vulcan-cryptanalysis
vulcan-cryptanalysis
vulcan-cryptanalysis
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
... k<br />
k 127 000<br />
7-bitvaddressvselects<br />
1vbitvofvcryptovariable<br />
z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1<br />
z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1 z -1<br />
k 137 k 136 k 135 k 134 k 133 k 132 k 131 k 130<br />
z -1<br />
plaintext<br />
in<br />
differential<br />
encoder<br />
ciphertext<br />
out<br />
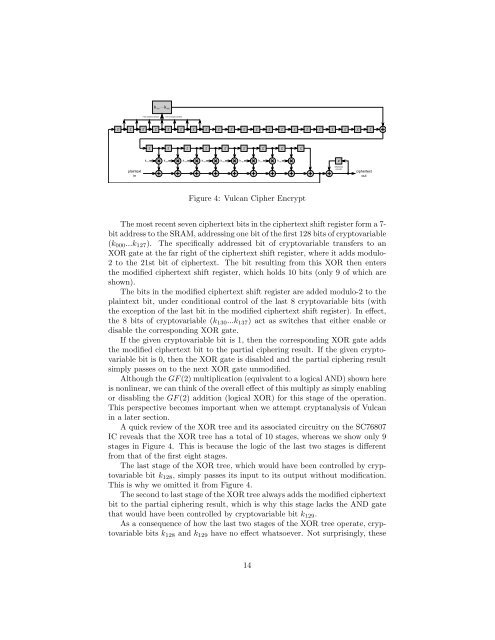
Figure 4: Vulcan Cipher Encrypt<br />
The most recent seven ciphertext bits in the ciphertext shift register form a 7-<br />
bit address to the SRAM, addressing one bit of the first 128 bits of cryptovariable<br />
(k 000 ...k 127 ). The specifically addressed bit of cryptovariable transfers to an<br />
XOR gate at the far right of the ciphertext shift register, where it adds modulo-<br />
2 to the 21st bit of ciphertext. The bit resulting from this XOR then enters<br />
the modified ciphertext shift register, which holds 10 bits (only 9 of which are<br />
shown).<br />
The bits in the modified ciphertext shift register are added modulo-2 to the<br />
plaintext bit, under conditional control of the last 8 cryptovariable bits (with<br />
the exception of the last bit in the modified ciphertext shift register). In effect,<br />
the 8 bits of cryptovariable (k 130 ...k 137 ) act as switches that either enable or<br />
disable the corresponding XOR gate.<br />
If the given cryptovariable bit is 1, then the corresponding XOR gate adds<br />
the modified ciphertext bit to the partial ciphering result. If the given cryptovariable<br />
bit is 0, then the XOR gate is disabled and the partial ciphering result<br />
simply passes on to the next XOR gate unmodified.<br />
Although the GF (2) multiplication (equivalent to a logical AND) shown here<br />
is nonlinear, we can think of the overall effect of this multiply as simply enabling<br />
or disabling the GF (2) addition (logical XOR) for this stage of the operation.<br />
This perspective becomes important when we attempt <strong>cryptanalysis</strong> of Vulcan<br />
in a later section.<br />
A quick review of the XOR tree and its associated circuitry on the SC76807<br />
IC reveals that the XOR tree has a total of 10 stages, whereas we show only 9<br />
stages in Figure 4. This is because the logic of the last two stages is different<br />
from that of the first eight stages.<br />
The last stage of the XOR tree, which would have been controlled by cryptovariable<br />
bit k 128 , simply passes its input to its output without modification.<br />
This is why we omitted it from Figure 4.<br />
The second to last stage of the XOR tree always adds the modified ciphertext<br />
bit to the partial ciphering result, which is why this stage lacks the AND gate<br />
that would have been controlled by cryptovariable bit k 129 .<br />
As a consequence of how the last two stages of the XOR tree operate, cryptovariable<br />
bits k 128 and k 129 have no effect whatsoever. Not surprisingly, these<br />
14