BLOCKING READER: DESIGN AND IMPLEMENTATION OF A ...
BLOCKING READER: DESIGN AND IMPLEMENTATION OF A ...
BLOCKING READER: DESIGN AND IMPLEMENTATION OF A ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
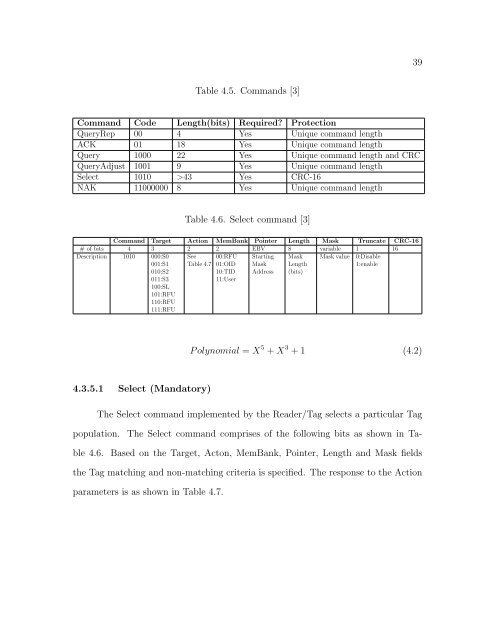
Table 4.5. Commands [3]<br />
Command Code Length(bits) Required? Protection<br />
QueryRep 00 4 Yes Unique command length<br />
ACK 01 18 Yes Unique command length<br />
Query 1000 22 Yes Unique command length and CRC<br />
QueryAdjust 1001 9 Yes Unique command length<br />
Select 1010 >43 Yes CRC-16<br />
NAK 11000000 8 Yes Unique command length<br />
Table 4.6. Select command [3]<br />
Command Target Action MemBank Pointer Length Mask Truncate CRC-16<br />
# of bits 4 3 2 2 EBV 8 variable 1 16<br />
Description 1010 000:S0 See 00:RFU Starting Mask Mask value 0:Disable<br />
001:S1 Table 4.7 01:OID Mask Length<br />
1:enable<br />
010:S2<br />
10:TID Address (bits)<br />
011:S3<br />
100:SL<br />
101:RFU<br />
110:RFU<br />
111:RFU<br />
11:User<br />
4.3.5.1 Select (Mandatory)<br />
P olynomial = X 5 + X 3 + 1 (4.2)<br />
The Select command implemented by the Reader/Tag selects a particular Tag<br />
population. The Select command comprises of the following bits as shown in Ta-<br />
ble 4.6. Based on the Target, Acton, MemBank, Pointer, Length and Mask fields<br />
the Tag matching and non-matching criteria is specified. The response to the Action<br />
parameters is as shown in Table 4.7.<br />
39