Operating system verificationâAn overview
Operating system verificationâAn overview
Operating system verificationâAn overview
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>Operating</strong> <strong>system</strong> verification—An <strong>overview</strong> 53<br />
Applications<br />
SOS<br />
User Mode<br />
VAMOS<br />
CVM<br />
Kernel Mode<br />
VAMP<br />
Hardware<br />
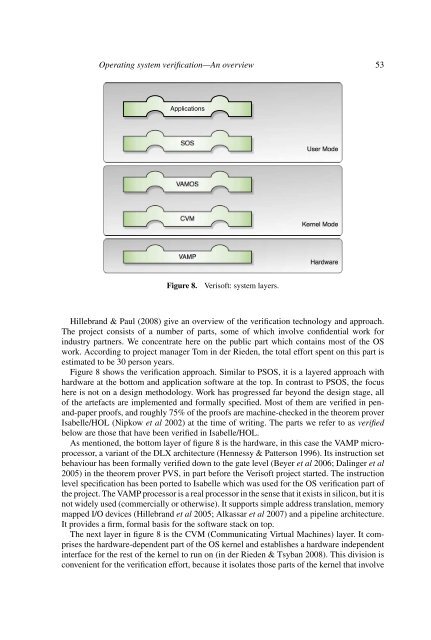
Figure 8.<br />
Verisoft: <strong>system</strong> layers.<br />
Hillebrand & Paul (2008) give an <strong>overview</strong> of the verification technology and approach.<br />
The project consists of a number of parts, some of which involve confidential work for<br />
industry partners. We concentrate here on the public part which contains most of the OS<br />
work. According to project manager Tom in der Rieden, the total effort spent on this part is<br />
estimated to be 30 person years.<br />
Figure 8 shows the verification approach. Similar to PSOS, it is a layered approach with<br />
hardware at the bottom and application software at the top. In contrast to PSOS, the focus<br />
here is not on a design methodology. Work has progressed far beyond the design stage, all<br />
of the artefacts are implemented and formally specified. Most of them are verified in penand-paper<br />
proofs, and roughly 75% of the proofs are machine-checked in the theorem prover<br />
Isabelle/HOL (Nipkow et al 2002) at the time of writing. The parts we refer to as verified<br />
below are those that have been verified in Isabelle/HOL.<br />
As mentioned, the bottom layer of figure 8 is the hardware, in this case the VAMP microprocessor,<br />
a variant of the DLX architecture (Hennessy & Patterson 1996). Its instruction set<br />
behaviour has been formally verified down to the gate level (Beyer et al 2006; Dalinger et al<br />
2005) in the theorem prover PVS, in part before the Verisoft project started. The instruction<br />
level specification has been ported to Isabelle which was used for the OS verification part of<br />
the project. The VAMP processor is a real processor in the sense that it exists in silicon, but it is<br />
not widely used (commercially or otherwise). It supports simple address translation, memory<br />
mapped I/O devices (Hillebrand et al 2005; Alkassar et al 2007) and a pipeline architecture.<br />
It provides a firm, formal basis for the software stack on top.<br />
The next layer in figure 8 is the CVM (Communicating Virtual Machines) layer. It comprises<br />
the hardware-dependent part of the OS kernel and establishes a hardware independent<br />
interface for the rest of the kernel to run on (in der Rieden & Tsyban 2008). This division is<br />
convenient for the verification effort, because it isolates those parts of the kernel that involve