- Page 1:
The C11 and C++11 Concurrency Model
- Page 5:
Mark John Batty The C11 and C++11 C
- Page 8 and 9:
8 3.5.1 Release sequences . . . . .
- Page 10 and 11:
10 B.1 The pre-execution type . . .
- Page 12 and 13:
12
- Page 14 and 15:
14 stores to memory are interleaved
- Page 16 and 17:
16 still, relaxed-concurrencybugsca
- Page 18 and 19:
18 to sequential consistency [37],
- Page 20 and 21:
20 ory model. It has been used for
- Page 22 and 23:
22 by Dubois et al. [48]. C/C++11 c
- Page 24 and 25:
24 There has been some work on veri
- Page 26 and 27:
26 int x = 0; int y = 0; x = 1; y =
- Page 28 and 29:
28 On the SC memory model this prog
- Page 30 and 31:
30 The x86 architecture provides th
- Page 32 and 33:
32 Write request Read request Barri
- Page 34 and 35:
34 coherence-commitment order restr
- Page 36 and 37:
36 Multi-copy atomicity Some memory
- Page 38 and 39:
38 Further details of the Power and
- Page 40 and 41:
40 they can be guaranteed with no d
- Page 42 and 43:
42 indivisible events that affect t
- Page 44 and 45:
44 undefined behaviour. In the prog
- Page 46 and 47:
46 On each architecture, this is su
- Page 48 and 49:
48
- Page 50 and 51:
50 sublanguages and the related par
- Page 52 and 53:
52 int main() { int x = 2; int y =
- Page 54 and 55:
54 a:W NA x=0 sb int main() { int x
- Page 56 and 57:
56 effects of a particular read are
- Page 58 and 59:
58 | Blocked rmw l → lk l = Atomi
- Page 60 and 61:
60 let det read (Xo, Xw, :: (“vse
- Page 62 and 63:
62 let indeterminate reads (Xo, Xw,
- Page 64 and 65:
64 let single thread memory model =
- Page 66 and 67:
66 becomes: int main() { int x = 0;
- Page 68 and 69:
68 additional-synchronises-withedge
- Page 70 and 71:
70 let locks only consistent locks
- Page 72 and 73:
72 let data races (Xo, Xw, (“hb
- Page 74 and 75:
74 = ( (¬ (a = b)) ∧ is write a
- Page 76 and 77:
76 the atomic location is accessed.
- Page 78 and 79:
78 Message passing, MP The first ex
- Page 80 and 81:
80 a:W NA x=0 sb rf b:W NA y=0 rf r
- Page 82 and 83:
82 the C/C++11 analogue of the test
- Page 84 and 85: 84 On Power and ARM, the analogue o
- Page 86 and 87: 86 stores of this fragment of the l
- Page 88 and 89: 88 int main() { atomic_int x = 0; a
- Page 90 and 91: 90 int main() { int x = 0; atomic_i
- Page 92 and 93: 92 and ARM all guarantee that each
- Page 94 and 95: 94 Release fences In the example in
- Page 96 and 97: 96 ( is fence a ∧ is release a
- Page 98 and 99: 98 3.7 Programs with SC atomics Pro
- Page 100 and 101: 100 not forbid the store-buffering
- Page 102 and 103: 102 int main() { atomic_int x = 0;
- Page 104 and 105: 104 ( (w, w ′ ) ∈ Xw.mo ∧ (w
- Page 106 and 107: 106 int main() { atomic_int x = 0;
- Page 108 and 109: 108 conjunct of sc fenced sc fences
- Page 110 and 111: 110 int main() { int x = 0; atomic_
- Page 112 and 113: 112 let r = sw ∪ dob ∪ (compose
- Page 114 and 115: 114 of the read. This write forms t
- Page 116 and 117: 116
- Page 118 and 119: 118 behaviour of the memory model.
