IMSI Catchers and Mobile Security
EAS499Honors-IMSICatchersandMobileSecurity-V18F-1
EAS499Honors-IMSICatchersandMobileSecurity-V18F-1
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
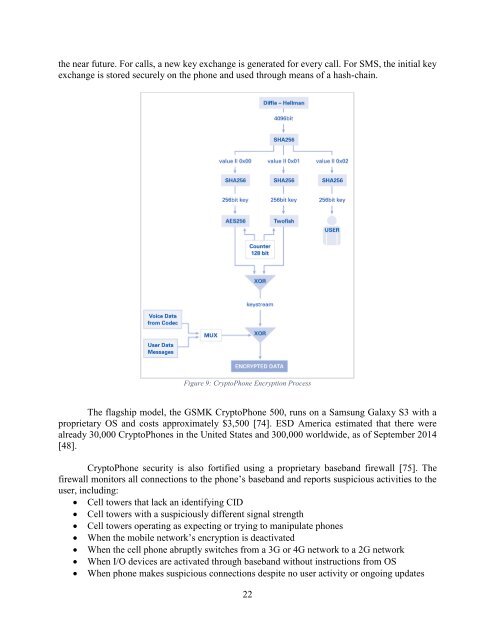
the near future. For calls, a new key exchange is generated for every call. For SMS, the initial key<br />
exchange is stored securely on the phone <strong>and</strong> used through means of a hash-chain.<br />
Figure 9: CryptoPhone Encryption Process<br />
The flagship model, the GSMK CryptoPhone 500, runs on a Samsung Galaxy S3 with a<br />
proprietary OS <strong>and</strong> costs approximately $3,500 [74]. ESD America estimated that there were<br />
already 30,000 CryptoPhones in the United States <strong>and</strong> 300,000 worldwide, as of September 2014<br />
[48].<br />
CryptoPhone security is also fortified using a proprietary baseb<strong>and</strong> firewall [75]. The<br />
firewall monitors all connections to the phone’s baseb<strong>and</strong> <strong>and</strong> reports suspicious activities to the<br />
user, including:<br />
Cell towers that lack an identifying CID<br />
Cell towers with a suspiciously different signal strength<br />
Cell towers operating as expecting or trying to manipulate phones<br />
When the mobile network’s encryption is deactivated<br />
When the cell phone abruptly switches from a 3G or 4G network to a 2G network<br />
When I/O devices are activated through baseb<strong>and</strong> without instructions from OS<br />
When phone makes suspicious connections despite no user activity or ongoing updates<br />
22