Raytheon Company Public Key Infrastructure (PKI) Certificate Policy
Raytheon Company Public Key Infrastructure (PKI) Certificate Policy
Raytheon Company Public Key Infrastructure (PKI) Certificate Policy
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
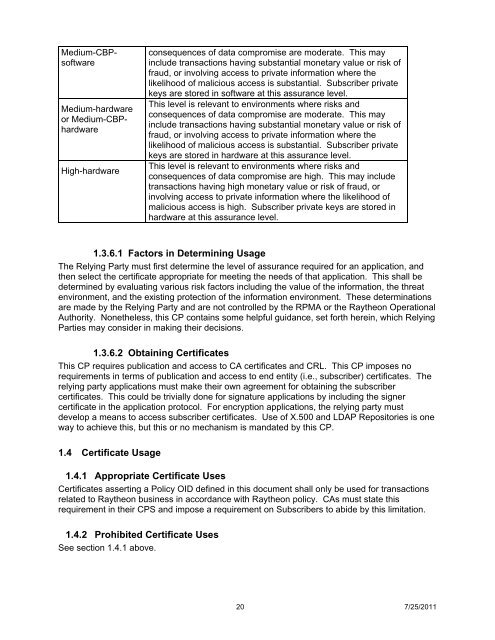
Medium-CBPsoftware<br />
Medium-hardware<br />
or Medium-CBPhardware<br />
High-hardware<br />
consequences of data compromise are moderate. This may<br />
include transactions having substantial monetary value or risk of<br />
fraud, or involving access to private information where the<br />
likelihood of malicious access is substantial. Subscriber private<br />
keys are stored in software at this assurance level.<br />
This level is relevant to environments where risks and<br />
consequences of data compromise are moderate. This may<br />
include transactions having substantial monetary value or risk of<br />
fraud, or involving access to private information where the<br />
likelihood of malicious access is substantial. Subscriber private<br />
keys are stored in hardware at this assurance level.<br />
This level is relevant to environments where risks and<br />
consequences of data compromise are high. This may include<br />
transactions having high monetary value or risk of fraud, or<br />
involving access to private information where the likelihood of<br />
malicious access is high. Subscriber private keys are stored in<br />
hardware at this assurance level.<br />
1.3.6.1 Factors in Determining Usage<br />
The Relying Party must first determine the level of assurance required for an application, and<br />
then select the certificate appropriate for meeting the needs of that application. This shall be<br />
determined by evaluating various risk factors including the value of the information, the threat<br />
environment, and the existing protection of the information environment. These determinations<br />
are made by the Relying Party and are not controlled by the RPMA or the <strong>Raytheon</strong> Operational<br />
Authority. Nonetheless, this CP contains some helpful guidance, set forth herein, which Relying<br />
Parties may consider in making their decisions.<br />
1.3.6.2 Obtaining <strong>Certificate</strong>s<br />
This CP requires publication and access to CA certificates and CRL. This CP imposes no<br />
requirements in terms of publication and access to end entity (i.e., subscriber) certificates. The<br />
relying party applications must make their own agreement for obtaining the subscriber<br />
certificates. This could be trivially done for signature applications by including the signer<br />
certificate in the application protocol. For encryption applications, the relying party must<br />
develop a means to access subscriber certificates. Use of X.500 and LDAP Repositories is one<br />
way to achieve this, but this or no mechanism is mandated by this CP.<br />
1.4 <strong>Certificate</strong> Usage<br />
1.4.1 Appropriate <strong>Certificate</strong> Uses<br />
<strong>Certificate</strong>s asserting a <strong>Policy</strong> OID defined in this document shall only be used for transactions<br />
related to <strong>Raytheon</strong> business in accordance with <strong>Raytheon</strong> policy. CAs must state this<br />
requirement in their CPS and impose a requirement on Subscribers to abide by this limitation.<br />
1.4.2 Prohibited <strong>Certificate</strong> Uses<br />
See section 1.4.1 above.<br />
20 7/25/2011