A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
A Primer on Reverse Engineering Malwares
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Behavior Analysis<br />
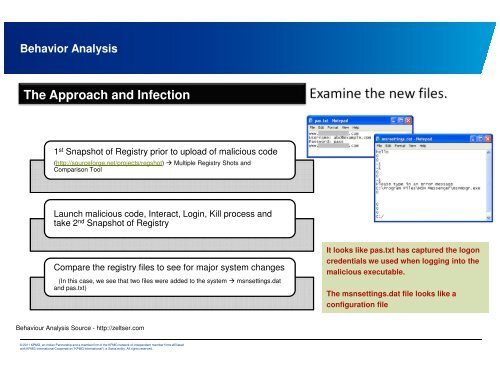
The Approach and Infecti<strong>on</strong><br />
1 st Snapshot of Registry prior to upload of malicious code<br />
(http://sourceforge.net/projects/regshot) � Multiple Registry Shots and<br />
Comparis<strong>on</strong> Tool<br />
Launch malicious code, Interact, Login, Kill process and<br />
take 2 nd Snapshot of Registry<br />
Compare the registry files to see for major system changes<br />
(In this case, we see that two files were added to the system � msnsettings.dat<br />
and pas.txt)<br />
Behaviour Analysis Source - http://zeltser.com<br />
© 2011 KPMG, an Indian Partnership and a member firm of the KPMG network of independent member firms affiliated<br />
with KPMG Internati<strong>on</strong>al Cooperative (“KPMG Internati<strong>on</strong>al”), a Swiss entity. All rights reserved.<br />
It looks like pas.txt has captured the log<strong>on</strong><br />
credentials we used when logging into the<br />
malicious executable.<br />
The msnsettings.dat file looks like a<br />
c<strong>on</strong>figurati<strong>on</strong> file