Banking and Finance Sector-Specific Plan - U.S. Department of ...
Banking and Finance Sector-Specific Plan - U.S. Department of ...
Banking and Finance Sector-Specific Plan - U.S. Department of ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
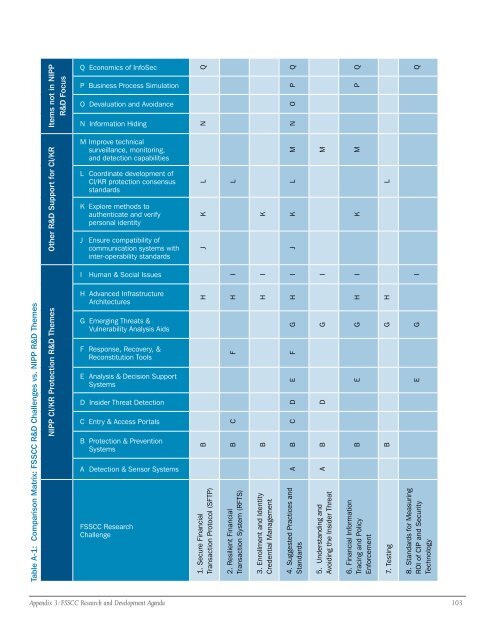
SCC R&D Challenges vs. NIPP R&D Themes<br />
able A-1: Comparison Matrix: FS<br />
T<br />
NIPP CI/KR Protection R&D Themes Other R&D Support for CI/KR Items not in NIPP<br />
R&D Focus<br />
Q Economics <strong>of</strong> InfoSec<br />
P Business Process Simulation<br />
O Devaluation <strong>and</strong> Avoidance<br />
N Information Hiding<br />
M Improve technical<br />
surveillance, monitoring,<br />
<strong>and</strong> detection capabilities<br />
L Coordinate development <strong>of</strong><br />
CI/KR protection consensus<br />
st<strong>and</strong>ards<br />
K Explore methods to<br />
authenticate <strong>and</strong> verify<br />
personal identity<br />
J Ensure compatibility <strong>of</strong><br />
communication systems with<br />
inter-operability st<strong>and</strong>ards<br />
I Human & Social Issues<br />
H Advanced Infrastructure<br />
Architectures<br />
G Emerging Threats &<br />
Vulnerability Analysis Aids<br />
F Response, Recovery, &<br />
Reconstitution Tools<br />
E Analysis & Decision Support<br />
Systems<br />
D Insider Threat Detection<br />
C Entry & Access Portals<br />
B Protection & Prevention<br />
Systems<br />
A Detection & Sensor Systems<br />
FSSCC Research<br />
Challenge<br />
B H J K L N Q<br />
1. Secure Financial<br />
Transaction Protocol (SFTP)<br />
B C F H I L<br />
2. Resilient Financial<br />
Transaction System (RFTS)<br />
Appendix : FSSCC Research <strong>and</strong> Development Agenda 0<br />
B H I K<br />
3. Enrollment <strong>and</strong> Identity<br />
Credential Management<br />
A B C D E F G H I J K L M N O P Q<br />
4. Suggested Practices <strong>and</strong><br />
St<strong>and</strong>ards<br />
A B D G I M<br />
5. Underst<strong>and</strong>ing <strong>and</strong><br />
Avoiding the Insider Threat<br />
B E G H I K M P Q<br />
6. Financial Information<br />
Tracing <strong>and</strong> Policy<br />
Enforcement<br />
7. Testing B G H L<br />
E G I Q<br />
8. St<strong>and</strong>ards for Measuring<br />
ROI <strong>of</strong> CIP <strong>and</strong> Security<br />
Technology