You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>DESTOVER</strong> “FORMBOUNDARY” BACKDOOR, NOV 2015<br />
This backdoor has many code overlaps with RandomDomain.B – for example, it uses CharSwap API obfuscation,<br />
and uses the same set of integer commands. It has evolved away from the use of faked SSL, which means whole<br />
segments of code have been removed, including most of the domain names used for the SSL handshake. Instead, it<br />
connects to the C&C server via regular HTTP on port 80 and initially posts a blob of random data disguised as a<br />
legitimate file. Any real content is sent encrypted afterwards, using one of the bytewise XOR encodings known from<br />
RandomDomain.<br />
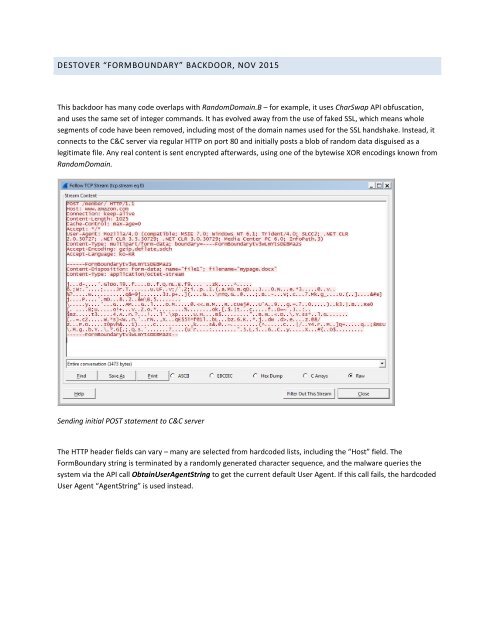
Sending initial POST statement to C&C server<br />
The HTTP header fields can vary – many are selected from hardcoded lists, including the “Host” field. The<br />
FormBoundary string is terminated by a randomly generated character sequence, and the malware queries the<br />
system via the API call ObtainUserAgentString to get the current default User Agent. If this call fails, the hardcoded<br />
User Agent “AgentString” is used instead.