ADMIN
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
PAM and Hardware<br />
Nuts and Bolts<br />
Figure 1: PAM provides a centralized user management framework for the<br />
application.<br />
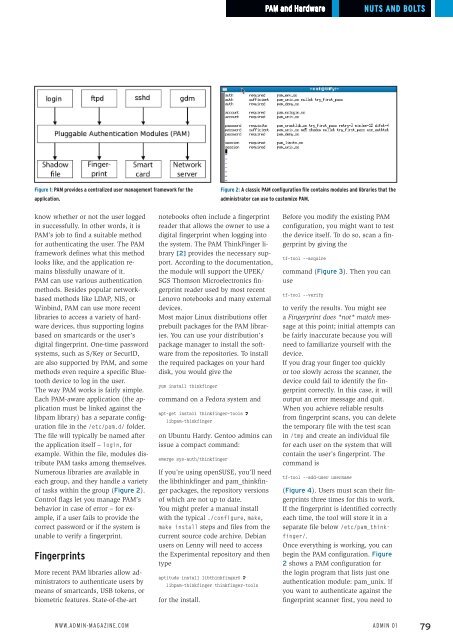
Figure 2: A classic PAM configuration file contains modules and libraries that the<br />
administrator can use to customize PAM.<br />
know whether or not the user logged<br />
in successfully. In other words, it is<br />
PAM’s job to find a suitable method<br />
for authenticating the user. The PAM<br />
framework defines what this method<br />
looks like, and the application remains<br />
blissfully unaware of it.<br />
PAM can use various authentication<br />
methods. Besides popular networkbased<br />
methods like LDAP, NIS, or<br />
Winbind, PAM can use more recent<br />
libraries to access a variety of hardware<br />
devices, thus supporting logins<br />
based on smartcards or the user’s<br />
digital fingerprint. One-time password<br />
systems, such as S/Key or SecurID,<br />
are also supported by PAM, and some<br />
methods even require a specific Bluetooth<br />
device to log in the user.<br />
The way PAM works is fairly simple.<br />
Each PAM-aware application (the application<br />
must be linked against the<br />
libpam library) has a separate configuration<br />
file in the /etc/pam.d/ folder.<br />
The file will typically be named after<br />
the application itself – login, for<br />
example. Within the file, modules distribute<br />
PAM tasks among themselves.<br />
Numerous libraries are available in<br />
each group, and they handle a variety<br />
of tasks within the group (Figure 2).<br />
Control flags let you manage PAM’s<br />
behavior in case of error – for example,<br />
if a user fails to provide the<br />
correct password or if the system is<br />
unable to verify a fingerprint.<br />
Fingerprints<br />
More recent PAM libraries allow administrators<br />
to authenticate users by<br />
means of smartcards, USB tokens, or<br />
biometric features. State-of-the-art<br />
notebooks often include a fingerprint<br />
reader that allows the owner to use a<br />
digital fingerprint when logging into<br />
the system. The PAM ThinkFinger library<br />
[2] provides the necessary support.<br />
According to the documentation,<br />
the module will support the UPEK/<br />
SGS Thomson Microelectronics fingerprint<br />
reader used by most recent<br />
Lenovo notebooks and many external<br />
devices.<br />
Most major Linux distributions offer<br />
prebuilt packages for the PAM libraries.<br />
You can use your distribution’s<br />
package manager to install the software<br />
from the repositories. To install<br />
the required packages on your hard<br />
disk, you would give the<br />
yum install thinkfinger<br />
command on a Fedora system and<br />
apt‐get install thinkfinger‐tools U<br />
libpam‐thinkfinger<br />
on Ubuntu Hardy. Gentoo admins can<br />
issue a compact command:<br />
emerge sys‐auth/thinkfinger<br />
If you’re using openSUSE, you’ll need<br />
the libthinkfinger and pam_thinkfinger<br />
packages, the repository versions<br />
of which are not up to date.<br />
You might prefer a manual install<br />
with the typical ./configure, make,<br />
make install steps and files from the<br />
current source code archive. Debian<br />
users on Lenny will need to access<br />
the Experimental repository and then<br />
type<br />
aptitude install libthinkfinger0 U<br />
libpam‐thinkfinger thinkfinger‐tools<br />
for the install.<br />
Before you modify the existing PAM<br />
configuration, you might want to test<br />
the device itself. To do so, scan a fingerprint<br />
by giving the<br />
tf‐tool ‐‐acquire<br />
command (Figure 3). Then you can<br />
use<br />
tf‐tool ‐‐verify<br />
to verify the results. You might see<br />
a Fingerprint does *not* match message<br />
at this point; initial attempts can<br />
be fairly inaccurate because you will<br />
need to familiarize yourself with the<br />
device.<br />
If you drag your finger too quickly<br />
or too slowly across the scanner, the<br />
device could fail to identify the fingerprint<br />
correctly. In this case, it will<br />
output an error message and quit.<br />
When you achieve reliable results<br />
from fingerprint scans, you can delete<br />
the temporary file with the test scan<br />
in /tmp and create an individual file<br />
for each user on the system that will<br />
contain the user’s fingerprint. The<br />
command is<br />
tf‐tool ‐‐add‐user username<br />
(Figure 4). Users must scan their fingerprints<br />
three times for this to work.<br />
If the fingerprint is identified correctly<br />
each time, the tool will store it in a<br />
separate file below /etc/pam_thinkfinger/.<br />
Once everything is working, you can<br />
begin the PAM configuration. Figure<br />
2 shows a PAM configuration for<br />
the login program that lists just one<br />
authentication module: pam_unix. If<br />
you want to authenticate against the<br />
fingerprint scanner first, you need to<br />
www.admin-magazine.com<br />
Admin 01<br />
79