A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
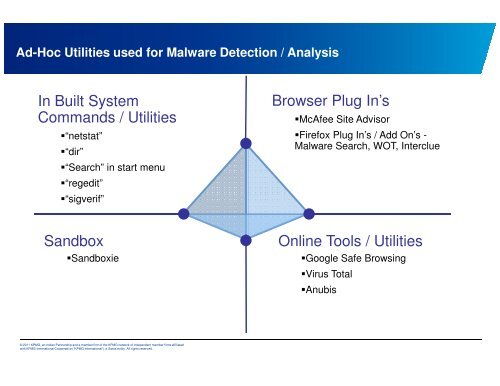
Ad-Hoc Utilities used for Malware Detecti<strong>on</strong> / Analysis<br />
In Built System<br />
Commands / Utilities<br />
�“netstat”<br />
�“dir”<br />
�“Search” in start menu<br />
�“regedit”<br />
�“sigverif”<br />
Sandbox<br />
�Sandboxie<br />
© 2011 KPMG, an Indian Partnership and a member firm of the KPMG network of independent member firms affiliated<br />
with KPMG Internati<strong>on</strong>al Cooperative (“KPMG Internati<strong>on</strong>al”), a Swiss entity. All rights reserved.<br />
Browser Plug In’s<br />
�McAfee Site Advisor<br />
�Firefox Plug In’s / Add On’s -<br />
Malware Search, WOT, Interclue<br />
Online Tools / Utilities<br />
�Google Safe Browsing<br />
�Virus Total<br />
�Anubis