Mission Operations Reference Model. Draft ... - CCSDS
Mission Operations Reference Model. Draft ... - CCSDS
Mission Operations Reference Model. Draft ... - CCSDS
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
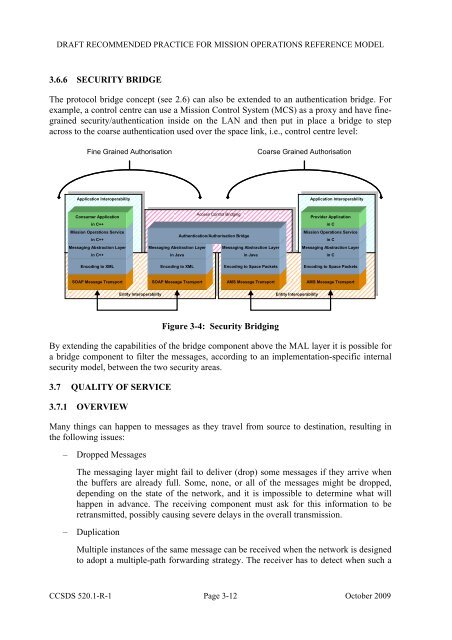
DRAFT RECOMMENDED PRACTICE FOR MISSION OPERATIONS REFERENCE MODEL3.6.6 SECURITY BRIDGEThe protocol bridge concept (see 2.6) can also be extended to an authentication bridge. Forexample, a control centre can use a <strong>Mission</strong> Control System (MCS) as a proxy and have finegrainedsecurity/authentication inside on the LAN and then put in place a bridge to stepacross to the coarse authentication used over the space link, i.e., control centre level:Fine Grained AuthorisationCoarse Grained AuthorisationApplication InteroperabilityApplication InteroperabilityApplication InteroperabilityApplication InteroperabilityConsumer Applicationin C++<strong>Mission</strong> <strong>Operations</strong> Servicein C++Messaging Abstraction Layerin C++Messaging Abstraction Layerin JavaAccess Control BridgingAccess Control BridgingAuthentication/Authorisation BridgeMessaging Abstraction Layerin JavaProvider Applicationin C<strong>Mission</strong> <strong>Operations</strong> Servicein CMessaging Abstraction Layerin CEncoding to XMLEncoding to XMLEncoding to Space PacketsEncoding to Space PacketsSOAP Message TransportSOAP Message TransportAMS Message TransportAMS Message TransportEntity InteroperabilityEntity InteroperabilityEntity InteroperabilityEntity InteroperabilityFigure 3-4: Security BridgingBy extending the capabilities of the bridge component above the MAL layer it is possible fora bridge component to filter the messages, according to an implementation-specific internalsecurity model, between the two security areas.3.7 QUALITY OF SERVICE3.7.1 OVERVIEWMany things can happen to messages as they travel from source to destination, resulting inthe following issues:– Dropped MessagesThe messaging layer might fail to deliver (drop) some messages if they arrive whenthe buffers are already full. Some, none, or all of the messages might be dropped,depending on the state of the network, and it is impossible to determine what willhappen in advance. The receiving component must ask for this information to beretransmitted, possibly causing severe delays in the overall transmission.– DuplicationMultiple instances of the same message can be received when the network is designedto adopt a multiple-path forwarding strategy. The receiver has to detect when such a<strong>CCSDS</strong> 520.1-R-1 Page 3-12 October 2009