Evaluating A Selection of Tools for Extraction of Forensic Data: Disk ...
Evaluating A Selection of Tools for Extraction of Forensic Data: Disk ...
Evaluating A Selection of Tools for Extraction of Forensic Data: Disk ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
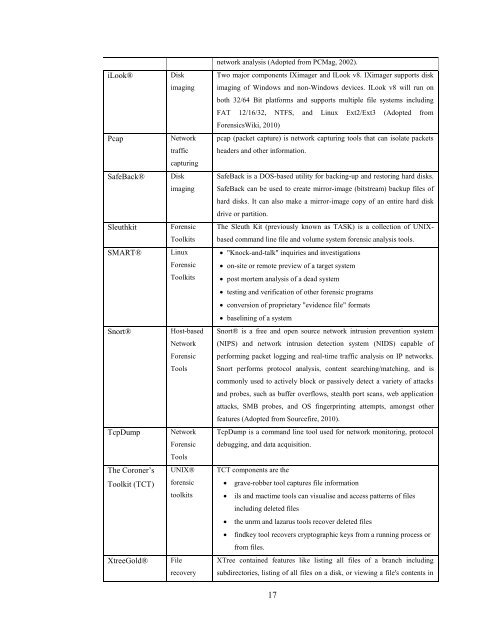
iLook® <strong>Disk</strong><br />
imaging<br />
Pcap Network<br />
traffic<br />
SafeBack® <strong>Disk</strong><br />
capturing<br />
imaging<br />
Sleuthkit <strong>Forensic</strong><br />
Toolkits<br />
SMART® Linux<br />
<strong>Forensic</strong><br />
Toolkits<br />
Snort® Host-based<br />
Network<br />
<strong>Forensic</strong><br />
<strong>Tools</strong><br />
TcpDump Network<br />
The Coroner‟s<br />
Toolkit (TCT)<br />
<strong>Forensic</strong><br />
<strong>Tools</strong><br />
UNIX®<br />
<strong>for</strong>ensic<br />
toolkits<br />
XtreeGold® File<br />
recovery<br />
network analysis (Adopted from PCMag, 2002).<br />
Two major components IXimager and ILook v8. IXimager supports disk<br />
imaging <strong>of</strong> Windows and non-Windows devices. ILook v8 will run on<br />
both 32/64 Bit plat<strong>for</strong>ms and supports multiple file systems including<br />
FAT 12/16/32, NTFS, and Linux Ext2/Ext3 (Adopted from<br />
<strong>Forensic</strong>sWiki, 2010)<br />
pcap (packet capture) is network capturing tools that can isolate packets<br />
headers and other in<strong>for</strong>mation.<br />
SafeBack is a DOS-based utility <strong>for</strong> backing-up and restoring hard disks.<br />
SafeBack can be used to create mirror-image (bitstream) backup files <strong>of</strong><br />
hard disks. It can also make a mirror-image copy <strong>of</strong> an entire hard disk<br />
drive or partition.<br />
The Sleuth Kit (previously known as TASK) is a collection <strong>of</strong> UNIX-<br />
based command line file and volume system <strong>for</strong>ensic analysis tools.<br />
"Knock-and-talk" inquiries and investigations<br />
on-site or remote preview <strong>of</strong> a target system<br />
post mortem analysis <strong>of</strong> a dead system<br />
testing and verification <strong>of</strong> other <strong>for</strong>ensic programs<br />
conversion <strong>of</strong> proprietary "evidence file" <strong>for</strong>mats<br />
baselining <strong>of</strong> a system<br />
Snort® is a free and open source network intrusion prevention system<br />
(NIPS) and network intrusion detection system (NIDS) capable <strong>of</strong><br />
per<strong>for</strong>ming packet logging and real-time traffic analysis on IP networks.<br />
Snort per<strong>for</strong>ms protocol analysis, content searching/matching, and is<br />
commonly used to actively block or passively detect a variety <strong>of</strong> attacks<br />
and probes, such as buffer overflows, stealth port scans, web application<br />
attacks, SMB probes, and OS fingerprinting attempts, amongst other<br />
features (Adopted from Sourcefire, 2010).<br />
TcpDump is a command line tool used <strong>for</strong> network monitoring, protocol<br />
debugging, and data acquisition.<br />
TCT components are the<br />
grave-robber tool captures file in<strong>for</strong>mation<br />
ils and mactime tools can visualise and access patterns <strong>of</strong> files<br />
including deleted files<br />
the unrm and lazarus tools recover deleted files<br />
findkey tool recovers cryptographic keys from a running process or<br />
from files.<br />
XTree contained features like listing all files <strong>of</strong> a branch including<br />
subdirectories, listing <strong>of</strong> all files on a disk, or viewing a file's contents in<br />
17