- Page 1:
International Technical Support Org
- Page 4 and 5:
Take Note! Before using this inform
- Page 6 and 7:
iv DataHub Implementation and Conne
- Page 8 and 9:
vi DataHub Implementation and Conne
- Page 10 and 11:
viii DataHub Implementation and Con
- Page 12 and 13:
x DataHub Implementation and Connec
- Page 14 and 15:
xii DataHub Implementation and Conn
- Page 16 and 17:
xiv DataHub Implementation and Conn
- Page 18 and 19:
xvi DataHub Implementation and Conn
- Page 20 and 21:
How to Read This Document xviii Dat
- Page 22 and 23:
xx DataHub Implementation and Conne
- Page 24 and 25:
xxii DataHub Implementation and Con
- Page 26 and 27:
DB2/2 Documentation DATABASE 2 OS/2
- Page 28 and 29:
xxvi DataHub Implementation and Con
- Page 30 and 31:
xxviii DataHub Implementation and C
- Page 32 and 33:
DataHub in Information Warehouse Fr
- Page 34 and 35:
1.1.1 Platform Feature 1.1.2 Tools
- Page 36 and 37:
1.2 DataHub Data Flows: Overview Be
- Page 38 and 39:
1.2.2 Utilities • AS4SQL statemen
- Page 40 and 41:
1.2.3 Manage Authorizations 10 Data
- Page 42 and 43:
1.2.5 Copy Data 12 DataHub Implemen
- Page 44 and 45:
• Target host The target host is
- Page 46 and 47:
Figure 9. Copy Data to an OS/2 Targ
- Page 48 and 49:
18 DataHub Implementation and Conne
- Page 50 and 51:
2.2 Sample Scenarios Let′s see ho
- Page 52 and 53:
2.2.2 Scenario 2: Central Managemen
- Page 54 and 55:
2.2.3 Scenario 3: Distributed Manag
- Page 56 and 57:
2.3 Factors Affecting Implementatio
- Page 58 and 59:
Managed Hosts • Install and confi
- Page 60 and 61:
• Physical resources − Requeste
- Page 62 and 63:
32 DataHub Implementation and Conne
- Page 64 and 65:
34 DataHub Implementation and Conne
- Page 66 and 67:
3.2.3 RDS Parameters RDB Name Like
- Page 68 and 69:
3.3 The ITSC Network 38 DataHub Imp
- Page 70 and 71:
3.4 MVS Definitions 3.4.1 SNA Defin
- Page 72 and 73:
42 DataHub Implementation and Conne
- Page 74 and 75:
44 DataHub Implementation and Conne
- Page 76 and 77:
VBUILD TYPE=APPL *-----------------
- Page 78 and 79:
48 DataHub Implementation and Conne
- Page 80 and 81:
50 DataHub Implementation and Conne
- Page 82 and 83:
3.5.2 DRDA Definitions 52 DataHub I
- Page 84 and 85:
SQL/DS Database Machine (AS) A CMS
- Page 86 and 87:
AVS Machine Definition In Figure 35
- Page 88 and 89:
Communication Directory Definition
- Page 90 and 91:
3.6 AS/400 Definitions 3. Enter the
- Page 92 and 93:
62 DataHub Implementation and Conne
- Page 94 and 95:
64 DataHub Implementation and Conne
- Page 96 and 97:
Other classes of service can be cre
- Page 98 and 99:
3.6.3 Testing DRDA Connections 68 D
- Page 100 and 101:
tools conversation. It could also b
- Page 102 and 103:
72 DataHub Implementation and Conne
- Page 104 and 105:
74 DataHub Implementation and Conne
- Page 106 and 107:
3. Click on Configure.... The Confi
- Page 108 and 109:
Manager/2 folder. For the Extended
- Page 110 and 111:
You are then back to the Communicat
