- Page 1 and 2: Security Articles from Wikipedia PD
- Page 3 and 4: Article Licenses License 180
- Page 5 and 6: Advanced Encryption Standard 2 is a
- Page 7 and 8: Advanced Encryption Standard 4 The
- Page 9 and 10: Advanced Encryption Standard 6 Know
- Page 11 and 12: Advanced Encryption Standard 8 Test
- Page 13 and 14: Block cipher 10 Block cipher In cry
- Page 15 and 16: Block cipher 12 Block ciphers and o
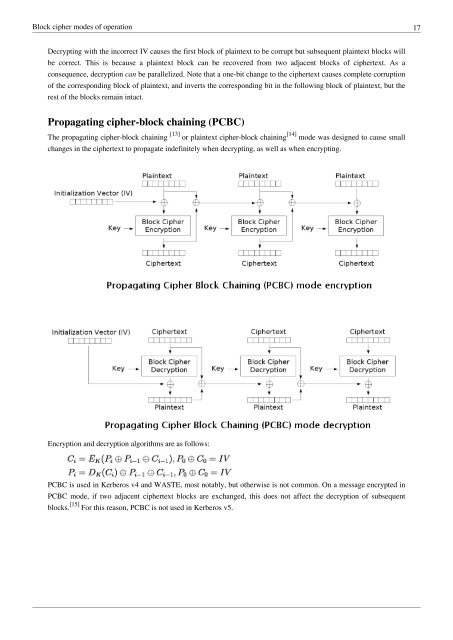
- Page 17 and 18: Block cipher modes of operation 14
- Page 19: Block cipher modes of operation 16
- Page 23 and 24: Block cipher modes of operation 20
- Page 25 and 26: Block cipher modes of operation 22
- Page 27 and 28: Certificate authority 24 Certificat
- Page 29 and 30: Certificate authority 26 Security T
- Page 31 and 32: CMAC 28 The CMAC tag generation pro
- Page 33 and 34: Cryptographic hash function 30 resi
- Page 35 and 36: Cryptographic hash function 32 func
- Page 37 and 38: Cryptographic hash function 34 Algo
- Page 39 and 40: DiffieHellman key exchange 36 The s
- Page 41 and 42: DiffieHellman key exchange 38 3. Bo
- Page 43 and 44: DiffieHellman key exchange 40 Upon
- Page 45 and 46: DiffieHellman key exchange 42 • C
- Page 47 and 48: Digital signature 44 every paramete
- Page 49 and 50: Digital signature 46 implemented. I
- Page 51 and 52: Digital signature 48 authority). Fo
- Page 53 and 54: Digital Signature Algorithm 50 Digi
- Page 55 and 56: Digital Signature Algorithm 52 Sens
- Page 57 and 58: HMAC 54 Implementation The followin
- Page 59 and 60: HMAC 56 External links • FIPS PUB
- Page 61 and 62: HTTP Secure 58 Browser integration
- Page 63 and 64: HTTP Secure 60 From an architectura
- Page 65 and 66: IPsec 62 IPsec Internet Protocol Se
- Page 67 and 68: IPsec 64 operates directly on top o
- Page 69 and 70: IPsec 66 Cryptographic algorithms C
- Page 71 and 72:
IPsec 68 External links • All IET
- Page 73 and 74:
Kerberos (protocol) 70 Kerberos (pr
- Page 75 and 76:
Kerberos (protocol) 72 Client Authe
- Page 77 and 78:
Kerberos (protocol) 74 External lin
- Page 79 and 80:
Message authentication code 76 Mess
- Page 81 and 82:
Message authentication code 78 Exte
- Page 83 and 84:
NeedhamSchroeder protocol 80 S resp
- Page 85 and 86:
Pretty Good Privacy 82 Pretty Good
- Page 87 and 88:
Pretty Good Privacy 84 Security qua
- Page 89 and 90:
Pretty Good Privacy 86 PGP 3 and fo
- Page 91 and 92:
Pretty Good Privacy 88 based on sec
- Page 93 and 94:
Public key certificate 90 Public ke
- Page 95 and 96:
Public key certificate 92 (b) ensur
- Page 97 and 98:
Public key certificate 94 Usefulnes
- Page 99 and 100:
Public key infrastructure 96 As tim
- Page 101 and 102:
Public key infrastructure 98 Extern
- Page 103 and 104:
Public-key cryptography 100 In cont
- Page 105 and 106:
Public-key cryptography 102 To achi
- Page 107 and 108:
Public-key cryptography 104 using t
- Page 109 and 110:
Public-key cryptography 106 Spreadi
- Page 111 and 112:
Public-key cryptography 108 Externa
- Page 113 and 114:
RSA (algorithm) 110 The RSA algorit
- Page 115 and 116:
RSA (algorithm) 112 A working examp
- Page 117 and 118:
RSA (algorithm) 114 Signing message
- Page 119 and 120:
RSA (algorithm) 116 Side-channel an
- Page 121 and 122:
RSA (algorithm) 118 • The PKCS #1
- Page 123 and 124:
S/MIME 120 administrative overhead
- Page 125 and 126:
Secure Electronic Transaction 122 T
- Page 127 and 128:
Secure Shell 124 Usage SSH is typic
- Page 129 and 130:
Secure Shell 126 • RFC 4462, Gene
- Page 131 and 132:
Secure Shell 128 ability to multipl
- Page 133 and 134:
Security service (telecommunication
- Page 135 and 136:
Security service (telecommunication
- Page 137 and 138:
SHA-1 134 SHA-1 SHA-1 General Desig
- Page 139 and 140:
SHA-1 136 Applications SHA-1 forms
- Page 141 and 142:
SHA-1 138 At the Rump Session of CR
- Page 143 and 144:
SHA-1 140 a = temp Add this chunk's
- Page 145 and 146:
SHA-1 142 • Xiaoyun Wang, Yiqun L
- Page 147 and 148:
Stream cipher 144 Types of stream c
- Page 149 and 150:
Stream cipher 146 Filter generator
- Page 151 and 152:
Stream cipher 148 SNOW Pre-2003 Ver
- Page 153 and 154:
Symmetric-key algorithm 150 Key gen
- Page 155 and 156:
Transport Layer Security 152 TLS 1.
- Page 157 and 158:
Transport Layer Security 154 • SS
- Page 159 and 160:
Transport Layer Security 156 • Fi
- Page 161 and 162:
Transport Layer Security 158 Length
- Page 163 and 164:
Transport Layer Security 160 layer
- Page 165 and 166:
Transport Layer Security 162 Suppor
- Page 167 and 168:
Transport Layer Security 164 • RF
- Page 169 and 170:
Transport Layer Security 166 Extern
- Page 171 and 172:
X.509 168 Extensions informing a sp
- Page 173 and 174:
X.509 170 00:d3:a4:50:6e:c8:ff:56:6
- Page 175 and 176:
X.509 172 Exploits • MD2-based ce
- Page 177 and 178:
X.509 174 External links • ITU-T
- Page 179 and 180:
Article Sources and Contributors 17
- Page 181 and 182:
Article Sources and Contributors 17
- Page 183:
License 180 License Creative Common