You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>DESTOVER</strong> “VOLGMER2” BACKDOOR, JAN 2016<br />
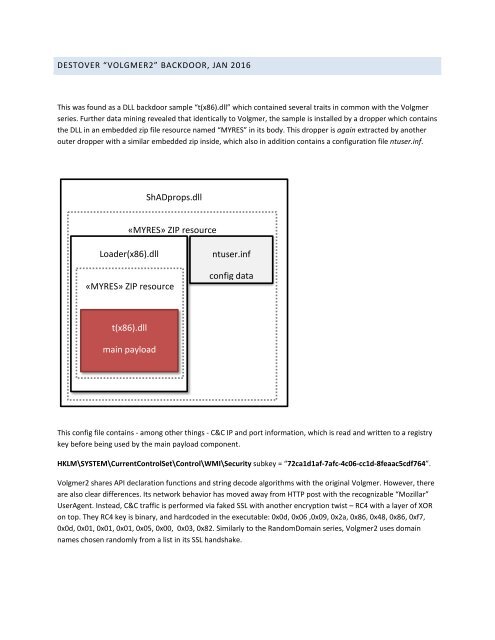
This was found as a DLL backdoor sample “t(x86).dll” which contained several traits in common with the Volgmer<br />
series. Further data mining revealed that identically to Volgmer, the sample is installed by a dropper which contains<br />
the DLL in an embedded zip file resource named “MYRES” in its body. This dropper is again extracted by another<br />
outer dropper with a similar embedded zip inside, which also in addition contains a configuration file ntuser.inf.<br />
ShADprops.dll<br />
«MYRES» ZIP resource<br />
Loader(x86).dll<br />
«MYRES» ZIP resource<br />
ntuser.inf<br />
config data<br />
t(x86).dll<br />
main payload<br />
This config file contains - among other things - C&C IP and port information, which is read and written to a registry<br />
key before being used by the main payload component.<br />
HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security subkey = “72ca1d1af-7afc-4c06-cc1d-8feaac5cdf764”.<br />
Volgmer2 shares API declaration functions and string decode algorithms with the original Volgmer. However, there<br />
are also clear differences. Its network behavior has moved away from HTTP post with the recognizable “Mozillar”<br />
UserAgent. Instead, C&C traffic is performed via faked SSL with another encryption twist – RC4 with a layer of XOR<br />
on top. They RC4 key is binary, and hardcoded in the executable: 0x0d, 0x06 ,0x09, 0x2a, 0x86, 0x48, 0x86, 0xf7,<br />
0x0d, 0x01, 0x01, 0x01, 0x05, 0x00, 0x03, 0x82. Similarly to the RandomDomain series, Volgmer2 uses domain<br />
names chosen randomly from a list in its SSL handshake.