Security analysis of Dutch smart metering systems - Multiple Choices
Security analysis of Dutch smart metering systems - Multiple Choices
Security analysis of Dutch smart metering systems - Multiple Choices
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
3.2 NTA 3 THEORETICAL ANALYSIS<br />
could be caused by a device on the bus that acts as a rogue master and tries to send commands<br />
to the slave devices on the bus. An example <strong>of</strong> a command that could be sent to a slave device is<br />
to close or open the valve <strong>of</strong> a gas or water meter.<br />
Master<br />
(listener)<br />
M-Bus<br />
device 1<br />
M-Bus<br />
device 2<br />
M-Bus<br />
device 3<br />
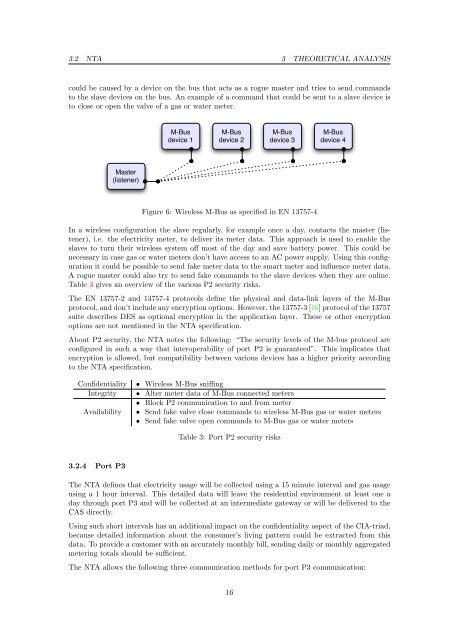
Figure 6: Wireless M-Bus as specified in EN 13757-4<br />
M-Bus<br />
device 4<br />
In a wireless configuration the slave regularly, for example once a day, contacts the master (listener),<br />
i.e. the electricity meter, to deliver its meter data. This approach is used to enable the<br />
slaves to turn their wireless system <strong>of</strong>f most <strong>of</strong> the day and save battery power. This could be<br />
necessary in case gas or water meters don’t have access to an AC power supply. Using this configuration<br />
it could be possible to send fake meter data to the <strong>smart</strong> meter and influence meter data.<br />
A rogue master could also try to send fake commands to the slave devices when they are online.<br />
Table 3 gives an overview <strong>of</strong> the various P2 security risks.<br />
The EN 13757-2 and 13757-4 protocols define the physical and data-link layers <strong>of</strong> the M-Bus<br />
protocol, and don’t include any encryption options. However, the 13757-3 [16] protocol <strong>of</strong> the 13757<br />
suite describes DES as optional encryption in the application layer. These or other encryption<br />
options are not mentioned in the NTA specification.<br />
About P2 security, the NTA notes the following: “The security levels <strong>of</strong> the M-bus protocol are<br />
configured in such a way that interoperability <strong>of</strong> port P2 is guaranteed”. This implicates that<br />
encryption is allowed, but compatibility between various devices has a higher priority according<br />
to the NTA specification.<br />
Confidentiality • Wireless M-Bus sniffing<br />
Integrity • Alter meter data <strong>of</strong> M-Bus connected meters<br />
• Block P2 communication to and from meter<br />
Availability • Send fake valve close commands to wireless M-Bus gas or water meters<br />
• Send fake valve open commands to M-Bus gas or water meters<br />
3.2.4 Port P3<br />
Table 3: Port P2 security risks<br />
The NTA defines that electricity usage will be collected using a 15 minute interval and gas usage<br />
using a 1 hour interval. This detailed data will leave the residential environment at least one a<br />
day through port P3 and will be collected at an intermediate gateway or will be delivered to the<br />
CAS directly.<br />
Using such short intervals has an additional impact on the confidentiality aspect <strong>of</strong> the CIA-triad,<br />
because detailed information about the consumer’s living pattern could be extracted from this<br />
data. To provide a customer with an accurately monthly bill, sending daily or monthly aggregated<br />
<strong>metering</strong> totals should be sufficient.<br />
The NTA allows the following three communication methods for port P3 communication:<br />
16