IMSI Catchers and Mobile Security
EAS499Honors-IMSICatchersandMobileSecurity-V18F-1
EAS499Honors-IMSICatchersandMobileSecurity-V18F-1
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
The possible cipher modes include:<br />
A5/0 – no encryption<br />
A5/1<br />
A5/2<br />
A5/3 – based on the KASUMI algorithm<br />
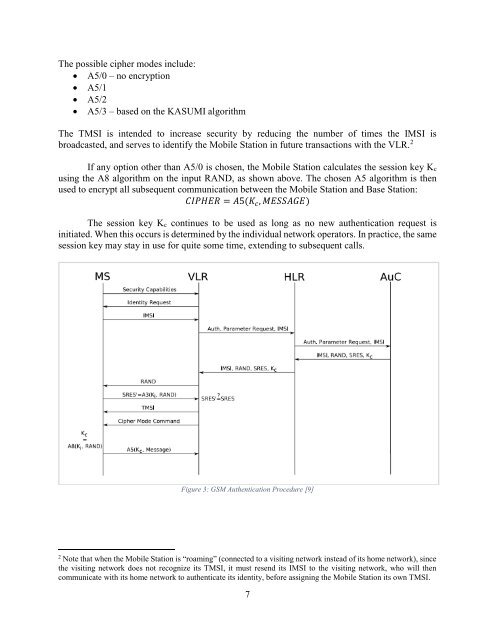
The TMSI is intended to increase security by reducing the number of times the <strong>IMSI</strong> is<br />
broadcasted, <strong>and</strong> serves to identify the <strong>Mobile</strong> Station in future transactions with the VLR. 2<br />
If any option other than A5/0 is chosen, the <strong>Mobile</strong> Station calculates the session key Kc<br />
using the A8 algorithm on the input RAND, as shown above. The chosen A5 algorithm is then<br />
used to encrypt all subsequent communication between the <strong>Mobile</strong> Station <strong>and</strong> Base Station:<br />
CIPHER = A5(K c , MESSAGE)<br />
The session key Kc continues to be used as long as no new authentication request is<br />
initiated. When this occurs is determined by the individual network operators. In practice, the same<br />
session key may stay in use for quite some time, extending to subsequent calls.<br />
Figure 3: GSM Authentication Procedure [9]<br />
2<br />
Note that when the <strong>Mobile</strong> Station is “roaming” (connected to a visiting network instead of its home network), since<br />
the visiting network does not recognize its TMSI, it must resend its <strong>IMSI</strong> to the visiting network, who will then<br />
communicate with its home network to authenticate its identity, before assigning the <strong>Mobile</strong> Station its own TMSI.<br />
7