Intrusion Management Installation and User Guide - G4S Technology
Intrusion Management Installation and User Guide - G4S Technology
Intrusion Management Installation and User Guide - G4S Technology
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
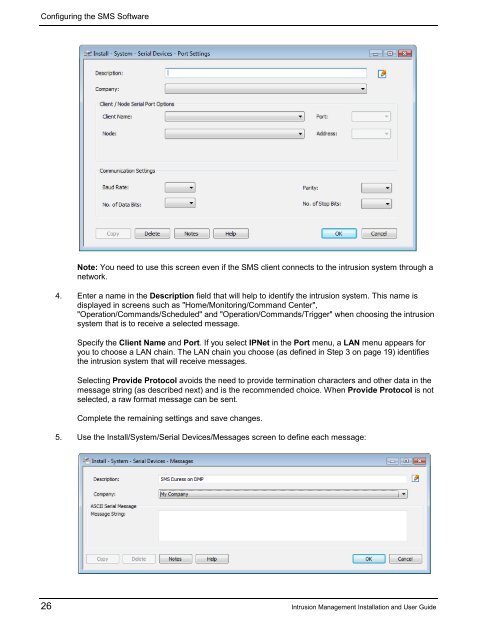
Configuring the SMS SoftwareNote: You need to use this screen even if the SMS client connects to the intrusion system through anetwork.4. Enter a name in the Description field that will help to identify the intrusion system. This name isdisplayed in screens such as "Home/Monitoring/Comm<strong>and</strong> Center","Operation/Comm<strong>and</strong>s/Scheduled" <strong>and</strong> "Operation/Comm<strong>and</strong>s/Trigger" when choosing the intrusionsystem that is to receive a selected message.Specify the Client Name <strong>and</strong> Port. If you select IPNet in the Port menu, a LAN menu appears foryou to choose a LAN chain. The LAN chain you choose (as defined in Step 3 on page 19) identifiesthe intrusion system that will receive messages.Selecting Provide Protocol avoids the need to provide termination characters <strong>and</strong> other data in themessage string (as described next) <strong>and</strong> is the recommended choice. When Provide Protocol is notselected, a raw format message can be sent.Complete the remaining settings <strong>and</strong> save changes.5. Use the Install/System/Serial Devices/Messages screen to define each message:26 <strong>Intrusion</strong> <strong>Management</strong> <strong>Installation</strong> <strong>and</strong> <strong>User</strong> <strong>Guide</strong>