- Page 112 and 113:
Figure 55. CM/2: Connections List W
- Page 114 and 115:
Figure 58. CM/2: Change Partner LUs
- Page 116 and 117:
3.7.5 DRDA Definitions Figure 60. C
- Page 118 and 119:
Communications Manager and OS/2 Dat
- Page 120 and 121:
Node Directory Number of entries in
- Page 122 and 123:
Figure 66 on page 92 shows you all
- Page 124 and 125:
94 DataHub Implementation and Conne
- Page 126 and 127:
Database Connection Services (DCS)
- Page 128 and 129:
3.7.7 Testing DRDA and RDS Connecti
- Page 130 and 131:
100 DataHub Implementation and Conn
- Page 132 and 133:
3.8 Adding a New DRDA Host 3.8.1 DR
- Page 134 and 135:
3.9 Recommendations Our recommendat
- Page 136 and 137:
DataHub/2 Prerequisites: Installati
- Page 138 and 139:
associated with the local UPM user
- Page 140 and 141:
4.2 Scenario 1: Local Management of
- Page 142 and 143:
112 DataHub Implementation and Conn
- Page 144 and 145:
4.3 Scenario 2: Central Management
- Page 146 and 147:
116 DataHub Implementation and Conn
- Page 148 and 149:
4.4.1 Required Products Install the
- Page 150 and 151:
LAN Server Access Profile Tip Versi
- Page 152 and 153:
Figure 81. DH/2 Install: Feature Se
- Page 154 and 155:
124 DataHub Implementation and Conn
- Page 156 and 157:
126 DataHub Implementation and Conn
- Page 158 and 159:
Tuning versus Execution 128 DataHub
- Page 160 and 161:
NETBIOS: DataHub/2 flat files and e
- Page 162 and 163:
Table 14. NETBIOS Session Informati
- Page 164 and 165:
Figure 93. LAPS: Configure Workstat
- Page 166 and 167:
136 DataHub Implementation and Conn
- Page 168 and 169:
138 DataHub Implementation and Conn
- Page 170 and 171:
PROT_MAN DRIVERNAME = PROTMAN$ IBML
- Page 172 and 173:
configurations. Notice the differen
- Page 174 and 175:
4.4.7 DataHub/2 Database Connectivi
- Page 176 and 177:
4.6.2 Workload consideration if the
- Page 178 and 179:
4.7 Codepage Support 4.8 Recommenda
- Page 180 and 181:
150 DataHub Implementation and Conn
- Page 182 and 183:
5.1 Key Connectivity Parameters The
- Page 184 and 185:
5.2 The ITSC Network DB2 Subsystem
- Page 186 and 187:
Figure 110. DataHub/2: OS/2 Compone
- Page 188 and 189:
Recommendation A good naming conven
- Page 190 and 191:
In the Symbolic destination field,
- Page 192 and 193:
• Communications link • Partner
- Page 194 and 195:
1. Select the CPI Communications si
- Page 196 and 197:
5. Click on the OK push button when
- Page 198 and 199:
2. Verify that the system software
- Page 200 and 201:
DATAHUB.SMP.GLOBAL.CSI DATAHUB.V110
- Page 202 and 203:
STDB2AMQ JOB (999,POK), // ′ DATA
- Page 204 and 205:
174 DataHub Implementation and Conn
- Page 206 and 207:
Figure 131. VM Service Pool Environ
- Page 208 and 209:
SPM00000, SPM00001 The IDs of Servi
- Page 210 and 211:
Environment Configuration Overview
- Page 212 and 213:
182 DataHub Implementation and Conn
- Page 214 and 215:
184 DataHub Implementation and Conn
- Page 216 and 217:
186 DataHub Implementation and Conn
