O Guia Definitivo do Yii 1.1
O Guia Definitivo do Yii 1.1
O Guia Definitivo do Yii 1.1
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
When authorization fails, i.e., the user is not allowed to perform the specified action, one of<br />
the following two scenarios may happen:<br />
If the user is not logged in and if the loginUrl property of the user component is configured<br />
to be the URL of the login page, the browser will be redirected to that page. Note that by<br />
default, loginUrl points to thesite/login page.<br />
Otherwise an HTTP exception will be displayed with error code 403.<br />
When configuring the loginUrl property, one can provide a relative or absolute URL. One<br />
can also provide an array which will be used to generate a URL by calling<br />
CWebApplication::createUrl. The first array element should specify the route to the login<br />
controller action, and the rest name-value pairs are GET parameters. For example,<br />
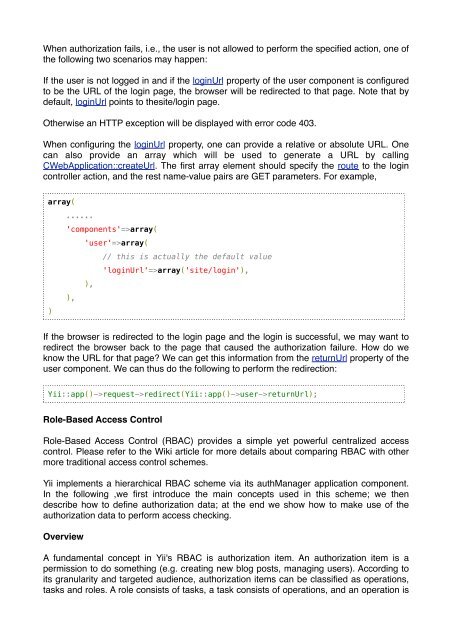
array(<br />
......<br />
'components'=>array(<br />
'user'=>array(<br />
// this is actually the default value<br />
'loginUrl'=>array('site/login'),<br />
),<br />
),<br />
)<br />
If the browser is redirected to the login page and the login is successful, we may want to<br />
redirect the browser back to the page that caused the authorization failure. How <strong>do</strong> we<br />
know the URL for that page? We can get this information from the returnUrl property of the<br />
user component. We can thus <strong>do</strong> the following to perform the redirection:<br />
<strong>Yii</strong>::app()->request->redirect(<strong>Yii</strong>::app()->user->returnUrl);<br />
Role-Based Access Control<br />
Role-Based Access Control (RBAC) provides a simple yet powerful centralized access<br />
control. Please refer to the Wiki article for more details about comparing RBAC with other<br />
more traditional access control schemes.<br />
<strong>Yii</strong> implements a hierarchical RBAC scheme via its authManager application component.<br />
In the following ,we first introduce the main concepts used in this scheme; we then<br />
describe how to define authorization data; at the end we show how to make use of the<br />
authorization data to perform access checking.<br />
Overview<br />
A fundamental concept in <strong>Yii</strong>'s RBAC is authorization item. An authorization item is a<br />
permission to <strong>do</strong> something (e.g. creating new blog posts, managing users). According to<br />
its granularity and targeted audience, authorization items can be classified as operations,<br />
tasks and roles. A role consists of tasks, a task consists of operations, and an operation is