Security analysis of Dutch smart metering systems - Multiple Choices
Security analysis of Dutch smart metering systems - Multiple Choices
Security analysis of Dutch smart metering systems - Multiple Choices
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
4.4 Port P3 4 PRACTICAL ANALYSIS<br />
4.4.2 Practical research<br />
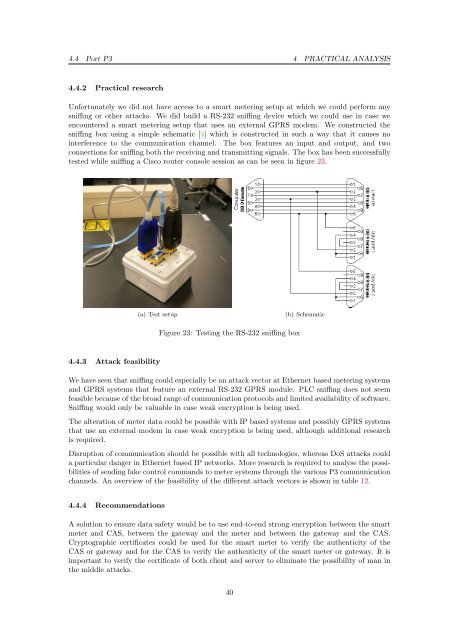
Unfortunately we did not have access to a <strong>smart</strong> <strong>metering</strong> setup at which we could perform any<br />
sniffing or other attacks. We did build a RS-232 sniffing device which we could use in case we<br />
encountered a <strong>smart</strong> <strong>metering</strong> setup that uses an external GPRS modem. We constructed the<br />
sniffing box using a simple schematic [4] which is constructed in such a way that it causes no<br />
interference to the communication channel. The box features an input and output, and two<br />
connections for sniffing both the receiving and transmitting signals. The box has been successfully<br />
tested while sniffing a Cisco router console session as can be seen in figure 23.<br />
4.4.3 Attack feasibility<br />
(a) Test setup (b) Schematic<br />
Figure 23: Testing the RS-232 sniffing box<br />
We have seen that sniffing could especially be an attack vector at Ethernet based <strong>metering</strong> <strong>systems</strong><br />
and GPRS <strong>systems</strong> that feature an external RS-232 GPRS module. PLC sniffing does not seem<br />
feasible because <strong>of</strong> the broad range <strong>of</strong> communication protocols and limited availability <strong>of</strong> s<strong>of</strong>tware.<br />
Sniffing would only be valuable in case weak encryption is being used.<br />
The alteration <strong>of</strong> meter data could be possible with IP based <strong>systems</strong> and possibly GPRS <strong>systems</strong><br />
that use an external modem in case weak encryption is being used, although additional research<br />
is required.<br />
Disruption <strong>of</strong> communication should be possible with all technologies, whereas DoS attacks could<br />
a particular danger in Ethernet based IP networks. More research is required to analyse the possibilities<br />
<strong>of</strong> sending fake control commands to meter <strong>systems</strong> through the various P3 communication<br />
channels. An overview <strong>of</strong> the feasibility <strong>of</strong> the different attack vectors is shown in table 12.<br />
4.4.4 Recommendations<br />
A solution to ensure data safety would be to use end-to-end strong encryption between the <strong>smart</strong><br />
meter and CAS, between the gateway and the meter and between the gateway and the CAS.<br />
Cryptographic certificates could be used for the <strong>smart</strong> meter to verify the authenticity <strong>of</strong> the<br />
CAS or gateway and for the CAS to verify the authenticity <strong>of</strong> the <strong>smart</strong> meter or gateway. It is<br />
important to verify the certificate <strong>of</strong> both client and server to eliminate the possibility <strong>of</strong> man in<br />
the middle attacks.<br />
40