Legal Disclaimer
Hacking-For-Beginners-a-beginners-guide-for-learning-ethical-hacking
Hacking-For-Beginners-a-beginners-guide-for-learning-ethical-hacking
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Hacking For Beginners – Manthan Desai 2010<br />
someone did manage to decrypt a transaction, that would not mean that they would have found the server's secret key; if<br />
they wanted to decrypt another transaction, they'd need to spend as much time and effort on the second transaction as<br />
they did on the first. Of course, they would have first have to have figured out some method of intercepting the<br />
transaction data in the first place, which is in itself extremely difficult. It would be significantly easier to tap your phone,<br />
or to intercept your mail to acquire your credit card number than to somehow intercept and decode Internet Data.<br />
Servers and browsers do encryption ranging from a 40-bit secret key to a 128-bit secret key, that is to say '2 to the 40th<br />
power' or '2 to the 128th power'. Many people have heard that 40-bit is insecure and that you need 128-bit to keep your<br />
credit card info safe. They feel that using a 40-bit key is insecure because it's vulnerable to a "brute force" attack<br />
(basically trying each of the 2^40 possible keys until you find the one that decrypts the message). This was in fact<br />
demonstrated when a French researcher used a network of fast workstations to crack a 40-bit encrypted message in a<br />
little over a week. Of course, even this 'vulnerability' is not really applicable to applications like an online credit card<br />
transaction, since the transaction is completed in a few moments. If a network of fast computers takes a week to crack a<br />
40-bit key, you'd be completed your transaction and long gone before the hacker even got started.<br />
Of course, using a 128-bit key eliminates any problem at all because there are 2^128 instead of 2^40 possible keys. Using<br />
the same method (a networked of fast workstations) to crack a message encrypted with such a key would take<br />
significantly longer than the age of the universe using conventional technology. Remember that 128-bit is not just 'three<br />
times' as powerful as 40-bit encryption. 2^128 is 'two times two, times two, times two...' with 128 two's. That is two,<br />
doubled on itself 128 times. 2^40 is already a HUGE number, about a trillion (that's a million, million!). Therefore 2^128<br />
is that number (a trillion), doubled over and over on itself another 88 times. Again, it would take significantly longer than<br />
the age of the universe to crack a 128-bit key.<br />
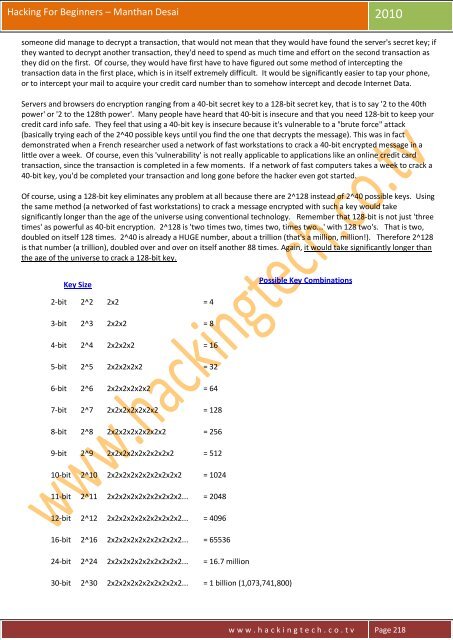
Key Size<br />
Possible Key Combinations<br />
2-bit 2^2 2x2 = 4<br />
3-bit 2^3 2x2x2 = 8<br />
4-bit 2^4 2x2x2x2 = 16<br />
5-bit 2^5 2x2x2x2x2 = 32<br />
6-bit 2^6 2x2x2x2x2x2 = 64<br />
7-bit 2^7 2x2x2x2x2x2x2 = 128<br />
8-bit 2^8 2x2x2x2x2x2x2x2 = 256<br />
9-bit 2^9 2x2x2x2x2x2x2x2x2 = 512<br />
10-bit 2^10 2x2x2x2x2x2x2x2x2x2 = 1024<br />
11-bit 2^11 2x2x2x2x2x2x2x2x2x2... = 2048<br />
12-bit 2^12 2x2x2x2x2x2x2x2x2x2... = 4096<br />
16-bit 2^16 2x2x2x2x2x2x2x2x2x2... = 65536<br />
24-bit 2^24 2x2x2x2x2x2x2x2x2x2... = 16.7 million<br />
30-bit 2^30 2x2x2x2x2x2x2x2x2x2... = 1 billion (1,073,741,800)<br />
w w w . h a c k i n g t e c h . c o . t v Page 218