Click to download Ethernet Basics manual - Grant Industrial Controls
Click to download Ethernet Basics manual - Grant Industrial Controls
Click to download Ethernet Basics manual - Grant Industrial Controls
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Ethernet</strong> 33<br />
A switch that support LLDP can carry out <strong>to</strong>pology detection via other participants that also<br />
support LLDP.<br />
Advantages:<br />
• Improved detection of network errors<br />
• Tool for replacing modules<br />
• Better network configuration and network management<br />
LDDP information is used within engineering <strong>to</strong>ols <strong>to</strong> visualise a network <strong>to</strong>pology in a graphic<br />
manner.<br />
2.9.2 IEEE 802.1x<br />
IEEE 802.1x is a security standard for authentication on each individual port of a switch.<br />
Authentication occurs even before the user is given access <strong>to</strong> the network. The recognition<br />
of an authorised user therefore occurs at Layer 2 of the OSI model. This can all be done,<br />
regardless of the hardware used, both wirelessly and with wires.<br />
IEEE 802.1x uses a pro<strong>to</strong>col <strong>to</strong> exchange information with a device/user that sends a request<br />
for access <strong>to</strong> a port. The messages contain a user name and a password. The switch does not<br />
perform the identification itself but forwards the request <strong>to</strong> a RADIUS authentication server<br />
on the network. The server processes the request and gives feedback <strong>to</strong> the switch, which<br />
then opens the port for the user.<br />
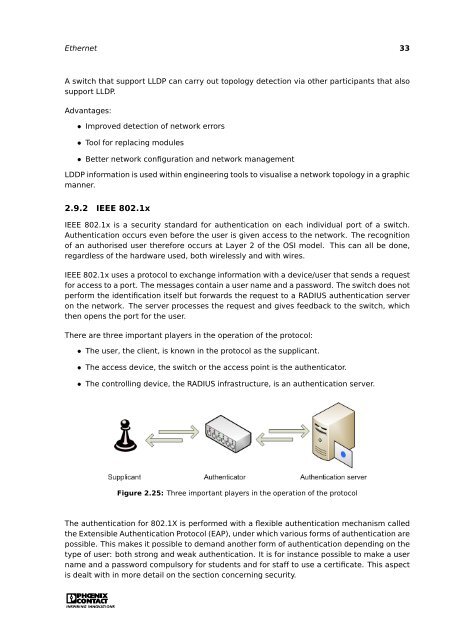
There are three important players in the operation of the pro<strong>to</strong>col:<br />
• The user, the client, is known in the pro<strong>to</strong>col as the supplicant.<br />
• The access device, the switch or the access point is the authentica<strong>to</strong>r.<br />
• The controlling device, the RADIUS infrastructure, is an authentication server.<br />
Figure 2.25: Three important players in the operation of the pro<strong>to</strong>col<br />
The authentication for 802.1X is performed with a flexible authentication mechanism called<br />
the Extensible Authentication Pro<strong>to</strong>col (EAP), under which various forms of authentication are<br />
possible. This makes it possible <strong>to</strong> demand another form of authentication depending on the<br />
type of user: both strong and weak authentication. It is for instance possible <strong>to</strong> make a user<br />
name and a password compulsory for students and for staff <strong>to</strong> use a certificate. This aspect<br />
is dealt with in more detail on the section concerning security.