Security analysis of Dutch smart metering systems - Multiple Choices
Security analysis of Dutch smart metering systems - Multiple Choices
Security analysis of Dutch smart metering systems - Multiple Choices
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
4.4 Port P3 4 PRACTICAL ANALYSIS<br />
mobile device registers itself at base station with at least an Access Point Name (APN) and its<br />
GPRS authentication credentials to get access to the GPRS network. An APN is a hostname<br />
which is associated with the GPRS connection and resolves to the Gateway GPRS Support Node<br />
(GGSN) that provides the connectivity between GPRS core network and the telecom operators<br />
or corporate router. This connectivity is <strong>of</strong>ten, but not necessarily, realized by means <strong>of</strong> a GRE<br />
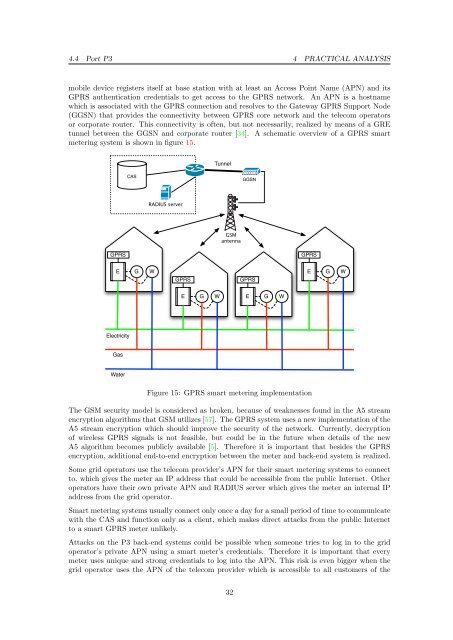
tunnel between the GGSN and corporate router [34]. A schematic overview <strong>of</strong> a GPRS <strong>smart</strong><br />
<strong>metering</strong> system is shown in figure 15.<br />
GPRS<br />
E G W<br />
Electricity<br />
Gas<br />
Water<br />
CAS<br />
RADIUS server<br />
GPRS<br />
E G W<br />
Tunnel<br />
GSM<br />
antenna<br />
GGSN<br />
GPRS<br />
E G W<br />
GPRS<br />
Figure 15: GPRS <strong>smart</strong> <strong>metering</strong> implementation<br />
E G W<br />
The GSM security model is considered as broken, because <strong>of</strong> weaknesses found in the A5 stream<br />
encryption algorithms that GSM utilizes [57]. The GPRS system uses a new implementation <strong>of</strong> the<br />
A5 stream encryption which should improve the security <strong>of</strong> the network. Currently, decryption<br />
<strong>of</strong> wireless GPRS signals is not feasible, but could be in the future when details <strong>of</strong> the new<br />
A5 algorithm becomes publicly available [5]. Therefore it is important that besides the GPRS<br />
encryption, additional end-to-end encryption between the meter and back-end system is realized.<br />
Some grid operators use the telecom provider’s APN for their <strong>smart</strong> <strong>metering</strong> <strong>systems</strong> to connect<br />
to, which gives the meter an IP address that could be accessible from the public Internet. Other<br />
operators have their own private APN and RADIUS server which gives the meter an internal IP<br />
address from the grid operator.<br />
Smart <strong>metering</strong> <strong>systems</strong> usually connect only once a day for a small period <strong>of</strong> time to communicate<br />
with the CAS and function only as a client, which makes direct attacks from the public Internet<br />
to a <strong>smart</strong> GPRS meter unlikely.<br />
Attacks on the P3 back-end <strong>systems</strong> could be possible when someone tries to log in to the grid<br />
operator’s private APN using a <strong>smart</strong> meter’s credentials. Therefore it is important that every<br />
meter uses unique and strong credentials to log into the APN. This risk is even bigger when the<br />
grid operator uses the APN <strong>of</strong> the telecom provider which is accessible to all customers <strong>of</strong> the<br />
32