Security - Telenor
Security - Telenor
Security - Telenor
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Before continuing, A must examine M to see if it<br />
constitutes an acceptance or refusal on B 1 ’s part.<br />
If it is a refusal, the protocol is finished. If it is<br />
an acceptance, the protocol continues for the initial<br />
platform as follows:<br />
3. A m3<br />
→ B1 :<br />
As(A, B1,iA,B1p(KA))<br />
m4<br />
4. B1 → A :<br />
B1s(B1,A,iA,H(m3))<br />
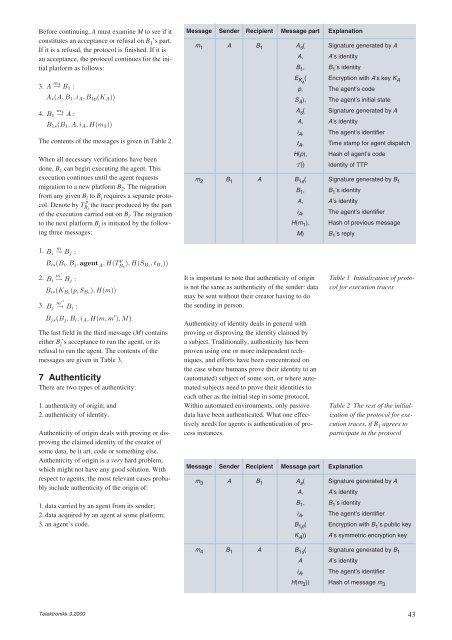
The contents of the messages is given in Table 2.<br />
When all necessary verifications have been<br />
done, B1 can begin executing the agent. This<br />
execution continues until the agent requests<br />
migration to a new platform B2 . The migration<br />
from any given Bi to Bj requires a separate protocol.<br />
Denote by T p<br />
B the trace produced by the part<br />
i<br />
of the execution carried out on Bi . The migration<br />
to the next platform Bj is initiated by the following<br />
three messages:<br />
1.<br />
m<br />
2. Bi<br />
′<br />
→ Bj :<br />
Bis(KBi(p, SBi),H(m))<br />
3.<br />
m<br />
Bi → Bj :<br />
Bis(Bi,Bj, agentA,H(T p<br />
Bi ),H(SBi,tBi))<br />
m<br />
Bj<br />
′′<br />
→ Bi :<br />
Bjs(Bj,Bi,iA,H(m, m ′ ),M)<br />
The last field in the third message (M) contains<br />
either B j ’s acceptance to run the agent, or its<br />
refusal to run the agent. The contents of the<br />
messages are given in Table 3.<br />
7 Authenticity<br />
There are two types of authenticity:<br />
1. authenticity of origin; and<br />
2. authenticity of identity.<br />
Authenticity of origin deals with proving or disproving<br />
the claimed identity of the creator of<br />
some data, be it art, code or something else.<br />
Authenticity of origin is a very hard problem,<br />
which might not have any good solution. With<br />
respect to agents, the most relevant cases probably<br />
include authenticity of the origin of:<br />
1. data carried by an agent from its sender;<br />
2. data acquired by an agent at some platform;<br />
3. an agent’s code.<br />
Telektronikk 3.2000<br />
Message Sender Recipient Message part Explanation<br />
m1 A B1 As ( Signature generated by A<br />
A, A’s identity<br />
B1 , B1 ’s identity<br />
EKA ( Encryption with A’s key KA p, The agent’s code<br />
SA ), The agent’s initial state<br />
As ( Signature generated by A<br />
A, A’s identity<br />
iA , The agent’s identifier<br />
tA , Time stamp for agent dispatch<br />
H(p), Hash of agent’s code<br />
T)) Identity of TTP<br />
m2 B1 A B1s ( Signature generated by B1 B1 , B1 ’s identity<br />
A, A’s identity<br />
iA , The agent’s identifier<br />
H(m1 ), Hash of previous message<br />
M) B1 ’s reply<br />
It is important to note that authenticity of origin<br />
is not the same as authenticity of the sender: data<br />
may be sent without their creator having to do<br />
the sending in person.<br />
Authenticity of identity deals in general with<br />
proving or disproving the identity claimed by<br />
a subject. Traditionally, authenticity has been<br />
proven using one or more independent techniques,<br />
and efforts have been concentrated on<br />
the case where humans prove their identity to an<br />
(automated) subject of some sort, or where automated<br />
subjects need to prove their identities to<br />
each other as the initial step in some protocol.<br />
Within automated environments, only passive<br />
data have been authenticated. What one effectively<br />
needs for agents is authentication of process<br />
instances.<br />
Message Sender Recipient Message part Explanation<br />
Table 1 Initialization of protocol<br />
for execution traces<br />
Table 2 The rest of the initialization<br />
of the protocol for execution<br />
traces, if B 1 agrees to<br />
participate in the protocol<br />
m3 A B1 As ( Signature generated by A<br />
A, A’s identity<br />
B1 , B1 ’s identity<br />
iA , The agent’s identifier<br />
B1p ( Encryption with B1 ’s public key<br />
KA )) A’s symmetric encryption key<br />
m4 B1 A B1s ( Signature generated by B1 A A’s identity<br />
iA , The agent’s identifier<br />
H(m3 )) Hash of message m3 43