Mission Operations Reference Model. Draft ... - CCSDS
Mission Operations Reference Model. Draft ... - CCSDS
Mission Operations Reference Model. Draft ... - CCSDS
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
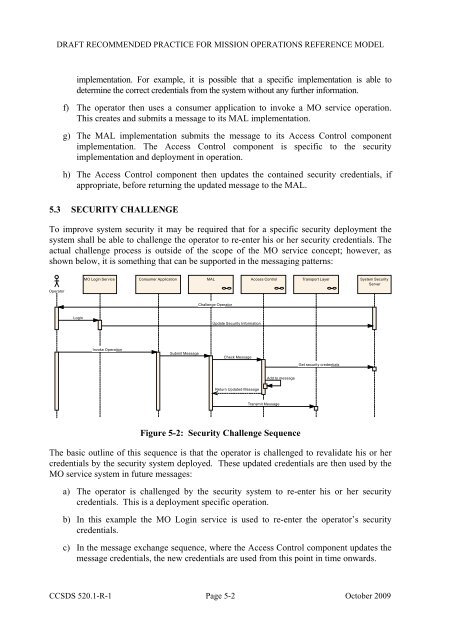
DRAFT RECOMMENDED PRACTICE FOR MISSION OPERATIONS REFERENCE MODELimplementation. For example, it is possible that a specific implementation is able todetermine the correct credentials from the system without any further information.f) The operator then uses a consumer application to invoke a MO service operation.This creates and submits a message to its MAL implementation.g) The MAL implementation submits the message to its Access Control componentimplementation. The Access Control component is specific to the securityimplementation and deployment in operation.h) The Access Control component then updates the contained security credentials, ifappropriate, before returning the updated message to the MAL.5.3 SECURITY CHALLENGETo improve system security it may be required that for a specific security deployment thesystem shall be able to challenge the operator to re-enter his or her security credentials. Theactual challenge process is outside of the scope of the MO service concept; however, asshown below, it is something that can be supported in the messaging patterns:OperatorMO Login Service Consumer ApplicationMAL Access Control Transport LayerSystem SecurityServerChallenge OperatorLoginUpdate Security InformationInvoke OperationSubmit MessageCheck MessageGet security credentialsAdd to messageReturn Updated MessageTransmit MessageFigure 5-2: Security Challenge SequenceThe basic outline of this sequence is that the operator is challenged to revalidate his or hercredentials by the security system deployed. These updated credentials are then used by theMO service system in future messages:a) The operator is challenged by the security system to re-enter his or her securitycredentials. This is a deployment specific operation.b) In this example the MO Login service is used to re-enter the operator’s securitycredentials.c) In the message exchange sequence, where the Access Control component updates themessage credentials, the new credentials are used from this point in time onwards.<strong>CCSDS</strong> 520.1-R-1 Page 5-2 October 2009