CCNP TSHOOT 6.0 - Cisco Learning Home
CCNP TSHOOT 6.0 - Cisco Learning Home
CCNP TSHOOT 6.0 - Cisco Learning Home
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>CCNP</strong>v6 <strong>TSHOOT</strong><br />
Sample Troubleshooting Output<br />
The following commands and outputs are provided as samples from the devices in this lab.<br />
<strong>Cisco</strong> IOS Stateful Firewall-related Commands<br />
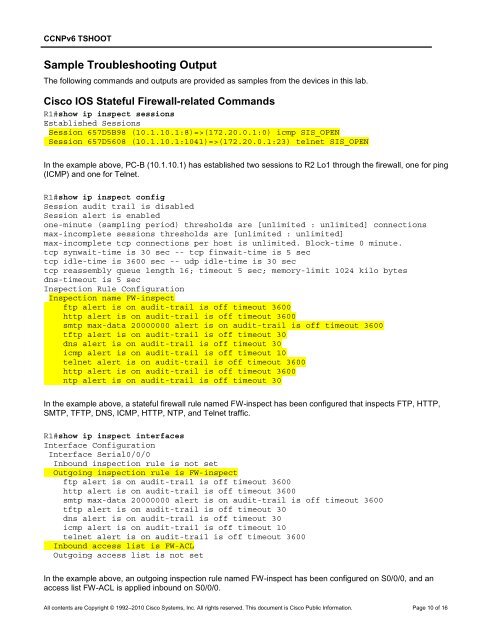
R1#show ip inspect sessions<br />
Established Sessions<br />
Session 657D5B98 (10.1.10.1:8)=>(172.20.0.1:0) icmp SIS_OPEN<br />
Session 657D5608 (10.1.10.1:1041)=>(172.20.0.1:23) telnet SIS_OPEN<br />
In the example above, PC-B (10.1.10.1) has established two sessions to R2 Lo1 through the firewall, one for ping<br />
(ICMP) and one for Telnet.<br />
R1#show ip inspect config<br />
Session audit trail is disabled<br />
Session alert is enabled<br />
one-minute (sampling period) thresholds are [unlimited : unlimited] connections<br />
max-incomplete sessions thresholds are [unlimited : unlimited]<br />
max-incomplete tcp connections per host is unlimited. Block-time 0 minute.<br />
tcp synwait-time is 30 sec -- tcp finwait-time is 5 sec<br />
tcp idle-time is 3600 sec -- udp idle-time is 30 sec<br />
tcp reassembly queue length 16; timeout 5 sec; memory-limit 1024 kilo bytes<br />
dns-timeout is 5 sec<br />
Inspection Rule Configuration<br />
Inspection name FW-inspect<br />
ftp alert is on audit-trail is off timeout 3600<br />
http alert is on audit-trail is off timeout 3600<br />
smtp max-data 20000000 alert is on audit-trail is off timeout 3600<br />
tftp alert is on audit-trail is off timeout 30<br />
dns alert is on audit-trail is off timeout 30<br />
icmp alert is on audit-trail is off timeout 10<br />
telnet alert is on audit-trail is off timeout 3600<br />
http alert is on audit-trail is off timeout 3600<br />
ntp alert is on audit-trail is off timeout 30<br />
In the example above, a stateful firewall rule named FW-inspect has been configured that inspects FTP, HTTP,<br />
SMTP, TFTP, DNS, ICMP, HTTP, NTP, and Telnet traffic.<br />
R1#show ip inspect interfaces<br />
Interface Configuration<br />
Interface Serial0/0/0<br />
Inbound inspection rule is not set<br />
Outgoing inspection rule is FW-inspect<br />
ftp alert is on audit-trail is off timeout 3600<br />
http alert is on audit-trail is off timeout 3600<br />
smtp max-data 20000000 alert is on audit-trail is off timeout 3600<br />
tftp alert is on audit-trail is off timeout 30<br />
dns alert is on audit-trail is off timeout 30<br />
icmp alert is on audit-trail is off timeout 10<br />
telnet alert is on audit-trail is off timeout 3600<br />
Inbound access list is FW-ACL<br />
Outgoing access list is not set<br />
In the example above, an outgoing inspection rule named FW-inspect has been configured on S0/0/0, and an<br />
access list FW-ACL is applied inbound on S0/0/0.<br />
All contents are Copyright © 1992–2010 <strong>Cisco</strong> Systems, Inc. All rights reserved. This document is <strong>Cisco</strong> Public Information. Page 10 of 16