ericssonhistory.com
ericssonhistory.com
ericssonhistory.com
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
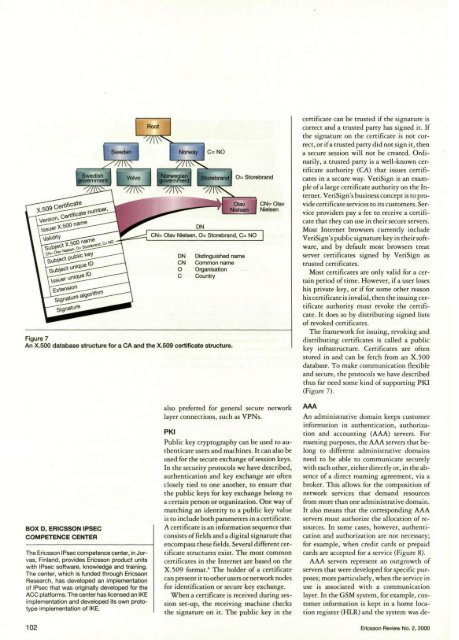
Figure 7An X.500 database structure for a CA and the X.509 certificate structure.certificate can be trusted if the signature iscorrect and a trusted party has signed it. Ifthe signature on the certificate is not correct,or if a trusted party did not sign it, thena secure session will not be created. Ordinarily,a trusted party is a well-known certificateauthority (CA) that issues certificatesin a secure way. VeriSign is an exampleof a large certificate authority on the Internet.VeriSign's business concept is to providecertificate services to its customers. Serviceproviders pay a fee to receive a certificatethat they can use in their secure servers.Most Internet browsers currently includeVeriSign's public signature key in their software,and by default most browsers treatserver certificates signed by VeriSign astrusted certificates.Most certificates are only valid for a certainperiod of time. However, if a user loseshis private key, or if for some other reasonhis certificate is invalid, then the issuing certificateauthority must revoke the certificate.It does so by distributing signed listsof revoked certificates.The framework for issuing, revoking anddistributing certificates is called a publickey infrastructure. Certificates are oftenstored in and can be fetch from an X.500database. To make <strong>com</strong>munication flexibleand secure, the protocols we have describedthus far need some kind of supporting PKI(Figure 7).BOX D, ERICSSON IPSECCOMPETENCE CENTERThe Ericsson IPsec <strong>com</strong>petence center, in Jorvas,Finland, provides Ericsson product unitswith IPsec software, knowledge and training.The center, which is funded through EricssonResearch, has developed an implementationof IPsec that was originally developed for theACC platforms. The center has licensed an IKEimplementation and developed its own prototypeimplementation of IKE.also preferred for general secure networklayer connections, such as VPNs.PKIPublic key cryptography can be used to authenticateusers and machines. It can also beused for the secure exchange of session keys.In the security protocols we have described,authentication and key exchange are oftenclosely tied to one another, to ensure thatthe public keys for key exchange belong toa certain person or organization. One way ofmatching an identity to a public key valueis to include both parameters in a certificate.A certificate is an information sequence thatconsists of fields and a digital signature thaten<strong>com</strong>pass these fields. Several different certificatestructures exist. The most <strong>com</strong>moncertificates in the Internet are based on theX.509 format. 6 The holder of a certificatecan present it to other users or network nodesfor identification or secure key exchange.When a certificate is received during sessionset-up, the receiving machine checksthe signature on it. The public key in theAAAAn administrative domain keeps customerinformation in authentication, authorizationand accounting (AAA) servers. Forroaming purposes, the AAA servers that belongto different administrative domainsneed to be able to <strong>com</strong>municate securelywith each other, either directly or, in the absenceof a direct roaming agreement, via abroker. This allows for the <strong>com</strong>position ofnetwork services that demand resourcesfrom more than one administrative domain.It also means that the corresponding AAAservers must authorize the allocation of resources.In some cases, however, authenticationand authorization are not necessary;for example, when credit cards or prepaidcards are accepted for a service (Figure 8).AAA servers represent an outgrowth ofservers that were developed for specific purposes;more particularly, when the service inuse is associated with a <strong>com</strong>municationlayer. In the GSM system, for example, customerinformation is kept in a home locationregister (HLR) and the system was de-102 Ericsson Review No. 2, 2000