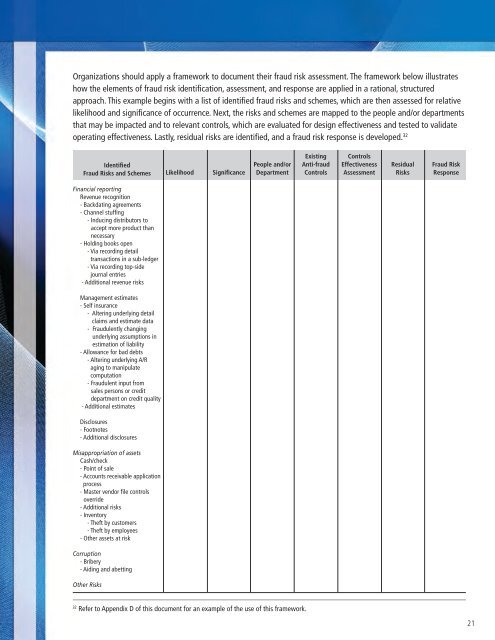
Organizations should apply a framework to document their <strong>fraud</strong> risk assessment. The framework below illustrateshow the elements of <strong>fraud</strong> risk identification, assessment, and response are applied in a rational, structuredapproach. This example begins with a list of identified <strong>fraud</strong> risks and schemes, which are then assessed for relativelikelihood and significance of occurrence. Next, the risks and schemes are mapped to the people and/or departmentsthat may be impacted and to relevant controls, which are evaluated for design effectiveness and tested to validateoperating effectiveness. Lastly, residual risks are identified, and a <strong>fraud</strong> risk response is developed. 32IdentifiedFraud Risks and SchemesLikelihoodSignificancePeople and/orDepartmentExistingAnti-<strong>fraud</strong>ControlsControlsEffectivenessAssessmentResidualRisksFraud RiskResponseFinancial reportingRevenue recognition- Backdating agreements- Channel stuffing- Inducing distributors toaccept more product thannecessary- Holding books open- Via recording detailtransactions in a sub-ledger- Via recording top-sidejournal entries- Additional revenue risksManagement estimates- Self insurance- Altering underlying detailclaims and estimate data- Fraudulently changingunderlying assumptions inestimation of liability- Allowance for bad debts- Altering underlying A/Raging to manipulatecomputation- Fraudulent input fromsales persons or creditdepartment on credit quality- Additional estimatesDisclosures- Footnotes- Additional disclosuresMisappropriation of assetsCash/<strong>check</strong>- Point of sale- Accounts receivable applicationprocess- Master vendor file controlsoverride- Additional risks- Inventory- Theft by customers- Theft by employees- Other assets at riskCorr<strong>up</strong>tion- Bribery- Aiding and abettingOther Risks32Refer to Appendix D of this document for an example of the use of this framework.21
The Risk Assessment TeamA good risk assessment requires input from various sources. Before conducting a risk assessment, managementshould identify a risk assessment team. This team should include individuals from throughout the organizationwith different knowledge, skills, and perspectives and should include a combination of internal and externalresources such as:• Accounting/finance personnel, who are familiar with the financial reporting process and internal controls.• Nonfinancial business unit and operations personnel, to leverage their knowledge of day-to-day operations,customer and vendor interactions, and general awareness of issues within the industry.• Risk management personnel, to ensure that the <strong>fraud</strong> risk assessment process integrates with theorganization’s ERM program.• Legal and compliance personnel, as the <strong>fraud</strong> risk assessment will identify risks that give rise to potentialcriminal, civil, and regulatory liability if the <strong>fraud</strong> or misconduct were to occur.• Internal audit personnel, who will be familiar with the organization’s internal controls and monitoringfunctions. In addition, internal auditors will be integral in developing and executing responses to significantrisks that cannot be mitigated practically by preventive and detective controls.• If expertise is not available internally, external consultants with expertise in applicable standards, key riskindicators, anti-<strong>fraud</strong> methodology, control activities, and detection procedures.Management, including senior management, business unit leaders, and significant process owners (e.g., accounting,sales, procurement, and operations) should participate in the assessment, as they are ultimately accountable for theeffectiveness of the organization’s <strong>fraud</strong> risk management efforts.Fraud Risk IdentificationOnce assembled, the risk assessment team should go through a brainstorming activity to identify the organization’s<strong>fraud</strong> risks. Effective brainstorming involves preparation in advance of the meeting, a leader to set the agendaand facilitate the session, and openness to ideas regarding potential risks and controls 33 . Brainstorming enablesdiscussions of the incentives, pressures, and opportunities to commit <strong>fraud</strong>; risks of management override ofcontrols; and the population of <strong>fraud</strong> risks relevant to the organization. 