Logical Analysis and Verification of Cryptographic Protocols - Loria
Logical Analysis and Verification of Cryptographic Protocols - Loria
Logical Analysis and Verification of Cryptographic Protocols - Loria
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
52 CHAPTER 2. PROTOCOL ANALYSIS USING CONSTRAINT SOLVING<br />
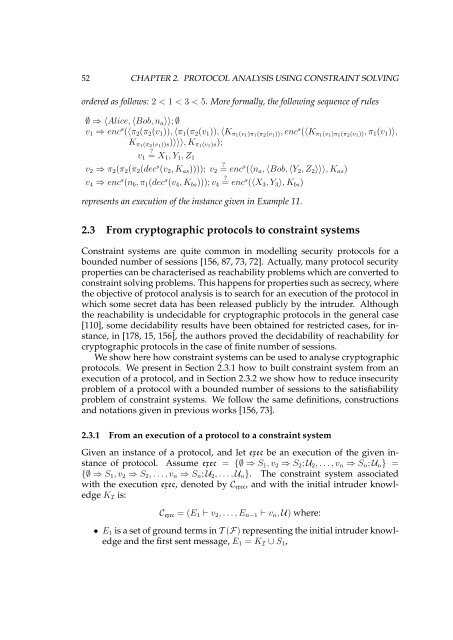
ordered as follows: 2 < 1 < 3 < 5. More formally, the following sequence <strong>of</strong> rules<br />
∅ ⇒ 〈Alice, 〈Bob, na〉〉; ∅<br />
v1 ⇒ encs (〈π2(π2(v1)), 〈π1(π2(v1)), 〈Kπ1(v1)π1(π2(v1)), encs (〈Kπ1(v1)π1(π2(v1)), π1(v1)〉,<br />
Kπ1(π2(v1))s)〉〉〉, Kπ1(v1)s);<br />
?<br />
v1 = X1, Y1, Z1<br />
v2 ⇒ π2(π2(π2(decs ?<br />
(v2, Kas)))); v2 = encs (〈na, 〈Bob, 〈Y2, Z2〉〉〉, Kas)<br />
v4 ⇒ encs (nb, π1(decs ?<br />
(v4, Kbs))); v4 = encs (〈X3, Y3〉, Kbs)<br />
represents an execution <strong>of</strong> the instance given in Example 11.<br />
2.3 From cryptographic protocols to constraint systems<br />
Constraint systems are quite common in modelling security protocols for a<br />
bounded number <strong>of</strong> sessions [156, 87, 73, 72]. Actually, many protocol security<br />
properties can be characterised as reachability problems which are converted to<br />
constraint solving problems. This happens for properties such as secrecy, where<br />
the objective <strong>of</strong> protocol analysis is to search for an execution <strong>of</strong> the protocol in<br />
which some secret data has been released publicly by the intruder. Although<br />
the reachability is undecidable for cryptographic protocols in the general case<br />
[110], some decidability results have been obtained for restricted cases, for instance,<br />
in [178, 15, 156], the authors proved the decidability <strong>of</strong> reachability for<br />
cryptographic protocols in the case <strong>of</strong> finite number <strong>of</strong> sessions.<br />
We show here how constraint systems can be used to analyse cryptographic<br />
protocols. We present in Section 2.3.1 how to built constraint system from an<br />
execution <strong>of</strong> a protocol, <strong>and</strong> in Section 2.3.2 we show how to reduce insecurity<br />
problem <strong>of</strong> a protocol with a bounded number <strong>of</strong> sessions to the satisfiability<br />
problem <strong>of</strong> constraint systems. We follow the same definitions, constructions<br />
<strong>and</strong> notations given in previous works [156, 73].<br />
2.3.1 From an execution <strong>of</strong> a protocol to a constraint system<br />
Given an instance <strong>of</strong> a protocol, <strong>and</strong> let exec be an execution <strong>of</strong> the given instance<br />
<strong>of</strong> protocol. Assume exec = {∅ ⇒ S1, v2 ⇒ S2; U2, . . . , vn ⇒ Sn; Un} =<br />
{∅ ⇒ S1, v2 ⇒ S2, . . . , vn ⇒ Sn; U2, . . . , Un}. The constraint system associated<br />
with the execution exec, denoted by Cexec, <strong>and</strong> with the initial intruder knowledge<br />
KI is:<br />
Cexec = (E1 ⊢ v2, . . . , En−1 ⊢ vn, U) where:<br />
• E1 is a set <strong>of</strong> ground terms in T (F) representing the initial intruder knowledge<br />
<strong>and</strong> the first sent message, E1 = KI ∪ S1,