GM 139 HIBRIDNI RAD
GM Business, vanredno izdanje, Hibridni rad
GM Business, vanredno izdanje, Hibridni rad
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
When working outside the enterprise firewall,<br />
users are more vulnerable to threats such as<br />
REMOTE WORK AND BREACH &<br />
ATTACK VECTORS<br />
The top cyber attack vectors reported by professionals who saw an<br />
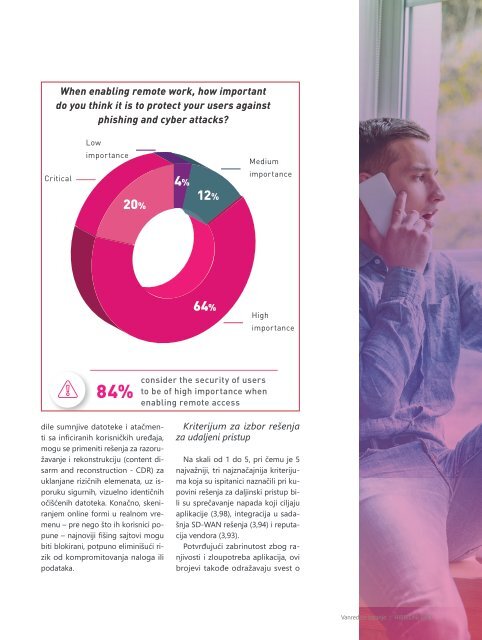
When enabling remote work, how important<br />
Key to preventing user-targeted<br />
increase in cyber attacks following Covid-19 are data exfiltration and<br />
do you think it is to protect your users against<br />
attacks are up-to-the minute<br />
leakage (55%), phishing emails (51%) and account takeover (44%).<br />
phishing and cyber attacks?<br />
threat intelligence and advanced<br />
These figures speak to the need to implement data loss prevention (DLP)<br />
Low<br />
sandboxing solutions that check<br />
for internet and cloud access by remote users, so that the same level of<br />
importance<br />
each link accessed and each file<br />
data protection is deployed within and outside the office. Medium<br />
importance downloaded, to block threats<br />
Critical<br />
Intrusion Prevention Systems (IPS) 4% and real-time anti-phishing engines<br />
before they populate on users’<br />
are critical to preventing phishing attacks 12% and account takeover, ensuring<br />
20%<br />
devices. To prevent suspicious<br />
that all clicked links are inspected and that corporate credentials are not<br />
files and attachment from<br />
reused in non-work accounts.<br />
infecting users’ devices, content<br />
If answered large or small increase in cyber attacks:<br />
Where do you see an increase in attacks and attack attempts?<br />
64%<br />
55% 51% 44% 36% 35%<br />
phishing sites, malware downloads and botnetlittle<br />
too late. As part of the SASE framework,<br />
Secure Web Gateways (SWGs) deliver secure<br />
internet access for remote users.<br />
High<br />
importance<br />
20%<br />
disarm and reconstruction (CDR)<br />
solutions can be deployed to<br />
remove risky elements while<br />
delivering safe, visually identical<br />
sanitized files. Finally, by scanning<br />
online forms in real time—before<br />
users complete them—the very<br />
latest phishing sites can be<br />
consider the security of users<br />
blocked, completely eliminating<br />
84%<br />
to be of high importance when Applicationtargeted<br />
the risk of account or data<br />
enabling remote access<br />
Ransomware<br />
Malware<br />
Account<br />
Phishing<br />
downloads<br />
attacks compromise.<br />
dile Data sumnjive datoteke i atačmenti<br />
sa<br />
takeoverKriterijum za izbor rešenja<br />
emails<br />
exfiltration,<br />
inficiranih korisničkih uređaja, za udaljeni pristup<br />
mo gu se pri me ni ti re še nja za raz o ružavanje<br />
i rekonstrukciju (content di<br />
leakage<br />
REMOTE<br />
Na skali<br />
AND<br />
od<br />
HYBRID<br />
1 do<br />
WORK<br />
5, pri<br />
SECURITY<br />
čemu je 5<br />
REPORT<br />
sarm and re con struc tion - CDR) za najvažniji, tri najznačajnija kriterijuma<br />
uklanjane rizičnih elemenata, uz isporuku<br />
koja su ispitanici naznačili pri ku<br />
sigurnih, vizuelno identičnih po vi ni re še nja za da ljin ski pri stup bili<br />
očišćenih datoteka. Konačno, skenira<br />
su sprečavanje napada koji ciljaju<br />
njem on li ne for mi u re al nom vremenu<br />
aplikacije (3,98), integracija u sadapune<br />
– pre nego što ih korisnici po<br />
šnja SD-WAN rešenja (3,94) i reputa<br />
– najnoviji fišing sajtovi mogu Top Attack cija vendora Vectors (3,93).<br />
biti blokirani, potpuno eliminišući rizik<br />
Potvrđujući zabrinutost zbog ra<br />
od kom pro mi to va nja na lo ga ili nji vo sti i zlo u po tre ba apli ka ci ja, ovi<br />
po da ta ka.<br />
brojevi takođe odražavaju svest o<br />
16<br />
Account takeover Phishing Data Leakage<br />
I<br />
REMOTE AND HYBRID WORK SECURITY REPORT<br />
Vanredno izdanje :: <strong>HIBRIDNI</strong> <strong>RAD</strong><br />
9