Signal Analysis Research (SAR) Group - RNet - Ryerson University
Signal Analysis Research (SAR) Group - RNet - Ryerson University
Signal Analysis Research (SAR) Group - RNet - Ryerson University
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
ing a large number of cells in Hough-Radon space shifts<br />
the peak of the accumulator to the neighbor cells and consequently<br />
results in a wrong detection of the slope in TFD.<br />
Therefore, we see in Figure 3 that DPPT-based method outperforms<br />
HRT-based algorithm in most of the attack types<br />
with a total detection of 92% compared to 87%. Also, comparing<br />
the complexity order of HRT-based and DPPT-based<br />
techniques, we conclude that the DPPT-based method is<br />
more practical for real-time applications. Figure 4, shows<br />
the complexity order and running time based on Pentium<br />
IV, CPU 2.66GHz and 512MB of RAM. DPPT-based watermark<br />
extraction is about 55 times faster than HRT-based<br />
algorithm.<br />
As we observe in Figure 3, the detection result for the<br />
BCH coding and repetition codings have almost the same<br />
detection rates, but DPPT-based method offers better or in<br />
some cases equal results when compared to REP and BCH<br />
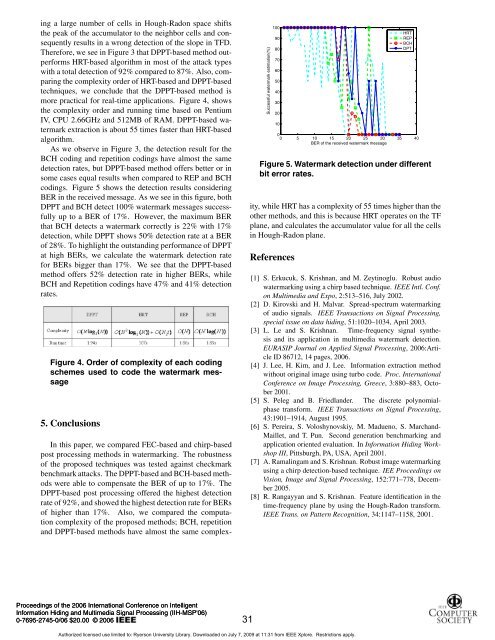
codings. Figure 5 shows the detection results considering<br />
BER in the received message. As we see in this figure, both<br />
DPPT and BCH detect 100% watermark messages successfully<br />
up to a BER of 17%. However, the maximum BER<br />
that BCH detects a watermark correctly is 22% with 17%<br />
detection, while DPPT shows 50% detection rate at a BER<br />
of 28%. To highlight the outstanding performance of DPPT<br />
at high BERs, we calculate the watermark detection rate<br />
for BERs bigger than 17%. We see that the DPPT-based<br />
method offers 52% detection rate in higher BERs, while<br />
BCH and Repetition codings have 47% and 41% detection<br />
rates.<br />
Figure 4. Order of complexity of each coding<br />
schemes used to code the watermark message<br />
5. Conclusions<br />
In this paper, we compared FEC-based and chirp-based<br />
post processing methods in watermarking. The robustness<br />
of the proposed techniques was tested against checkmark<br />
benchmark attacks. The DPPT-based and BCH-based methods<br />
were able to compensate the BER of up to 17%. The<br />
DPPT-based post processing offered the highest detection<br />
rate of 92%, and showed the highest detection rate for BERs<br />
of higher than 17%. Also, we compared the computation<br />
complexity of the proposed methods; BCH, repetition<br />
and DPPT-based methods have almost the same complex-<br />
Proceedings of the 2006 International Conference on Intelligent<br />
Information Hiding and Multimedia <strong>Signal</strong> Processing (IIH-MSP'06)<br />
0-7695-2745-0/06 $20.00 © 2006<br />
Successful watermark estimation(%)<br />
100<br />
90<br />
80<br />
70<br />
60<br />
50<br />
40<br />
30<br />
20<br />
10<br />
HRT<br />
REP<br />
BCH<br />
DPT<br />
0<br />
0 5 10 15 20 25 30 35 40<br />
BER of the received watermark message<br />
Figure 5. Watermark detection under different<br />
bit error rates.<br />
ity, while HRT has a complexity of 55 times higher than the<br />
other methods, and this is because HRT operates on the TF<br />
plane, and calculates the accumulator value for all the cells<br />
in Hough-Radon plane.<br />
References<br />
[1] S. Erkucuk, S. Krishnan, and M. Zeytinoglu. Robust audio<br />
watermarking using a chirp based technique. IEEE Intl. Conf.<br />
on Multimedia and Expo, 2:513–516, July 2002.<br />
[2] D. Kirovski and H. Malvar. Spread-spectrum watermarking<br />
of audio signals. IEEE Transactions on <strong>Signal</strong> Processing,<br />
special issue on data hiding, 51:1020–1034, April 2003.<br />
[3] L. Le and S. Krishnan. Time-frequency signal synthesis<br />
and its application in multimedia watermark detection.<br />
EURASIP Journal on Applied <strong>Signal</strong> Processing, 2006:Article<br />
ID 86712, 14 pages, 2006.<br />
[4] J. Lee, H. Kim, and J. Lee. Information extraction method<br />
without original image using turbo code. Proc. International<br />
Conference on Image Processing, Greece, 3:880–883, October<br />
2001.<br />
[5] S. Peleg and B. Friedlander. The discrete polynomialphase<br />
transform. IEEE Transactions on <strong>Signal</strong> Processing,<br />
43:1901–1914, August 1995.<br />
[6] S. Pereira, S. Voloshynovskiy, M. Madueno, S. Marchand-<br />
Maillet, and T. Pun. Second generation benchmarking and<br />
application oriented evaluation. In Information Hiding Workshop<br />
III, Pittsburgh, PA, USA, April 2001.<br />
[7] A. Ramalingam and S. Krishnan. Robust image watermarking<br />
using a chirp detection-based technique. IEE Proceedings on<br />
Vision, Image and <strong>Signal</strong> Processing, 152:771–778, December<br />
2005.<br />
[8] R. Rangayyan and S. Krishnan. Feature identification in the<br />
time-frequency plane by using the Hough-Radon transform.<br />
IEEE Trans. on Pattern Recognition, 34:1147–1158, 2001.<br />
Authorized licensed use limited to: <strong>Ryerson</strong> <strong>University</strong> Library. Downloaded on July 7, 2009 at 11:31 from IEEE Xplore. Restrictions apply.<br />
31