Security Articles from Wikipedia
Security Articles from Wikipedia
Security Articles from Wikipedia
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Cryptographic hash function 29<br />
Cryptographic hash function<br />
A cryptographic hash function is a<br />
hash function that it can be defined as<br />
a deterministic procedure that takes an<br />
arbitrary block of data and returns a<br />
fixed-size bit string, the<br />
(cryptographic) hash value, such that<br />
an accidental or intentional change to<br />
the data will change the hash value.<br />
The data to be encoded is often called<br />
the "message," and the hash value is<br />
sometimes called the message digest<br />
or simply digest.<br />
The ideal cryptographic hash function<br />
has four main or significant properties:<br />
• it is easy (but not necessarily quick)<br />
to compute the hash value for any<br />
given message<br />
• it is infeasible to generate a message that has a given hash<br />
• it is infeasible to modify a message without changing the hash<br />
• it is infeasible to find two different messages with the same hash<br />
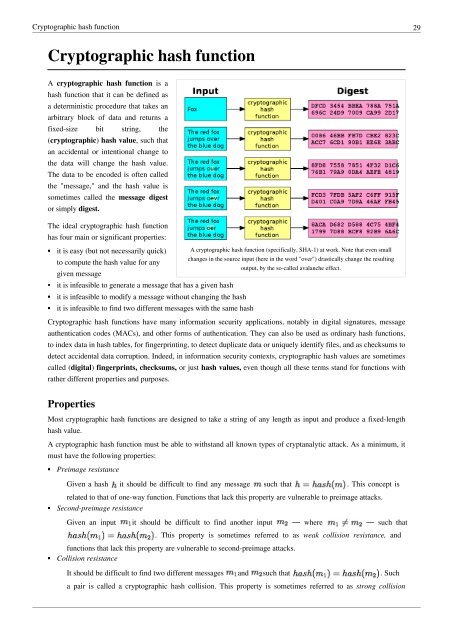
A cryptographic hash function (specifically, SHA-1) at work. Note that even small<br />
changes in the source input (here in the word "over") drastically change the resulting<br />
output, by the so-called avalanche effect.<br />
Cryptographic hash functions have many information security applications, notably in digital signatures, message<br />
authentication codes (MACs), and other forms of authentication. They can also be used as ordinary hash functions,<br />
to index data in hash tables, for fingerprinting, to detect duplicate data or uniquely identify files, and as checksums to<br />
detect accidental data corruption. Indeed, in information security contexts, cryptographic hash values are sometimes<br />
called (digital) fingerprints, checksums, or just hash values, even though all these terms stand for functions with<br />
rather different properties and purposes.<br />
Properties<br />
Most cryptographic hash functions are designed to take a string of any length as input and produce a fixed-length<br />
hash value.<br />
A cryptographic hash function must be able to withstand all known types of cryptanalytic attack. As a minimum, it<br />
must have the following properties:<br />
• Preimage resistance<br />
Given a hash it should be difficult to find any message such that . This concept is<br />
related to that of one-way function. Functions that lack this property are vulnerable to preimage attacks.<br />
• Second-preimage resistance<br />
Given an input it should be difficult to find another input — where — such that<br />
. This property is sometimes referred to as weak collision resistance, and<br />
functions that lack this property are vulnerable to second-preimage attacks.<br />
• Collision resistance<br />
It should be difficult to find two different messages and such that . Such<br />
a pair is called a cryptographic hash collision. This property is sometimes referred to as strong collision