ADMIN+Magazine+Sample+PDF
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Nuts and Bolts<br />
PAM and Hardware<br />
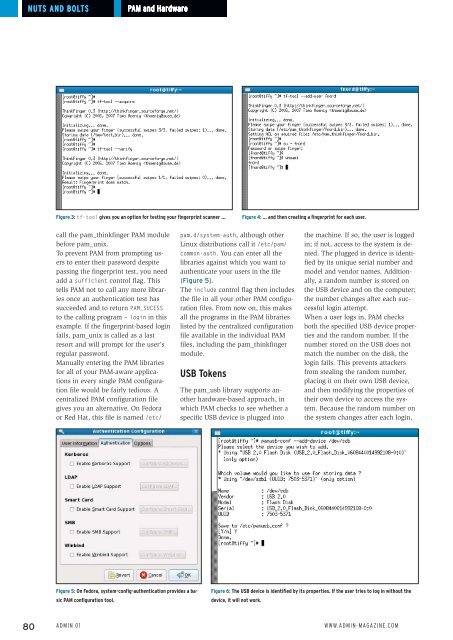
Figure 3: tf-tool gives you an option for testing your fingerprint scanner …<br />
Figure 4: … and then creating a fingerprint for each user.<br />
call the pam_thinkfinger PAM module<br />
before pam_unix.<br />
To prevent PAM from prompting users<br />
to enter their password despite<br />
passing the fingerprint test, you need<br />
add a sufficient control flag. This<br />
tells PAM not to call any more libraries<br />
once an authentication test has<br />
succeeded and to return PAM_SUCESS<br />
to the calling program – login in this<br />
example. If the fingerprint-based login<br />
fails, pam_unix is called as a last<br />
resort and will prompt for the user’s<br />
regular password.<br />
Manually entering the PAM libraries<br />
for all of your PAM-aware applications<br />
in every single PAM configuration<br />
file would be fairly tedious. A<br />
centralized PAM configuration file<br />
gives you an alternative. On Fedora<br />
or Red Hat, this file is named /etc/<br />
pam.d/system‐auth, although other<br />
Linux distributions call it /etc/pam/<br />
common‐auth. You can enter all the<br />
libraries against which you want to<br />
authenticate your users in the file<br />
(Figure 5).<br />
The include control flag then includes<br />
the file in all your other PAM configuration<br />
files. From now on, this makes<br />
all the programs in the PAM libraries<br />
listed by the centralized configuration<br />
file available in the individual PAM<br />
files, including the pam_thinkfinger<br />
module.<br />
USB Tokens<br />
The pam_usb library supports another<br />
hardware-based approach, in<br />
which PAM checks to see whether a<br />
specific USB device is plugged into<br />
the machine. If so, the user is logged<br />
in; if not, access to the system is denied.<br />
The plugged in device is identified<br />
by its unique serial number and<br />
model and vendor names. Additionally,<br />
a random number is stored on<br />
the USB device and on the computer;<br />
the number changes after each successful<br />
login attempt.<br />
When a user logs in, PAM checks<br />
both the specified USB device properties<br />
and the random number. If the<br />
number stored on the USB does not<br />
match the number on the disk, the<br />
login fails. This prevents attackers<br />
from stealing the random number,<br />
placing it on their own USB device,<br />
and then modifying the properties of<br />
their own device to access the system.<br />
Because the random number on<br />
the system changes after each login,<br />
Figure 5: On Fedora, system‐config‐authentication provides a basic<br />
PAM configuration tool.<br />
Figure 6: The USB device is identified by its properties. If the user tries to log in without the<br />
device, it will not work.<br />
80 Admin 01 www.admin-magazine.com