IMSI Catchers and Mobile Security
EAS499Honors-IMSICatchersandMobileSecurity-V18F-1
EAS499Honors-IMSICatchersandMobileSecurity-V18F-1
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
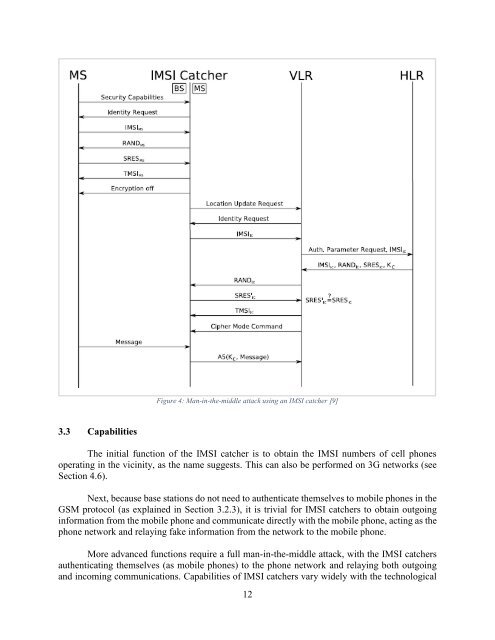
Figure 4: Man-in-the-middle attack using an <strong>IMSI</strong> catcher [9]<br />
3.3 Capabilities<br />
The initial function of the <strong>IMSI</strong> catcher is to obtain the <strong>IMSI</strong> numbers of cell phones<br />
operating in the vicinity, as the name suggests. This can also be performed on 3G networks (see<br />
Section 4.6).<br />
Next, because base stations do not need to authenticate themselves to mobile phones in the<br />
GSM protocol (as explained in Section 3.2.3), it is trivial for <strong>IMSI</strong> catchers to obtain outgoing<br />
information from the mobile phone <strong>and</strong> communicate directly with the mobile phone, acting as the<br />
phone network <strong>and</strong> relaying fake information from the network to the mobile phone.<br />
More advanced functions require a full man-in-the-middle attack, with the <strong>IMSI</strong> catchers<br />
authenticating themselves (as mobile phones) to the phone network <strong>and</strong> relaying both outgoing<br />
<strong>and</strong> incoming communications. Capabilities of <strong>IMSI</strong> catchers vary widely with the technological<br />
12