- Page 218 and 219:
3. The DataHub Support/VM CMR (CMR1
- Page 220 and 221:
Figure 145. DHS/VM Communication Fl
- Page 222 and 223:
5.6.2 Configuration Considerations
- Page 224 and 225:
The map file name and location are
- Page 226 and 227: 5.7.3 OS/2 Communications Manager D
- Page 228 and 229: Figure 150. Create a Transaction Pr
- Page 230 and 231: Figure 153. CM/2: Create Conversati
- Page 232 and 233: 5.8 Recommendations We recommend th
- Page 234 and 235: 6.2 DataHub/2 Workstation 204 DataH
- Page 236 and 237: When you open the log file, the pro
- Page 238 and 239: 6.2.3 OS/2 Communications Manager T
- Page 240 and 241: • Perform Trace − On the PWS pl
- Page 242 and 243: A DataHub user can request tracing
- Page 244 and 245: Abends All programs may abnormally
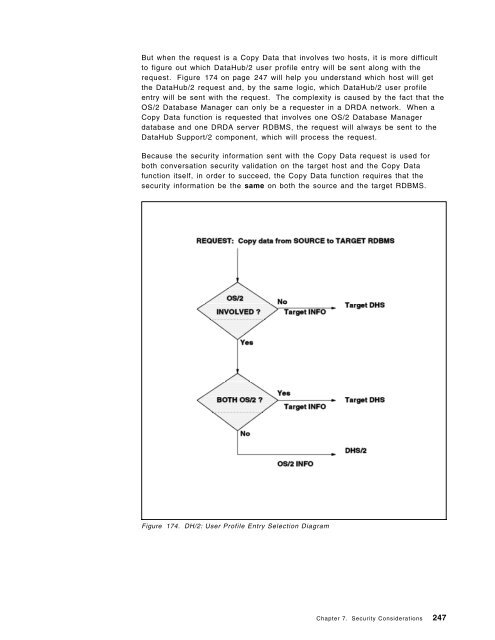
- Page 246 and 247: 216 DataHub Implementation and Conn
- Page 248 and 249: This can be very helpful when debug
- Page 250 and 251: When you receive any of these indic
- Page 252 and 253: 222 DataHub Implementation and Conn
- Page 254 and 255: eoccurrence is needed to get more i
- Page 256 and 257: 6.4 VM Host Problem Determination T
- Page 258 and 259: 6.4.3 Diagnosing Problems Statement
- Page 260 and 261: • A brief description of the prob
- Page 262 and 263: * Alert File Layout * *The set of r
- Page 264 and 265: 234 DataHub Implementation and Conn
- Page 266 and 267: Additional Message Information Page
- Page 268 and 269: To grant authority to any user, you
- Page 270 and 271: 240 DataHub Implementation and Conn
- Page 272 and 273: Before we explain what those domain
- Page 274 and 275: 244 DataHub Implementation and Conn
- Page 278 and 279: 7.1.3 DataHub/2 Database Privileges
- Page 280 and 281: Figure 175. DB2 Security Mechanism
- Page 282 and 283: Inbound Processing 1. LU Verificati
- Page 284 and 285: 7.4 AS/400 Security This section pr
- Page 286 and 287: DataHub Support/2 also uses one or
- Page 288 and 289: 258 DataHub Implementation and Conn
- Page 290 and 291: 260 DataHub Implementation and Conn
- Page 292 and 293: 262 DataHub Implementation and Conn
- Page 294 and 295: PARTNER_LU_ALIAS(DHNYCENT ) MODE_NA
- Page 296 and 297: ase product. A relational database
- Page 298 and 299: database catalog. A database table
- Page 300 and 301: F foreign key. A key that is specif
- Page 302 and 303: lib/obj*type lib/file(member) lib/f
- Page 304 and 305: OS/400. See Operating System/400. O
- Page 306 and 307: MVS A DB2 subsystem instance. VM An
- Page 308 and 309: operate even when connections to ot
- Page 310 and 311: U UNC. See universal naming convent
- Page 312 and 313: 282 DataHub Implementation and Conn
- Page 314 and 315: RU Request unit RUW Remote unit of
- Page 316 and 317: DataHub Support/VM (continued) conf
- Page 318 and 319: Q QEMQUSER collection 192 R RDB nam
- Page 321 and 322: ITSO Redbook Evaluation Internation
- Page 324: IBM ® Printed in U.S.A. GG24-4031-