Network Coding and Wireless Physical-layer ... - Jacobs University
Network Coding and Wireless Physical-layer ... - Jacobs University
Network Coding and Wireless Physical-layer ... - Jacobs University
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
6 Chapter 2: Introduction to Digital Communication Systems <strong>and</strong> <strong>Network</strong>s<br />
Binary<br />
Source<br />
Source<br />
Encoder<br />
Channel<br />
Encoder<br />
Digital<br />
Modulator<br />
Channel<br />
Binary<br />
Sink<br />
Source<br />
Decoder<br />
Channel<br />
Decoder<br />
Digital<br />
Demodulator<br />
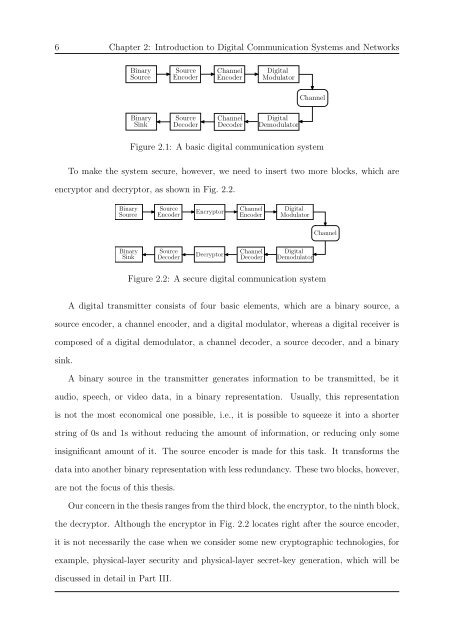
Figure 2.1: A basic digital communication system<br />
To make the system secure, however, we need to insert two more blocks, which are<br />
encryptor <strong>and</strong> decryptor, as shown in Fig. 2.2.<br />
Binary<br />
Source<br />
Source<br />
Encoder<br />
Encryptor<br />
Channel<br />
Encoder<br />
Digital<br />
Modulator<br />
Channel<br />
Binary<br />
Sink<br />
Source<br />
Decoder<br />
Decryptor<br />
Channel<br />
Decoder<br />
Digital<br />
Demodulator<br />
Figure 2.2: A secure digital communication system<br />
A digital transmitter consists of four basic elements, which are a binary source, a<br />
source encoder, a channel encoder, <strong>and</strong> a digital modulator, whereas a digital receiver is<br />
composed of a digital demodulator, a channel decoder, a source decoder, <strong>and</strong> a binary<br />
sink.<br />
A binary source in the transmitter generates information to be transmitted, be it<br />
audio, speech, or video data, in a binary representation.<br />
Usually, this representation<br />
is not the most economical one possible, i.e., it is possible to squeeze it into a shorter<br />
string of 0s <strong>and</strong> 1s without reducing the amount of information, or reducing only some<br />
insignificant amount of it. The source encoder is made for this task. It transforms the<br />
data into another binary representation with less redundancy. These two blocks, however,<br />
are not the focus of this thesis.<br />
Our concern in the thesis ranges from the third block, the encryptor, to the ninth block,<br />
the decryptor. Although the encryptor in Fig. 2.2 locates right after the source encoder,<br />
it is not necessarily the case when we consider some new cryptographic technologies, for<br />
example, physical-<strong>layer</strong> security <strong>and</strong> physical-<strong>layer</strong> secret-key generation, which will be<br />
discussed in detail in Part III.