ARM Security Technology Building a Secure System using ...
ARM Security Technology Building a Secure System using ...
ARM Security Technology Building a Secure System using ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Introduction<br />
1.2 The need for security<br />
1.2.1 Hardware enforced security<br />
Embedded devices are handling data of increasing value, such as consumer banking<br />
credentials. They are also steadily becoming open software platforms with high levels<br />
of off-device connectivity that enable the consumer to download arbitrary third-party<br />
applications. This puts these devices in a high risk position. In the desktop environment<br />
the combination of open software platforms, arbitrary application download, and<br />
valuable assets present on the device, have been shown to significantly increase the risk<br />
of a security vulnerability being exploited. Additionally, if the value of data passing<br />
through these systems is increasing, it is more likely that attackers will invest in<br />
breaking them.<br />
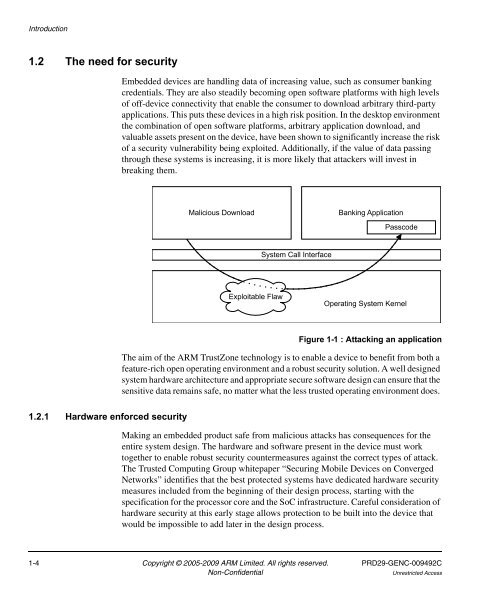
Malicious Download<br />
Exploitable Flaw<br />
<strong>System</strong> Call Interface<br />
Banking Application<br />
Passcode<br />
Operating <strong>System</strong> Kernel<br />
Figure 1-1 : Attacking an application<br />
The aim of the <strong>ARM</strong> TrustZone technology is to enable a device to benefit from both a<br />
feature-rich open operating environment and a robust security solution. A well designed<br />
system hardware architecture and appropriate secure software design can ensure that the<br />
sensitive data remains safe, no matter what the less trusted operating environment does.<br />
Making an embedded product safe from malicious attacks has consequences for the<br />
entire system design. The hardware and software present in the device must work<br />
together to enable robust security countermeasures against the correct types of attack.<br />
The Trusted Computing Group whitepaper “Securing Mobile Devices on Converged<br />
Networks” identifies that the best protected systems have dedicated hardware security<br />
measures included from the beginning of their design process, starting with the<br />
specification for the processor core and the SoC infrastructure. Careful consideration of<br />
hardware security at this early stage allows protection to be built into the device that<br />
would be impossible to add later in the design process.<br />
1-4 Copyright © 2005-2009 <strong>ARM</strong> Limited. All rights reserved. PRD29-GENC-009492C<br />
Non-Confidential Unrestricted Access