Security Articles from Wikipedia
Security Articles from Wikipedia
Security Articles from Wikipedia
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Digital signature 43<br />
Definition<br />
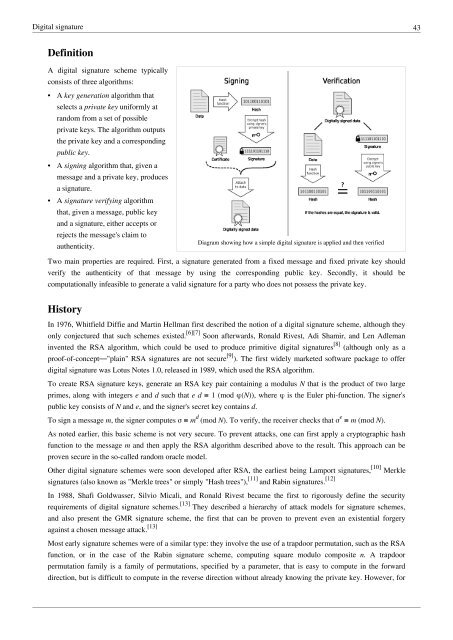
A digital signature scheme typically<br />
consists of three algorithms:<br />
• A key generation algorithm that<br />
selects a private key uniformly at<br />
random <strong>from</strong> a set of possible<br />
private keys. The algorithm outputs<br />
the private key and a corresponding<br />
public key.<br />
• A signing algorithm that, given a<br />
message and a private key, produces<br />
a signature.<br />
• A signature verifying algorithm<br />
that, given a message, public key<br />
and a signature, either accepts or<br />
rejects the message's claim to<br />
authenticity.<br />
Diagram showing how a simple digital signature is applied and then verified<br />
Two main properties are required. First, a signature generated <strong>from</strong> a fixed message and fixed private key should<br />
verify the authenticity of that message by using the corresponding public key. Secondly, it should be<br />
computationally infeasible to generate a valid signature for a party who does not possess the private key.<br />
History<br />
In 1976, Whitfield Diffie and Martin Hellman first described the notion of a digital signature scheme, although they<br />
only conjectured that such schemes existed. [6][7] Soon afterwards, Ronald Rivest, Adi Shamir, and Len Adleman<br />
invented the RSA algorithm, which could be used to produce primitive digital signatures [8] (although only as a<br />
proof-of-concept—"plain" RSA signatures are not secure [9] ). The first widely marketed software package to offer<br />
digital signature was Lotus Notes 1.0, released in 1989, which used the RSA algorithm.<br />
To create RSA signature keys, generate an RSA key pair containing a modulus N that is the product of two large<br />
primes, along with integers e and d such that e d ≡ 1 (mod φ(N)), where φ is the Euler phi-function. The signer's<br />
public key consists of N and e, and the signer's secret key contains d.<br />
To sign a message m, the signer computes σ ≡ m d (mod N). To verify, the receiver checks that σ e ≡ m (mod N).<br />
As noted earlier, this basic scheme is not very secure. To prevent attacks, one can first apply a cryptographic hash<br />
function to the message m and then apply the RSA algorithm described above to the result. This approach can be<br />
proven secure in the so-called random oracle model.<br />
Other digital signature schemes were soon developed after RSA, the earliest being Lamport signatures, [10] Merkle<br />
signatures (also known as "Merkle trees" or simply "Hash trees"), [11] and Rabin signatures. [12]<br />
In 1988, Shafi Goldwasser, Silvio Micali, and Ronald Rivest became the first to rigorously define the security<br />
requirements of digital signature schemes. [13] They described a hierarchy of attack models for signature schemes,<br />
and also present the GMR signature scheme, the first that can be proven to prevent even an existential forgery<br />
against a chosen message attack. [13]<br />
Most early signature schemes were of a similar type: they involve the use of a trapdoor permutation, such as the RSA<br />
function, or in the case of the Rabin signature scheme, computing square modulo composite n. A trapdoor<br />
permutation family is a family of permutations, specified by a parameter, that is easy to compute in the forward<br />
direction, but is difficult to compute in the reverse direction without already knowing the private key. However, for