34 Other risks, such as regulatory and legalmisconduct and reputation risk, as well as the impact of IT on <strong>fraud</strong> risks also should be considered in the <strong>fraud</strong> riskidentification process.The organization’s <strong>fraud</strong> risk identification information should be shared with the board or audit committee andcomments should be solicited. The board also should assess the implications of its own processes with respect to itscontribution to <strong>fraud</strong> risk, including incentive pressures.33Sources of information about good brainstorming practices include (a) Mark S. Beasley and Gregory Jenkins, “A Primer for BrainstormingFraud Risks,” Journal of Accountancy, December 2003, and (b) Michael J. Ramos, “Brainstorming Prior to the Audit,” in Fraud Detection in aGAAS Audit: Revised Edition, Chapter 2: “Considering Fraud in a Financial Statement Audit.”34Refer to Appendix E: Fraud Risk Exposures of this document for a list of potential <strong>fraud</strong> risk which could be used in brainstorming.22
- Page 1 and 2: ACFE FRAUD PREVENTIONCHECK-UP
- Page 3 and 4: ACFE FRAUD PREVENTIONCHECK-UPThe Be
- Page 5 and 6: ACFE FRAUD PREVENTIONCHECK-UPACFE F
- Page 7 and 8: ACFE FRAUD PREVENTIONCHECK-UPACFE F
- Page 9 and 10: ACFE FRAUD PREVENTIONCHECK-UPACFE F
- Page 11 and 12: ACFE FRAUD PREVENTIONCHECK-UPACFE F
- Page 13 and 14: Sponsored by:The Institute of Inter
- Page 15 and 16: Team Members:Toby J.F. Bishop, CPA,
- Page 17 and 18: Managing the Business Risk of Fraud
- Page 19 and 20: establish their own fraud risk mana
- Page 21 and 22: Fraud risk identification may inclu
- Page 23 and 24: Thus, to properly address fraud ris
- Page 25 and 26: The board also has the responsibili
- Page 27 and 28: • Implementing adequate internal
- Page 29 and 30: Fraud Risk Management Program Compo
- Page 31 and 32: ecently been hired in the purchasin
- Page 33: Organizations can identify and asse
- Page 37 and 38: This also involves understanding th
- Page 39 and 40: - Invoices for goods not received o
- Page 41 and 42: Other RisksRegulatory and Legal Mis
- Page 43 and 44: SECTION 3: FRAUD PREVENTIONPrincipl
- Page 45 and 46: An organization’s HR group is oft
- Page 47 and 48: SECTION 4: FRAUD DETECTIONPrinciple
- Page 49 and 50: Process ControlsProcess controls sp
- Page 51 and 52: keep such information confidential.
- Page 53 and 54: will vary depending on the nature,
- Page 55 and 56: Conducting the InvestigationPlannin
- Page 57 and 58: • Extended investigation — Cond
- Page 59 and 60: Fraud ControlsDeloitte Forensic Cen
- Page 61 and 62: APPENDIX B: SAMPLE FRAMEWORK FOR A
- Page 63 and 64: APPENDIX C: SAMPLE FRAUD POLICY 41N
- Page 65 and 66: CONFIDENTIALITYThe ______________ U
- Page 67 and 68: Sample Fraud Policy Decision Matrix
- Page 69 and 70: Identified Fraud Risksand Schemes (
- Page 71 and 72: 2) Misappropriation of:a) Tangible
- Page 73 and 74: ) Embezzlement(1) False accounting
- Page 75 and 76: Fraud Prevention Area, Factor, or C
- Page 77 and 78: Fraud Prevention Area, Factor, or C
- Page 79 and 80: Fraud Prevention Area, Factor, or C
- Page 81 and 82: Fraud Prevention Area, Factor, or C
- Page 83 and 84: O-Organization / PersonnelO1-Leader
- Page 85 and 86:
O4.3 Enhance Operational Skills & C
- Page 87 and 88:
PR-Prevent, Protect & PreparePR1-Ge
- Page 89 and 90:
E-Periodic EvaluationE1-Evaluation
- Page 91 and 92:
I2-CommunicationI2.1 Develop Commun
- Page 93 and 94:
CriminologyFraud Prevention Program
- Page 95 and 96:
CriminologyFraud Prevention Program
- Page 97 and 98:
CriminologyFraud Prevention Program
- Page 99 and 100:
CriminologyFraud Prevention Program
- Page 101 and 102:
CriminologyFraud Prevention Program
- Page 103 and 104:
CriminologyFraud Prevention Program
- Page 105 and 106:
CriminologyFraud Prevention Program
- Page 107 and 108:
CriminologyFraud Prevention Program
- Page 109 and 110:
CriminologyFraud Prevention Program
- Page 111 and 112:
CriminologyFraud Prevention Program
- Page 113 and 114:
CriminologyFraud Prevention Program
- Page 115 and 116:
CriminologyFraud Prevention Program
- Page 117 and 118:
Sample Fraud PolicyAssociation of C
- Page 119 and 120:
Sample Fraud PolicyCONFIDENTIALITYT
- Page 121 and 122:
Sample Fraud PolicyFraud Policy Dec
- Page 123 and 124:
Fraud’s Worst Enemyhttp://www.fra
- Page 125 and 126:
ACFE Insights - ACFE Insightshttp:/
- Page 127:
ACFE Insights - ACFE Insightshttp:/