and analysis to shape and elevate <strong>the</strong>national security debate. A key part of ourmission is to help <strong>in</strong>form and prepare <strong>the</strong>national security leaders of today and tomorrow.CNAS is located <strong>in</strong> Wash<strong>in</strong>gton, D.C., and wasestablished <strong>in</strong> February 2007 by Co-foundersKurt M. Campbell and Michèle A. Flournoy. CNASis a 501(c)3 tax-exempt nonprofit organization.Its research is nonpartisan; CNAS does not takespecific policy positions. Accord<strong>in</strong>gly, all views,positions, and conclusions expressed <strong>in</strong> thispublication should be understood to be solelythose of <strong>the</strong> authors.© 2011 Center for a New American Security.All rights reserved.Center for a New American Security1301 Pennsylvania Avenue, NWSuite 403Wash<strong>in</strong>gton, DC 20004TEL 202.457.9400FAX 202.457.9401EMAIL <strong>in</strong>fo@cnas.orgwww.cnas.orgProduction NotesPaper recycl<strong>in</strong>g is reprocess<strong>in</strong>g waste paper fibers back <strong>in</strong>toa usable paper product.Soy <strong>in</strong>k is a helpful component <strong>in</strong> paper recycl<strong>in</strong>g. It helps <strong>in</strong> thisprocess because <strong>the</strong> soy <strong>in</strong>k can be removed more easily thanregular <strong>in</strong>k and can be taken out of paper dur<strong>in</strong>g <strong>the</strong> de-<strong>in</strong>k<strong>in</strong>gprocess of recycl<strong>in</strong>g. This allows <strong>the</strong> recycled paper to have lessdamage to its paper fibers and have a brighter appearance.The waste that is left from <strong>the</strong> soy <strong>in</strong>k dur<strong>in</strong>g <strong>the</strong> de-<strong>in</strong>k<strong>in</strong>gprocess is not hazardous and it can be treated easily through<strong>the</strong> development of modern processes.
Strong, Pragmatic and Pr<strong>in</strong>cipledNational Security and Defense Policies1301 Pennsylvania Avenue, NWSuite 403Wash<strong>in</strong>gton, DC 20004Tel 202.457.9400Fax 202.457.9401Email <strong>in</strong>fo@cnas.orgwww.cnas.orgPr<strong>in</strong>ted on Post-Consumer Recycled paper with Soy Inks