Design and Implementation of TinyGALS: A Programming Model for ...
Design and Implementation of TinyGALS: A Programming Model for ...
Design and Implementation of TinyGALS: A Programming Model for ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
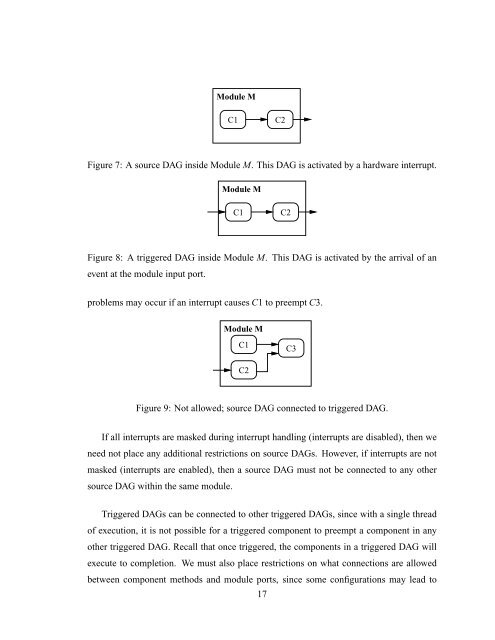
Module M<br />
C1 C2<br />
Figure 7: A source DAG inside Module M. This DAG is activated by a hardware interrupt.<br />
Module M<br />
C1 C2<br />
Figure 8: A triggered DAG inside Module M. This DAG is activated by the arrival <strong>of</strong> an<br />
event at the module input port.<br />
problems may occur if an interrupt causes C1 to preempt C3.<br />
Module M<br />
C1<br />
C2<br />
Figure 9: Not allowed; source DAG connected to triggered DAG.<br />
If all interrupts are masked during interrupt h<strong>and</strong>ling (interrupts are disabled), then we<br />
need not place any additional restrictions on source DAGs. However, if interrupts are not<br />
masked (interrupts are enabled), then a source DAG must not be connected to any other<br />
source DAG within the same module.<br />
Triggered DAGs can be connected to other triggered DAGs, since with a single thread<br />
<strong>of</strong> execution, it is not possible <strong>for</strong> a triggered component to preempt a component in any<br />
other triggered DAG. Recall that once triggered, the components in a triggered DAG will<br />
execute to completion. We must also place restrictions on what connections are allowed<br />
between component methods <strong>and</strong> module ports, since some configurations may lead to<br />
17<br />
C3