- Page 120 and 121: 120 At the top right, there are con
- Page 122 and 123: 122 int main() { atomic_int x = 0;
- Page 124 and 125: 124 A release sequence headed by a
- Page 126 and 127: 126 [ Note: The visible sequence of
- Page 128 and 129: 128 int main() { atomic_int x = 0;
- Page 130 and 131: 130 5.6 Undefined loops In C/C++11
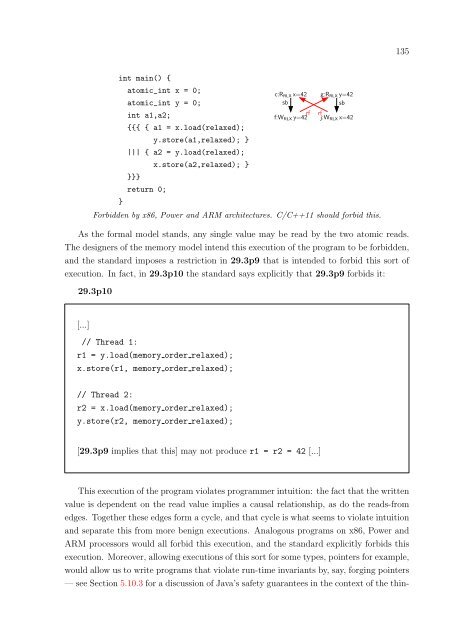
- Page 132 and 133: 132 Next consider the execution bel
- Page 136 and 137: 136 air problem. It seems clear the
- Page 138 and 139: 138 void main() { atomic_int x = 0;
- Page 140 and 141: 140 5.10.2 Possible solutions One c
- Page 142 and 143: 142 programs with thin-air values w
- Page 144 and 145: 144 Java introduces a great deal of
- Page 146 and 147: 146 int main() { atomic_int x = 2;
- Page 148 and 149: 148
- Page 150 and 151: 150 standard model T. 1 with consum
- Page 152 and 153: 152 tions, or they both produce und
- Page 154 and 155: 154 the two models are almost ident
- Page 156 and 157: 156 h, in the acyclic relation mo.
- Page 158 and 159: 158 | RMW mo → (mo ∈ {Acq rel,
- Page 160 and 161: 160 Programs without SC atomics Rem
- Page 162 and 163: 162 match a with | Lock → true |
- Page 164 and 165: 164 Theorem 8. (∀ opsem p. static
- Page 166 and 167: 166 is release rel ∧ ( (b = rel)
- Page 168 and 169: 168 Now we show that this equivalen
- Page 170 and 171: 170 is a dynamic property that can
- Page 172 and 173: 172 standard model T. 1 with consum
- Page 174 and 175: 174 [...][ Note: It can be shown th
- Page 176 and 177: 176 • consistent hb Furthermore,
- Page 178 and 179: 178 | Load mo → (mo ∈ {NA, Seq
- Page 180 and 181: 180 The induction will proceed by a
- Page 182 and 183: 182 exists a consistent execution i
- Page 184 and 185:
184 The domain and range of hbscr i
- Page 186 and 187:
186 implies that there is no tot in
- Page 188 and 189:
188 There are two directions to est
- Page 190 and 191:
190 incorporates the new action. Th
- Page 192 and 193:
192 Now for each sort of fault, we
- Page 194 and 195:
194 Theorem 14. For a program that
- Page 196 and 197:
196 we need only show that the sc-o
- Page 198 and 199:
198
- Page 200 and 201:
200 This chapter presents theorems
- Page 202 and 203:
202 C++0x actions a:W NA x=1 d:R AC
- Page 204 and 205:
204 and consume atomics require the
- Page 206 and 207:
206 Thread 0 has an lwsync as in th
- Page 208 and 209:
208 The thread and storage subsyste
- Page 210 and 211:
210 we know that any inter-thread h
- Page 212 and 213:
212
- Page 214 and 215:
214 behaviour in the specification.
- Page 216 and 217:
216 atomic Seq S; void init() { sto
- Page 218 and 219:
218 Message passing (MP): int a, b,
- Page 220 and 221:
220 in composition with a client wi
- Page 222 and 223:
222 tation in an arbitrary client c
- Page 224 and 225:
224 push and pop in an execution. T
- Page 226 and 227:
226 execution of the component exte
- Page 228 and 229:
228 Then for some Z ∈ C(L 2 )(I
- Page 230 and 231:
230
- Page 232 and 233:
232 it is possible to identify erra
- Page 234 and 235:
234 The release-sequence of C/C++11
- Page 236 and 237:
236 mer’s memory model. The CPU a
- Page 238 and 239:
238 17.3 defines additional terms t
- Page 240 and 241:
240 and the other is not, or if the
- Page 242 and 243:
242 abstract machine with the same
- Page 244 and 245:
244 a = ((a + b) + 32765); since if
- Page 246 and 247:
246 | RMW of aid ∗ tid ∗ memory
- Page 248 and 249:
248 not otherwise specifically sequ
- Page 250 and 251:
250 gram can potentially access eve
- Page 252 and 253:
252 acquire fence, a release fence,
- Page 254 and 255:
254 This relation does not order th
- Page 256 and 257:
256 performs a consume operation on
- Page 258 and 259:
258 • A is sequenced before B, or
- Page 260 and 261:
260 The model represents visible si
- Page 262 and 263:
262 where the three relations disag
- Page 264 and 265:
264 CoRW In this coherence violatio
- Page 266 and 267:
266 referred to as “sequential co
- Page 268 and 269:
268 29 Atomic operations library [a
- Page 270 and 271:
270 In the model, the memory order
- Page 272 and 273:
272 [...]) (∃c∈actions. (a, c)
- Page 274 and 275:
274 4 For an atomic operation B tha
- Page 276 and 277:
276 ForatomicoperationsAandB onanat
- Page 278 and 279:
278 However, implementations should
- Page 280 and 281:
280 | RMW l → lk l = Atomic | Fen
- Page 282 and 283:
282 The model captures these potent
- Page 284 and 285:
284 bool atomic_compare_exchange_we
- Page 286 and 287:
286 expected = current.load(); do {
- Page 288 and 289:
288 31 Effects: fetch key(operand)
- Page 290 and 291:
290 [...] (a, x) ∈ sb ∧ (x, y)
- Page 292 and 293:
292 extern "C" void atomic_signal_f
- Page 294 and 295:
294 30.3.1.2 thread constructors [t
- Page 296 and 297:
