Raytheon Company Public Key Infrastructure (PKI) Certificate Policy
Raytheon Company Public Key Infrastructure (PKI) Certificate Policy
Raytheon Company Public Key Infrastructure (PKI) Certificate Policy
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
It is acceptable for the system to over-write audit logs after they have been backed up and<br />
archived.<br />
5.4.5 Audit Log Backup Procedures<br />
Audit logs and audit summaries shall be backed up at least once every 30 days. A copy of the<br />
audit log shall be sent off-site in accordance with the CPS every 30 days.<br />
5.4.6 Audit Collection System (internal vs. external)<br />
The audit log collection system may or may not be external to the CA, CSA, or RA. Audit<br />
processes shall be invoked at system startup, and cease only at system shutdown. Should it<br />
become apparent that an automated audit system has failed, and the integrity of the system or<br />
confidentiality of the information protected by the system is at risk, then the CA shall determine<br />
whether to suspend CA operation until the problem is remedied.<br />
5.4.7 Notification to Event-Causing Subject<br />
This CP imposes no requirement to provide notice that an event was audited to the individual,<br />
organization, device, or application that caused the event.<br />
5.4.8 Vulnerability Assessments<br />
The CA, system administrator, and other operating personnel shall be watchful for attempts to<br />
violate the integrity of the certificate management system, including the equipment, physical<br />
location, and personnel. The security audit data shall be reviewed by the audit administrator for<br />
events such as repeated failed actions, requests for privileged information, attempted access of<br />
system files, and unauthenticated responses. Security auditors shall check for continuity of the<br />
security audit data. The audit administrator shall document the summary results of the period<br />
review of the audit logs.<br />
5.5 Records Archival<br />
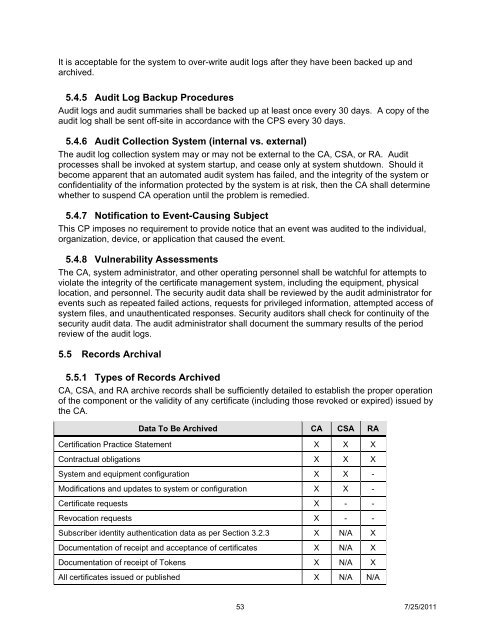
5.5.1 Types of Records Archived<br />
CA, CSA, and RA archive records shall be sufficiently detailed to establish the proper operation<br />
of the component or the validity of any certificate (including those revoked or expired) issued by<br />
the CA.<br />
Data To Be Archived CA CSA RA<br />
Certification Practice Statement X X X<br />
Contractual obligations X X X<br />
System and equipment configuration X X -<br />
Modifications and updates to system or configuration X X -<br />
<strong>Certificate</strong> requests X - -<br />
Revocation requests X - -<br />
Subscriber identity authentication data as per Section 3.2.3 X N/A X<br />
Documentation of receipt and acceptance of certificates X N/A X<br />
Documentation of receipt of Tokens X N/A X<br />
All certificates issued or published X N/A N/A<br />
53 7/25/2011