Operating system verificationâAn overview
Operating system verificationâAn overview
Operating system verificationâAn overview
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>Operating</strong> <strong>system</strong> verification—An <strong>overview</strong> 29<br />
Common<br />
Criteria<br />
Requirements<br />
Functional<br />
Specification<br />
HLD<br />
LLD<br />
Implementation<br />
EAL 1<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
EAL 2<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
EAL 3<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
EAL<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
Informal<br />
EAL 5<br />
Formal Semiformal Semiformal Informal<br />
Informal<br />
EAL 6 Formal Semiformal Semiformal Semiformal Informal<br />
EAL 7<br />
Formal Formal Formal Semiformal Informal<br />
Verified Formal Formal Formal Formal Formal<br />
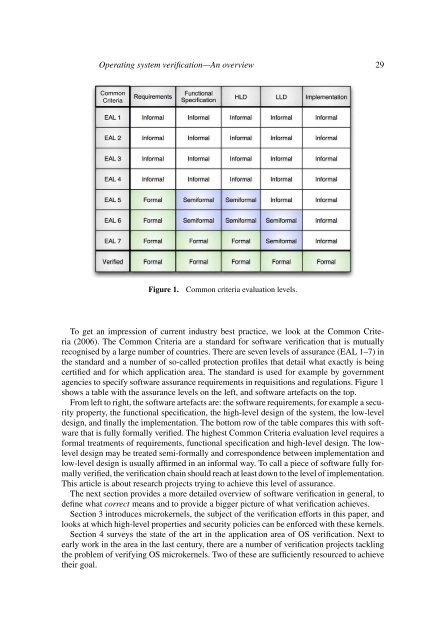
Figure 1.<br />
Common criteria evaluation levels.<br />
To get an impression of current industry best practice, we look at the Common Criteria<br />
(2006). The Common Criteria are a standard for software verification that is mutually<br />
recognised by a large number of countries. There are seven levels of assurance (EAL 1–7) in<br />
the standard and a number of so-called protection profiles that detail what exactly is being<br />
certified and for which application area. The standard is used for example by government<br />
agencies to specify software assurance requirements in requisitions and regulations. Figure 1<br />
shows a table with the assurance levels on the left, and software artefacts on the top.<br />
From left to right, the software artefacts are: the software requirements, for example a security<br />
property, the functional specification, the high-level design of the <strong>system</strong>, the low-level<br />
design, and finally the implementation. The bottom row of the table compares this with software<br />
that is fully formally verified. The highest Common Criteria evaluation level requires a<br />
formal treatments of requirements, functional specification and high-level design. The lowlevel<br />
design may be treated semi-formally and correspondence between implementation and<br />
low-level design is usually affirmed in an informal way. To call a piece of software fully formally<br />
verified, the verification chain should reach at least down to the level of implementation.<br />
This article is about research projects trying to achieve this level of assurance.<br />
The next section provides a more detailed <strong>overview</strong> of software verification in general, to<br />
define what correct means and to provide a bigger picture of what verification achieves.<br />
Section 3 introduces microkernels, the subject of the verification efforts in this paper, and<br />
looks at which high-level properties and security policies can be enforced with these kernels.<br />
Section 4 surveys the state of the art in the application area of OS verification. Next to<br />
early work in the area in the last century, there are a number of verification projects tackling<br />
the problem of verifying OS microkernels. Two of these are sufficiently resourced to achieve<br />
their goal.