296 Header synopsis [elided] 30.4.
- Page 298 and 299:
298 The behaviour of locks and unlo
- Page 300 and 301:
300 9 Postcondition: The calling th
- Page 302 and 303:
302 let locks only bad mutexes (Xo,
- Page 304 and 305:
304 after the unlock call returns.
- Page 306 and 307:
306 |〉 threads : set (tid); lk :
- Page 308 and 309:
308 let aid of a = match a with | L
- Page 310 and 311:
310 Effects: Blocks the calling thr
- Page 312 and 313:
312 atomic location. On failure the
- Page 314 and 315:
314 Requires: The failure argument
- Page 316 and 317:
316 | Fence mo → mo ∈ {Release,
- Page 318 and 319:
318
- Page 320 and 321:
320 The thread-local semantics coll
- Page 322 and 323:
322 B.2.2 Modification order Modifi
- Page 324 and 325:
324 isIrreflexive Xw.lo ∧ ∀ a
- Page 326 and 327:
326 A release sequence headed by a
- Page 328 and 329:
328 creation, mutex accesses, atomi
- Page 330 and 331:
330
- Page 332 and 333:
332 An atomic operation A that is a
- Page 334 and 335:
334 B.3.5 Dependency ordered before
- Page 336 and 337:
336 the inter-thread-happens-before
- Page 338 and 339:
338 B.3.9 Visible sequence of side
- Page 340 and 341:
340 B.4.1 Coherence The previous se
- Page 342 and 343:
342 The coherence restriction These
- Page 344 and 345:
344 Second read-from derivative In
- Page 346 and 347:
346 To cover the second and third c
- Page 348 and 349:
348 This restriction requires reads
- Page 350 and 351:
350 [...]If a side effect on a scal
- Page 352 and 353:
352 The model captures these potent
- Page 354 and 355:
354 successful to have an interveni
- Page 356 and 357:
356 each empty M.undefined X then D
- Page 358 and 359:
358 type program impl = nat type ti
- Page 360 and 361:
360 let named predicate tree measur
- Page 362 and 363:
362 C.3 Projection functions let ai
- Page 364 and 365:
364 | RMW → true | → false end
- Page 366 and 367:
366 | Store mo → mo = Seq cst | R
- Page 368 and 369:
368 blocking observed Xo.actions Xo
- Page 370 and 371:
370 a ′ ∈ fringe set Xo ′ A
- Page 372 and 373:
372 val indeterminate reads : candi
- Page 374 and 375:
374 let locks only consistent locks
- Page 376 and 377:
376 val locks only behaviour : ∀
- Page 378 and 379:
378 |〉 〈| rf flag = true; mo fl
- Page 380 and 381:
380 (“release acquire coherent me
- Page 382 and 383:
382 val release acquire relaxed beh
- Page 384 and 385:
384 behaviourrelease acquire fenced
- Page 386 and 387:
386 ∀ (Xo, Xw, rl) ∈ Xs. ∀ a
- Page 388 and 389:
388 let sc fenced behaviour opsem (
- Page 390 and 391:
390 behaviour with consume memory m
- Page 392 and 393:
392 let release acquire SC conditio
- Page 394 and 395:
394 let bounded executions (Xs : se
- Page 396 and 397:
396 { (a, b) | ∀ a ∈ Xo.actions
- Page 398 and 399:
398 statically satisfied single thr
- Page 400 and 401:
400 let vse = visible side effect s
- Page 402 and 403:
402
- Page 404 and 405:
404 [15] J. Alglave, D. Kroening, V
- Page 406 and 407:
406 [42] L. Censier and P. Feautrie
- Page 408 and 409:
408 [68] S. Mador-Haim, L. Maranget
- Page 410 and 411:
410 ization and analysis of message
- Page 412 and 413:
Index actions, 41, 245 additional s
- Page 414:
414 Last updated: Saturday 29 th No