A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
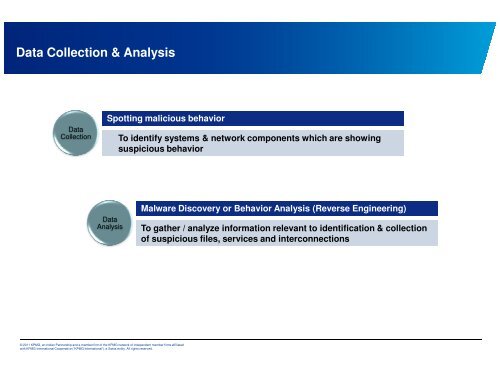
Data Collecti<strong>on</strong> & Analysis<br />
Data<br />
Collecti<strong>on</strong><br />
Spotting malicious behavior<br />
Data<br />
Analysis<br />
© 2011 KPMG, an Indian Partnership and a member firm of the KPMG network of independent member firms affiliated<br />
with KPMG Internati<strong>on</strong>al Cooperative (“KPMG Internati<strong>on</strong>al”), a Swiss entity. All rights reserved.<br />
To identify systems & network comp<strong>on</strong>ents which are showing<br />
suspicious behavior<br />
Malware Discovery or Behavior Analysis (<strong>Reverse</strong> <strong>Engineering</strong>)<br />
To gather / analyze informati<strong>on</strong> relevant to identificati<strong>on</strong> & collecti<strong>on</strong><br />
of suspicious files, services and interc<strong>on</strong>necti<strong>on</strong>s