Operating system verificationâAn overview
Operating system verificationâAn overview
Operating system verificationâAn overview
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
42 Gerwin Klein<br />
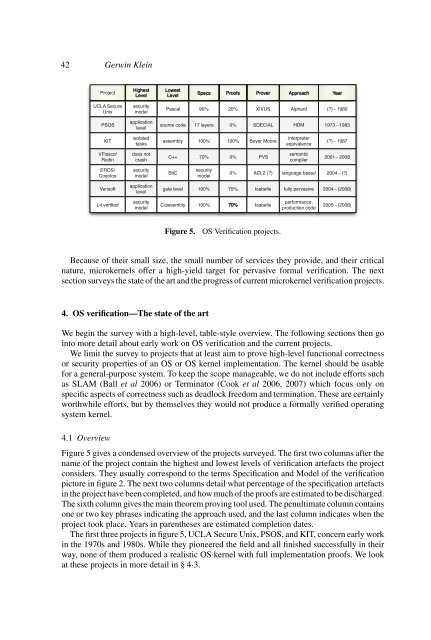
Figure 5.<br />
OS Verification projects.<br />
Because of their small size, the small number of services they provide, and their critical<br />
nature, microkernels offer a high-yield target for pervasive formal verification. The next<br />
section surveys the state of the art and the progress of current microkernel verification projects.<br />
4. OS verification—The state of the art<br />
We begin the survey with a high-level, table-style <strong>overview</strong>. The following sections then go<br />
into more detail about early work on OS verification and the current projects.<br />
We limit the survey to projects that at least aim to prove high-level functional correctness<br />
or security properties of an OS or OS kernel implementation. The kernel should be usable<br />
for a general-purpose <strong>system</strong>. To keep the scope manageable, we do not include efforts such<br />
as SLAM (Ball et al 2006) or Terminator (Cook et al 2006, 2007) which focus only on<br />
specific aspects of correctness such as deadlock freedom and termination. These are certainly<br />
worthwhile efforts, but by themselves they would not produce a formally verified operating<br />
<strong>system</strong> kernel.<br />
4.1 Overview<br />
Figure 5 gives a condensed <strong>overview</strong> of the projects surveyed. The first two columns after the<br />
name of the project contain the highest and lowest levels of verification artefacts the project<br />
considers. They usually correspond to the terms Specification and Model of the verification<br />
picture in figure 2. The next two columns detail what percentage of the specification artefacts<br />
in the project have been completed, and how much of the proofs are estimated to be discharged.<br />
The sixth column gives the main theorem proving tool used. The penultimate column contains<br />
one or two key phrases indicating the approach used, and the last column indicates when the<br />
project took place. Years in parentheses are estimated completion dates.<br />
The first three projects in figure 5, UCLA Secure Unix, PSOS, and KIT, concern early work<br />
in the 1970s and 1980s. While they pioneered the field and all finished successfully in their<br />
way, none of them produced a realistic OS kernel with full implementation proofs. We look<br />
at these projects in more detail in § 4·3.